S 1.12 Archiving
Description
Imaging business processes and documents in electronic documents requires suitable storage of the generated data for later usage, finding, and processing of the data. This refers both to datasets and electronic representations of paper business documents and vouchers. Permanent and immutable storage of electronic documents and other data is referred to as archiving.
Archiving must be deemed a part of the document management process. Along with generating, processing, and managing electronic documents, permanent storage (archiving) plays a special role, because it is normally expected that the documents will be available until expiration of a specified retention period on the one hand, and that their confidentiality and integrity will be maintained on the other hand. Electronic documents may also be required to be available for an unlimited period.
The technical design of this process is performed using document management and archive systems (see figure). This module only refers to electronic archive systems.
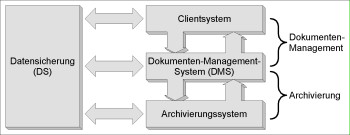
Figure: Technical design of archiving using document management and archiving systems
The scope of implementation options of such an archive system includes:
- small-scale archive systems, e.g. consisting of an archive server with connected mass storage (e.g. hard disk or jukebox), up to
- complex, possibly widely distributed archive systems for organisation-wide archiving of relevant business data, consisting of:
- central archive server components with RAID systems, jukeboxes, or the connection to storage area networks (SAN) for the central storage of files,
- WORM media for the audit-proof, immutable storage of data,
- components for indexing files, research, and for converting storage formats (rendition),
- local cache servers for the quick access to frequently needed data,
- client software allowing for direct access to archive data (e.g. also from Office applications).
It is appropriate to delimit electronic archives regarding data backup systems. Copies of the system and usage data are generated during data backup. In this, the backed up data is stored in such a way that it is physically separated from the IT system and protected against hazards. On the contrary, electronic archives are regularly integrated into running system operations. Here, large amounts of usage data (electronic documents) are normally stored, which can be retrieved at any time from the electronic archive system. If designed specifically (e.g. redundant design of the storage components and the corresponding spatial arrangement), larger archive systems may partially assume the data backup functionality (for the usage data).
This module is intended to illustrate a systematic method for creating a concept for electronic archiving and how the design of an archive system and its integration can be ensured in a company and/or government agency. The time and effort required for the creation and implementation of such a concept are considerable. This module should always be applied if the data to be archived is relevant to the government agency and/or company in the long term.
Threat scenario
The following typical threats are assumed within the framework of IT-Grundschutz for the archive systems to be taken into consideration during electronic archiving, as well as the related organisational processes.
Force Majeure
| T 1.2 | Failure of the IT system |
| T 1.7 | Inadmissible temperature and humidity |
| T 1.9 | Loss of data due to intensive magnetic fields |
| T 1.14 | Loss of data due to strong light |
Organisational Shortcomings
| T 2.7 | Unauthorised use of rights |
| T 2.72 | Inadequate migration of archive systems |
| T 2.73 | Inadequate audit trail of archive systems |
| T 2.74 | Inadequate indexing keys for archives |
| T 2.75 | Inadequate capacity of archival storage media |
| T 2.76 | Inadequate documentation of archive accesses |
| T 2.77 | Ineffectual transfer of paper data to electronic archives |
| T 2.78 | Ineffectual regeneration of data stocks during archiving |
| T 2.79 | Ineffectual regeneration of digital signatures during archiving |
| T 2.80 | Ineffectual auditing of archiving procedures |
| T 2.81 | Ineffectual destruction of data media during archiving |
| T 2.82 | Poor planning of the archive system location |
Human Error
| T 3.1 | Loss of data confidentiality or integrity as a result of user error |
| T 3.16 | Incorrect administration of site and data access rights |
| T 3.35 | Disabling the server while in operation |
| T 3.54 | Use of unsuitable data media for archiving |
| T 3.55 | Violation of legal requirements regarding the use of archive systems |
Technical Failure
| T 4.7 | Defective data media |
| T 4.13 | Loss of stored data |
| T 4.20 | Overloaded information systems |
| T 4.26 | Failure of a database |
| T 4.30 | Loss of database integrity/consistency |
| T 4.31 | Failure or malfunction of a network component |
| T 4.45 | Delayed access to archive information |
| T 4.46 | Poor synchronisation of index data during archiving |
| T 4.47 | Obsolescence of cryptomethods |
Deliberate Acts
| T 5.2 | Manipulation of information or software |
| T 5.6 | Attack |
| T 5.29 | Unauthorised copying of data media |
| T 5.82 | Manipulation of a cryptomodule |
| T 5.83 | Compromising cryptographic keys |
| T 5.85 | Loss of integrity of information that should be protected |
| T 5.102 | Sabotage |
| T 5.105 | Disruption of archive system services |
| T 5.106 | Unauthorised overwriting or deletion of archiving media |
Method recommendation
To secure the information system examined, other modules must be implemented in addition to this module, with these modules being selected based on the results of the IT-Grundschutz modelling process.
Furthermore, the approach described below is recommended for implementing and operating electronic archive systems. During the planning phase, it must be taken into account that the archive systems and archiving media used will become obsolete from a technological and physical point of view over the course of time. Therefore, the planning and implementation/operation phases are followed by a migration phase where the existing archive system or parts thereof is/are replaced by new technologies and components. The migration phase also includes the conversion of the archived data and documents into data formats used in the future.
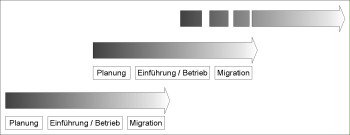
Figure: Planning of migration steps during archiving system planning
The individual phases and the safeguards to be implemented in these phases are explained briefly in the following.
1. Planning phase
In the planning phase, the objective related to the use of the archive system must be formulated (see S 2.242 Electronic archiving objectives). Here, the relevant organisational, legal, and technical requirements must be determined, including an assessment as to how the requirements will develop during the expected service life of the archive system to be implemented (see S 2.244, S 2.245, and S 2.246). The results must be documented in an archiving concept (see S 2.243).
2. Implementation and operation
When implementing an archive system, a system meeting the determined requirements must first be selected. Furthermore, the installation location of the system and the storage location of the archiving media must be defined (see S 4.168, S 4.169, S 4.170, S 1.59, S 1.60).
Along with the archive system as such, a suitable superior document management system must be implemented in order to manage the archive contents (see S 2.258, S 2.259).
Regulations regarding the use of the archive system and regarding the use of digital signatures must be defined and the Administrators and users must be trained (see S 2.262, S 2.265, S 3.34, S 3.35).
In order to ensure the correctness in the long term, the archiving process must be monitored continuously and checked for correctness. Furthermore, it must be ensured that sufficient media are available for archiving at any given time (see S 2.257, S 2.260 S 2.263, S 4.171, S 4.172, S 4.173, S 6.84).
Depending on the specifically used archive software, the safeguards described in module S 5.7 Databases must also be implemented.
3. Migration phase
The migration phase is often triggered by the following events, for example:
- There was a technology change regarding system components or data formats, which is why the developments in this area should be surveyed (see S 2.261 Regular market surveys of archive systems).
- System components, particularly data media, are obsolete and must be replaced by new ones (see S 2.266 Regular replacement of technical archive system components).
- The usage criteria for the archive system changed.
- Cryptographic procedures, products, and/or keys must be replaced by new ones (see S 2.264 Regular regeneration of encrypted data in archiving).
In the following, the bundle of measures regarding the use of electronic archive systems is presented.
Planning and design
| S 2.242 | (A) | Electronic archiving objectives |
| S 2.243 | (A) | Development of an archiving concept |
| S 2.244 | (A) | Determination of the technical influencing factors for electronic archiving |
| S 2.245 | (A) | Determination of the legal influencing factors for electronic archiving |
| S 2.246 | (A) | Determination of the organisational influencing factors for electronic archiving |
| S 2.259 | (Z) | Introduction of a high-level document management system |
| S 2.262 | (A) | Control of archive system usage |
| S 2.265 | (Z) | Proper use of digital signatures in archiving |
Purchasing
| S 4.168 | (B) | Selection of a suitable archive system |
| S 4.169 | (B) | Use of appropriate archival media |
| S 4.170 | (B) | Selection of suitable data formats for the archival storage of documents |
Implementation
| S 1.59 | (A) | Suitable siting of archive systems |
| S 2.266 | (C) | Regular replacement of technical archive system components |
| S 3.34 | (A) | Basic training on the administration of the archive system |
| S 3.35 | (A) | Basic user training on how to use the archive system |
Operation
| S 1.60 | (A) | Appropriate storage of archiving media |
| S 2.257 | (C) | Monitoring of the memory resources of archiving media |
| S 2.258 | (A) | Consistent indexing of documents during archiving |
| S 2.260 | (B) | Regular auditing of the archiving procedure |
| S 2.261 | (B) | Regular market surveys of archive systems |
| S 2.263 | (A) | Regular regeneration of archived data resources |
| S 2.264 | (B) | Regular regeneration of encrypted data in archiving |
| S 4.171 | (A) | Protection of the integrity of the archive system index database |
| S 4.172 | (C) | Logging of the archival accesses |
| S 4.173 | (B) | Regular function and recovery tests for archiving |
Contingency Planning
| S 6.84 | (A) | Regular data backup of the system and archived data |

