1 IT-Grundschutz - The basis for information security
1.1 Why is information security important?

Information constitutes an essential asset for companies and government agencies and so requires adequate protection. Today, the majority of information is at least partially generated, stored, transported, or processed further with the help of information technology (IT). State-of-the-art business processes in the fields of economy and administration without IT support are no longer imaginable today. A reliably working information processing system is as indispensable for maintaining operations as the related technology. Inadequately protected information is a frequently underestimated risk factor that can threaten the existence of some organisations. At the same time, reasonable information protection and basic IT protection can be achieved with relatively modest resources.
With the IT-Grundschutz, the BSI offers a simple method for appropriately protecting all an organisation's information. With a combination of the IT-Grundschutz approach in BSI standard 100-2 and the IT-Grundschutz Catalogues, the BSI provides both a collection of security safeguards and a corresponding methodology for selecting and adapting suitable safeguards for safe handling of information for most different application environments.
Nowadays, almost all business processes and specialised tasks are controlled electronically. These processes and tasks store large amounts of information digitally, process it electronically, and transmit it in local and global networks, as well as in private and public networks. Many tasks and projects in the public or private sector cannot be implemented at all or can only be implemented in part without IT. As a result, many administrative and business organisations depend on the correct operation of the IT used. The corresponding goals of government agencies and companies can only be achieved when their IT is used properly and securely.
As the level of dependency on IT increases, the potential damage to society caused by a failure of information technology also increases accordingly. Since IT systems are never completely free of vulnerabilities, there is a justifiably great interest regarding the protection of the data and information processed by the IT and regarding the processes of planning, implementing, and monitoring their security. Here, it is important to not to only focus on the security of IT systems, because information security is not only a question of technology, but also greatly depends on the organisational and personnel boundary conditions. The security of the operating environment, the reliability of services, proper handling of the information to be protected, and many other important aspects must not be neglected.
Deficiencies in the field of information technology may cause significant problems. The potential damage can be assigned to different categories.
- Loss of availability If basic information is not present, this is most often noticed quickly when tasks cannot be continued in the absence of this information. If an IT system is down, financial transactions cannot be executed, online orders cannot be placed, and production processes come to a halt, for example. However, even just limiting the availability of certain information can result in impairments of the processes of an organisation.
- Loss of confidentiality of information: Each citizen wants his/her personal data to be treated confidentially. Each company knows that the competition is interested in internal, confidential data about turnover, marketing, research, and development. The accidental disclosure of information may cause serious damage in many areas.
- Loss of integrity (correctness of the information): Falsified or manipulated data may cause erroneous bookings, incorrect deliveries, or faulty products, for example. Over the last few years, the loss of data authenticity as a component of data integrity has become increasingly important: Data is assigned to the wrong person. For example, payment instructions or orders could be processed to the account of a third person, inadequately secured digital declarations of intent could be associated with the wrong persons, or someone’s "digital identity" could be forged.
Information and communication technology plays an important role in more and more areas of daily life, with a consistently high speed of innovation over the past few years. The following developments are particularly worth mentioning:
- Increasing degree of networking: Today, humans, but also IT systems, no longer operate isolated from each other and are in fact becoming increasingly networked. Networking allows access to shared databases and use of intensive forms of cooperation across geographic, political, or institutional boundaries. The result is not only dependence on the individual IT systems, but also a high level of dependence on the data networks. This in turn means that security deficiencies may quickly have global effects.
- IT distribution and penetration: More and more areas are supported by information technology, often without this support even being noticed. The necessary hardware is becoming increasingly compact and inexpensive so that small and miniature IT units can be integrated into all aspects of daily life. For example, there are jackets with integrated PDAs, RFIDs for controlling the flow of visitors or goods, and IT-based sensors in cars in order to be able to automatically adjust to changes in the environment. The various IT components increasingly communicate with each other using wireless connections. This way, even everyday objects can be localised and controlled via the internet.
- Disappearance of network borders: Until recently, it was possible to clearly limit business processes and applications to specific IT systems and the communication routes between these systems. Likewise, it was also possible to determine where the systems were located and to which organisation they belonged. Due to globalisation and the increasing use of wireless and spontaneous communication, this line is becoming more and more blurred.
- Attacks occur faster: The best way to prevent computer viruses, Trojan horses, or other attacks to IT systems, application programs, and protocols is to obtain the most recent information on security gaps and how to eliminate them, e.g. by installing patches or updates. However, the time between the announcement of a security gap and the first targeted large-scale attacks is constantly decreasing, which means it is becoming more and more important to have a well-staffed information security management team and a warning system.
- Higher interactivity of applications: Under the heading Web 2.0, previously existing technologies are combined in order to create new application and use models this way. This includes the most diverse fields of application such as new, social communication platforms, portals for the joint use of information, photos, and videos, or interactive web applications. Due to the increased integration of user feedback, information is not only distributed faster, but it is also more difficult to control its disclosure.
- Responsibility of the users: The best technology and quickest elimination of security gaps do not result in sufficient information security, unless humans are considered as a risk factor in so doing. This is not only about being able to identify security-critical situations, but also about the responsible behaviour of the individual. For this, it is necessary to dispose of knowledge regarding security gaps and codes of conduct.
Given the above-mentioned potential threats and the increasing dependence on IT, each organisation, regardless of whether it is a company or a government agency, must ask itself the following key questions relating to IT security:
- How carefully is business-relevant information handled?
- How secure is the information technology of the organisation?
- Which security safeguards need to be adopted?
- How do these safeguards need to be implemented specifically?
- How does the organisation maintain and/or improve the level of security attained?
- Are the personnel aspects of information security taken into consideration sufficiently?
- What is the level of security of other organisations the organisation cooperates with?
- Is there a contingency plan in order to be able to react quickly in the event of a threat?
When searching for answers to these questions, it must be taken into consideration that information security is a combination of technical, organisational, personnel, and structural/infrastructural aspects. It makes sense to introduce an information security management team designing, coordinating, and monitoring the tasks related to information security.
When comparing the business processes, applications, and IT systems of all organisations regarding the questions raised above, a special group would emerge. The approaches and IT systems in this group can be characterised as follows:
- The approaches and IT systems are typical, meaning that they are not individual solutions, but rather commonly used.
- The protection requirements of the information in terms of confidentiality, integrity, and availability are
- within the normal range.
- The approaches and IT systems are subject to the usual general conditions and are therefore exposed to typical basic threats and hazards.
If it were possible to identify the common denominator of all required security safeguards for this group of "typical" business processes, applications, and IT systems, i.e. the standard security safeguards, this would make answering the questions raised above for these "typical" application cases much easier. Areas outside of this group, regardless of whether they are rare, custom solutions, or IT systems with high protection requirements, can be based on the standard security safeguards, but will ultimately need to be examined individually.
The IT-Grundschutz Catalogues describe these standard security safeguards in detail, which should be taken into consideration for practically every IT system. The catalogues contain:
- standard security safeguards for typical business processes, applications, and IT systems with "normal" protection requirements,
- a description of the threat scenarios usually applicable, and
- detailed descriptions of safeguards to facilitate their implementation.
A comprehensive description of the process for achieving and maintaining an adequate level of security, as well as a simple approach for determining the achieved level of security in the form of a target-actual comparison can be found in BSI standards 100-1, 100-2, and 100-3 for IT-Grundschutz.
Since the IT-Grundschutz also proved popular on an international scale, the IT-Grundschutz Catalogues and the GSTOOL, as well as most of the other documents relating to IT-Grundschutz, are also available in digital form in the English language.
1.2 IT-Grundschutz: Objectives, concept, and design

The IT-Grundschutz Catalogues contain recommendations for standard security safeguards for typical business processes, applications, and IT systems. The objective of IT-Grundschutz is to achieve an adequate level of protection for all information available in an organisation. In so doing, IT-Grundschutz follows a holistic approach. By combining standard organisational, personnel, infrastructural, and technical security safeguards, it is possible to attain a level of security that is adequate for normal protection requirements and appropriate for protecting business-relevant information Furthermore, the safeguards in the IT-Grundschutz Catalogues not only form a basis for IT systems and applications requiring a high level of protection, but also provide high-quality security at many locations.
IT-Grundschutz follows a modular approach in order to be able to better prepare and structure the highly heterogeneous field of information technology, including the application environment. The individual modules reflect typical business process workflows and areas of IT use, for example emergency management, client/server networks, buildings, and communication and application components. Each module starts with a description of the expected threat scenario including descriptions of the typical threats in the scenario as well as general estimates of their probabilities of occurrence. This threat scenario forms the basis for generating a specific bundle of security safeguards for the fields of infrastructure, personnel, organisation, hardware and software, communication, and contingency planning.
The IT-Grundschutz approach makes the process of drawing up IT security concepts easier and more efficient. Within the framework of traditional risk analysis, the basic threats are initially determined and then evaluated with probabilities of occurrence in order to be able to subsequently select suitable security safeguards and to assess the residual risk afterwards. For IT-Grundschutz, these steps have already been completed for each module and the appropriate security safeguards have already been selected for typical application scenarios. When applying IT-Grundschutz, the analysis is reduced to a target-actual comparison between the safeguards recommended in the IT-Grundschutz Catalogues and those already implemented. Any missing or not yet implemented safeguards identified in so doing point out the security shortcomings to be eliminated with the help of the recommended safeguards. Only in the event of significantly higher protection requirements it is necessary to also perform a additional security analysis taking into consideration cost and effectiveness aspects. However, in this context it is generally adequate to supplement the recommended security safeguards in the IT-Grundschutz Catalogues with the corresponding individual, higher quality safeguards. A simple approach regarding this is described in BSI standard 100-3 Risk analysis based on IT-Grundschutz.
The IT-Grundschutz Catalogues are a valuable aid even for special components or application environments not addressed sufficiently in the IT-Grundschutz Catalogues. The required additional analysis can then focus on the specific threats and security safeguards for these components or general conditions.
The safeguards listed in the IT-Grundschutz Catalogues are the standard security safeguards, i.e. the safeguards to be implemented for the corresponding modules according to the current state of the art in order to achieve an adequate basic level of security. In this, the safeguards required to obtain the certification according to ISO 27001 based on IT-Grundschutz constitute the minimum of what must reasonably be implemented in the field of security safeguards. The safeguards identified as "additional" have also proven their worth in practice, but are aimed at applications with higher protection requirements. Security concepts based on IT-Grundschutz can be very compact in design, because it is only necessary to refer to the corresponding safeguards in the IT-Grundschutz Catalogues within the concept. This promotes understandability and clarity. In order to make the implementation of the recommend safeguards easier, the security safeguards are described in detail in the IT-Grundschutz Catalogues. When technical terminology is used, it is ensured that the descriptions can be understood by those who need to implement the safeguards.
To simplify the implementation of the safeguards, the IT-Grundschutz Catalogues, like most of the information relating to IT-Grundschutz, are also available in electronic form. Furthermore, resources and sample solutions are provided to help implement the safeguards, some of which were provided by the BSI, and some by IT-Grundschutz users.
Since the field of information technology is highly innovative and is constantly developing, the present catalogues were designed in such a way that they can be updated and expanded easily. The Federal Office for Information Security constantly updates the IT-Grundschutz Catalogues and adds new topics based on the feedback provided in user surveys.
The BSI provides all users with the opportunity to register voluntarily, and of course free of charge. Registered users regularly receive information regarding current topics relating to IT-Grundschutz and information security. Registration is also required to participate in the user surveys. The catalogues can only be revised and updated as necessary by continuously exchanging experiences with IT-Grundschutz users. The ultimate goal of these efforts is to be able to show current recommendations for typical information security problems. Recommended safeguards not updated and expanded regularly become outdated very quickly or have to be written so generally that they cannot achieve their intended goal of identifying security gaps and simplifying the specific implementation.
1.3 Structure of the IT-Grundschutz Catalogues

The IT-Grundschutz Catalogues can be divided into different areas that are explained below for the purpose of better understanding:
Introduction and approach
This introductory section briefly describes the design of IT-Grundschutz and the approach for drawing up a security concept according to IT-Grundschutz. A detailed description of the approach according to IT-Grundschutz can be found in BSI standard 100-2. Furthermore, the structure of the IT-Grundschutz Catalogues and their use are explained.
Information security management
The planning and management tasks necessary to design and continuously implement a sophisticated and thoroughly planned information security process are referred to as information security management or shortly IS management.
Experience has shown that it is practically impossible to achieve and maintain a consistent and adequate level of security without a properly working IS management. Therefore, BSI standard 100-1 "Information Security Management Systems (ISMS)" describes what such a management system should provide and which tasks are related to it.
Based on this standard, module S 1.0 Security management of the IT-Grundschutz Catalogues describes what an efficient information security management system should look like and which organisational structures are reasonable for this system. Furthermore, it also describes a systematic method for configuring a functioning IS management system and further developing this system during operation.
Modules
Each of the modules of the IT-Grundschutz Catalogues contains a short description of the applicable components, approaches, and IT systems, as well as an overview of the threat scenario and the recommended safeguards. The modules are grouped into the following catalogues according to the IT-Grundschutz layer model:
- S 1: Comprehensive aspects of information security
- S 2: Security of the infrastructure
- S 3: Security of IT systems
- S 4: Security in networks
- S 5: Security in applications
Threat catalogues
This section contains detailed descriptions of the threats referred to as the threat scenarios in the individual modules. The threats are divided into six catalogues:
- T 0: Basic threats
- T 1: Force Majeure
- T 2: Organisational Shortcomings
- T 3: Human Error
- T 4: Technical Failure
- T 5: Deliberate Acts
Additionally, a Threats Catalogue T 0 Basic threats was added containing generalised basic threats reduced to bare essentials. This catalogue may be used as a basis for risk analyses, for example.
Safeguard catalogue
This section describes the security safeguards mentioned in the modules of the IT-Grundschutz Catalogues in detail. The safeguards are divided into six safeguard catalogues:
- S 1: Infrastructure
- S 2: Organisation
- S 3: Personnel
- S 4: Hardware and Software
- S 5: Communication
- S 6: Contingency Planning
Structure of the modules
The modules play the central role of the IT-Grundschutz Catalogues, which all have the same basic structure. Each module starts with a short description of the components, the approach, and/or the IT system examined in the module.
The threat scenario is described subsequently. The threats are divided into the areas of Force Majeure, Organisational Shortcomings, Human Error, Technical Failure, and Deliberate Acts mentioned above.
To keep the modules clear and to avoid redundancies, only references to the text of the threats are provided. Here is an example of a reference to a threat in a module:
- - T 4.1 Disruption of power supply
In this case, the letter "T" in T x.y stands for threat. The number x before the decimal point refers to the corresponding Threat Catalogue (T 4 = Technical Failure) and the number y after the decimal point refers to the number of the threat in that catalogue. This is followed by the name of the threat. It is recommended to read the texts of the threats in order to increase awareness for these threats and to better understand the safeguards, but it is not absolutely necessary to read them before creating a security concept based on IT-Grundschutz.
The most important section of each module is the section containing the recommended safeguards following the threat scenario. At first, short notes regarding the respective bundle of safeguards are shown, e.g. with regard to the proper sequence while implementing the required measures.
In each module, an overview of the topic under review is provided before the list of safeguards in the form of a life cycle that describes which safeguards should be implemented in which phase and for what purpose. Normally, the following phases can be identified, with typical work to be performed within the framework of individual safeguards being specified for each of these phases. Security management and auditing affect all phases since they accompany and monitor the entire life cycle.
| Phase | Typical tasks |
|---|---|
| Planning and design |
|
| Purchasing (if necessary) |
|
| Implementation |
|
| Operation |
|
| Disposal (if necessary) |
|
| Contingency Planning |
|
Corresponding safeguards are not provided for each phase in all modules. For example, there are no safeguards in the purchasing phase in the module "Internet Information Server", because this module is based on the implementation of the "Web servers" module and the decision regarding which product to select has already been made.
Experience has shown that the phases must be executed repeatedly, since all business processes, IT systems, and application conditions are subject to constant changes and new developments. Information security management must ensure the aforementioned.
Similar to the threats, the safeguards are divided into the Infrastructure, Organisation, Personnel, Hardware and Software, Communication, and Contingency Planning Safeguard Catalogues. Just like for the threats, the corresponding safeguards are only referenced here. The following is an example of a reference in a module to a recommended safeguard:
- - S 1.15 (A) Closed windows and doors
In this case, the letter "S" in S x.y stands for safeguard and the number x before the decimal point refers to the Safeguard Catalogue (here S 1 = Infrastructure). The number y after the decimal point refers to the number of the safeguard in the respective catalogue.
The letters in brackets (in this case (A)) specify the qualification level for each safeguard, which is a classification as to whether this safeguard is required for the IT-Grundschutz qualification. The following classifications are provided::
| Qualification level | Description |
|---|---|
| A (Entry) | These safeguards must be implemented for all three types of qualification according to IT-Grundschutz ("IT-Grundschutz Entry Level" auditor attestation, "IT-Grundschutz Secondary Level" auditor attestation, and ISO 27001 certification based on IT-Grundschutz). These safeguards are essential to security in the corresponding module. Their implementation must be given high priority. |
| B (Secondary) | These safeguards must be implemented for the "IT-Grundschutz Secondary Level" auditor attestation and for ISO 27001 certification based on IT-Grundschutz. They are particularly important for establishing a level of information security that can be monitored. They should be implemented promptly. |
| C (Certificate) | These safeguards must be implemented for ISO 27001 certification based on IT-Grundschutz. They are important for rounding off information security. Their implementation can be put off until later if bottlenecks arise. |
| Z (Additional) | These safeguards do not necessarily have to be implemented in a binding manner for an auditor attestation or for ISO 27001 certification based on IT-Grundschutz. They represent additional safeguards that may prove helpful especially when there are higher security requirements. |
| W (Knowledge) | These safeguards are intended to convey the basic principles and know-how helpful for understanding and implementing the other safeguards. These safeguards do not have to be checked for an auditor attestation or for ISO 27001 certification based on IT-Grundschutz. |
In order to be able to create a security concept according to IT-Grundschutz and to perform the target-actual comparison required to this end, it is necessary to carefully read the texts of the safeguards identified in the modules in each case found in the respective Safeguard Catalogue. An excerpt from a safeguard is provided below as an example:
S 2.11 Provisions governing the use of passwords
Initiation responsibility: Head of IT, IT Security Officer
Implementation responsibility: IT Security Officer, Users
[Text of the safeguard ...]
Review questions:
- Are there clear rules for the use and composition of passwords?
[...]
The safeguards should be implemented according to their meaning. The texts are written in such a way that they can be applied to as many areas as possible. Before implementing the recommended safeguards, it must always be checked whether they must be adapted to the particular organisation or the information system. All changes should be documented so that the reasons can still be understood later.
In addition to the actual recommendation of how to implement the individual safeguards, examples of the persons responsible are provided. Initiation responsibility refers to the persons or roles who should typically initiate the implementation of a safeguard. Implementation responsibility refers to the persons or roles who should implement the safeguard.
Review questions can be found at the end of the majority of the safeguards.
These questions are formulated in such a way that they can be used as the final checklist in order to check the implementation of the safeguards. They specify the objective and the basic orientation of the security recommendations and can be used as the basis for audits and certification audits. After having answered all review questions, it can be stated to which extent the objectives of the individual modules are fulfilled in the organisation.
Review questions are always closed questions that can be answered with "Yes" or "No". In this, "Yes" means that the respective requirement is met. This way, the review questions can also be analysed with the aid of tools. Review questions are formulated more generally and abstractly than the safeguard texts. Details on the specific implementation of recommendations can be found in the respective safeguards.
Review questions were not necessarily introduced for all safeguards, because the questions are not intended to be used for designing security concepts, but for checking the implemented security safeguards. For example, the safeguards in the "Purchasing" life cycle phase do not contain any review questions, because security recommendations to be observed before purchasing systems were formulated here. However, within the framework of an audit it can only be checked whether the existing systems are operated securely.
The relationship between the assumed threats for IT-Grundschutz and the recommended safeguards can be obtained from the safeguard-threat tables. These tables can be found in the IT-Grundschutz section of the BSI website. There is one safeguard-threat table for each module.
An excerpt from the safeguard-threat table for module S 2.10 Mobile workplace is shown below as an example:
| S 2.10 | Phase | Level | T 1. 15 |
T 2. 1 |
T 2. 4 |
T 2. 47 |
T 2. 48 |
T 3. 3 |
T 3. 43 |
T 3. 44 |
T 5. 1 |
T 5. 2 |
T 5. 4 |
T 5. 71 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| S 1.15 | OP | A | X | X | ||||||||||
| S 1.23 | OP | A | X | X | ||||||||||
| S 1.45 | OP | A | X | X | X | X | X | |||||||
| S 1.46 | OP | Z | X | |||||||||||
| S 1.61 | PD | A | X | X | X | X | X |
All tables have the same layout. The column headers contain the numbers of the threats listed in the corresponding module. The first column contains the number of the corresponding safeguard. The second column contains the life cycle phase the respective safeguard for the corresponding module belongs to. For space reasons, the following abbreviations for the individual life cycle phases are used: PD for "Planning and Design", PU for "Purchasing", IM for "Implementation", OP for "Operation", DI for "Disposal", and CP for "Contingency Planning". The third column notes the classification regarding an IT-Grundschutz qualification assigned to the individual safeguard for the corresponding module.
The other columns describe the relationships between the safeguards and the threats. If an "X" is entered in a field, this means that the corresponding safeguard is effective in counteracting the corresponding threat. This effect may be of a preventative or loss minimising nature.
It must be noted that only the most important threats against which a certain safeguard is effective are listed in the safeguards-threats tables. In particular, this means that a safeguard is not automatically superfluous if none of the threats assigned in the table are relevant to a certain application case. Whether or not a standard security safeguard is necessary must always be checked and documented on a case-by-case basis according to the overall security concept and not only based on the safeguards-threats table.
Finally, it must be mentioned that all modules, threats, safeguards, tables, and resources are available in electronic form. These texts can be used when drawing up a security concept and when implementing safeguards.
1.4 Application methods of the IT-Grundschutz Catalogues

Numerous tasks must be performed in order to successfully establish an end-to-end and effective security process. The IT-Grundschutz approach (see BSI standard 100-2) and the IT-Grundschutz Catalogues provide a wealth of information on methodology and practical implementation aids. They furthermore contain potential solutions for various tasks relating to information security, for example security design, auditing, and certification. Depending on the task at hand, different ways of using the IT-Grundschutz may be appropriate. This section is intended to facilitate the direct entry into the individual ways of use by providing cross-references to the corresponding chapters of the IT-Grundschutz approach in BSI standard 100-2.
Security process and information security management
Information constitutes an essential value for companies and government agencies and therefore requires adequate protection. Depending on the type of information, protection focuses on different goals: for example, it must be ensured that information is treated confidentially, that it is not changed deliberately or accidentally, and that it is available when needed.
Today, the majority of information is at least partially generated, stored, transported, or processed further with the help of information technology (IT). The dependence on properly functioning information technology has increased significantly in recent years both in public administrations and in private businesses. More and more business processes are outsourced to or intermeshed with information technology. There is no prospect of an end of this development. Therefore, protecting the IT is also part of reasonable information security.
Information security is relevant for all business processes and specialised tasks and must therefore be deemed an integral part of the original task. The following action plan contains all essential steps necessary for a continuous security process and should therefore be viewed as a planned, well-founded approach to achieve and maintain an adequate level of security:
- initiation of the security process
- acceptance of responsibility by the management level
- design and planning of the IT Security Process
- drawing up of an information security policy
- establishment of a suitable organisational structure for information security management
- provision of financial resources, personnel, and the necessary time
- integration of all employees in the security process
- drawing up of a security concept
- implementation of the security concept and of the security safeguards
- maintenance of information security during operation and continuous improvement
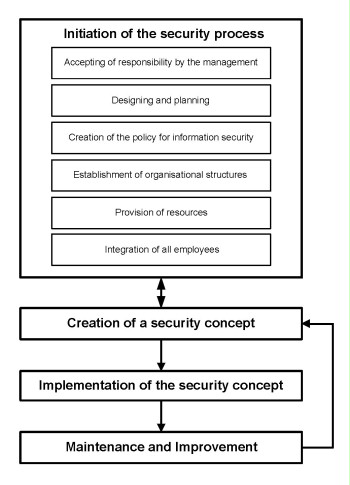
Figure: Phases of the security process
The sequence is described in detail in the BSI standard 100-2. Furthermore, an overview of the security process is contained in module S 1.0 Security management, and a detailed explanation of each of the actions is provided in the form of recommended standard safeguards.
In order to draw up the security concept, several steps explained briefly below are required according to IT-Grundschutz.
Structure analysis
An information system (or also IT system) refers to all infrastructural, organisational, personnel, and technical objects serving to perform tasks in a particular field of application of information processing. At the same time, an information system may refer to the entire organisation or to individual areas defined by organisational structures (e.g. departments) or joint business processes and/or shared applications (e.g. HR information system).
In order to create a security concept and especially in order to apply IT-Grundschutz, it is necessary to analyse and document the structure of the existing information system. Therefore, the information, applications, IT systems, rooms, communication networks required for performing the business processes or specialised tasks defined in the field of validity are captured within the framework of structure analysis.
The individual steps of the structure analysis are described in detail in chapter 4.2 of the IT-Grundschutz approach (BSI standard 100-2) in the form of instructions.
Protection requirements determination
The purpose of the protection requirements determination is to determine what level of protection is sufficient and adequate for the information and information technology used. In so doing, the damage to be expected is considered for each application and the information processed that could occur as a result of a loss of confidentiality, integrity, or availability. It is also important to realistically estimate the possible consequential damages. Experience has shown that it is best to divide the protection requirements into three categories: "normal", "high", and "very high". Explanations and practical information on the protection requirements determination are subject of chapter 4.3 of the IT-Grundschutz approach (BSI standard 100-2).
Modelling
Next, the modules of the IT-Grundschutz Catalogues must be imaged to the target objects of the present information system within a modelling step.
Chapter 4.4 of the IT-Grundschutz approach in the BSI standard 100-2 describes how to model an information system using the modules in the IT-Grundschutz Catalogues. Detailed instructions for the use of the layer model and the individual modules within the framework of modelling can be found in chapter 2 of the IT-Grundschutz Catalogues. The modelling result is an initial, rough draft of the security concept.
Basic security check
The basic security check is an organisational instrument providing a quick overview of the present level of security. With the help of interviews, the status quo of an existing information system (modelled according to IT-Grundschutz) is determined in terms of the degree of implementation of the security safeguards in the IT-Grundschutz Catalogues. The result is an overview where the implementation status "Unnecessary", "Yes", "Partially", or "No" is recorded for each relevant safeguard. By identifying which safeguards have not been implemented yet or have only been implemented partially, potential improvements regarding the security of the target objects being analysed are indicated. Chapter 4.5 of BSI standard 100-2 describes an action plan for performing the basic security check. This plan takes into account both organisational aspects and the technical requirements in the field of project implementation.
Additional security safeguards
The standard security safeguards in IT-Grundschutz normally offer sufficient and adequate protection. However, it may make sense to check whether additional or even higher-quality security safeguards are necessary, particularly in the case of high or very high protection requirements.
Within the framework of the additional security analysis (see chapter 4.6 of BSI standard 100-2), which target objects of the analysed information system a risk analysis is required for is decided in order to define further security measures, if necessary. One risk analysis method on the basis of IT-Grundschutz is described in BSI standard 100-3.
An additional security analysis is also necessary if parts of the information system cannot be mapped adequately using the existing modules of the IT-Grundschutz Catalogues or if special application scenarios are present which are not included in IT-Grundschutz.
Implementation of security concepts
In order to achieve the intended level of information security, it is necessary to identify any existing vulnerabilities as well as all necessary safeguards. First and foremost, all measures designed in the security concept must be implemented consistently based on an implementation plan. Chapter 5 of BSI standard 100-2 for the IT-Grundschutz approach describes what must be taken into consideration when planning
Security audit
The security safeguards contained in the IT-Grundschutz Catalogues may also be used for the security audit. For this, it is recommended to pursue the same approach used for the basic security check. Producing a separate checklist for each module using the safeguard texts which is adapted to the organisation is helpful and reduces the workload. This facilitates the performance of audits and often improves the reproducibility of the results.
ISO 27001 certification based on IT-Grundschutz
The IT-Grundschutz approach and the IT-Grundschutz Catalogues are not only used for the security design, but are also frequently used as a reference within the meaning of a security standard. By obtaining ISO 27001 certification based on IT-Grundschutz, an organisation can document internally and externally that it has implemented both ISO 27001 and IT-Grundschutz to the extent required.
The qualification level is divided into three different stages that differ in terms of quality (i.e. the required degree of implementation of the security safeguards) as well as in terms of trustworthiness. The entry level can be verified by a certified auditor and the highest level additionally requires testing by an independent certificate authority. The audit scheme for ISO 27001 certifications based on IT-Grundschutz, as well as the corresponding certification scheme for auditors can be found on the BSI web server.

