2 Layer model and modelling
2.1 Modelling according to IT-Grundschutz
When implementing IT-Grundschutz, the information system considered must be modelled with the help of the existing modules so that the relevant security safeguards can be compiled from the IT-Grundschutz Catalogues. For this, the structure analysis and a protection requirements determination must be available. Building upon these documents, an IT-Grundschutz model of the information system is developed that consists of the various IT-Grundschutz modules, possibly used several times, and a mapping between these modules and the security-relevant aspects of the information system.
Whether the information system consists of already used IT systems or whether it is an information system that is still in the planning stages does not matter for the developed IT-Grundschutz model. However, the model may be used in different ways:
- The IT-Grundschutz model of an already implemented information system identifies the relevant standard security safeguards based on the modules used. It can be used in the form of a test plan to perform a target-actual comparison.
- On the other hand, the IT-Grundschutz model of a planned information system constitutes a development concept. Using the selected modules, it describes which standard security safeguards must be implemented when the information system is implemented.
The position of the modelling phase and the possible results are illustrated in the following figure:
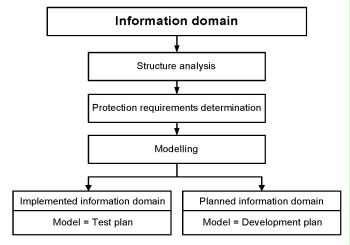
Figure: Results of modelling according to IT-Grundschutz
Typically, an information system currently in use will include both implemented components and also components still in the planning stages. The resulting IT-Grundschutz model then contains both a test plan and some elements of a development concept.
In order to map a generally complex information system to the modules in the IT-Grundschutz Catalogues, it makes sense to consider the security aspects grouped according to certain topics:
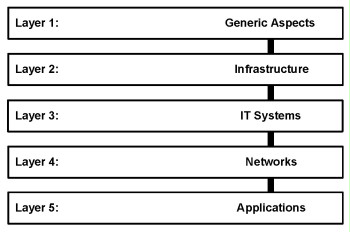
Figure: Layers of the IT-Grundschutz modell
The security aspects of an information system are assigned to the individual layers as follows:
- Layer 1 covers the comprehensive security aspects equally applicable to all or most of the information system. This particularly applies to comprehensive concepts and the regulations derived from such. Typical layer 1 modules include Security management, Organisation, Data backup policy, and Protection against malware, amongst other things.
- Layer 2 covers the physical, technical circumstances. In this layer, various aspects of infrastructural security are merged. For example, this refers to the Building, Server room, Computer centre, and Home workplace modules.
- Layer 3 addresses the individual IT systems of an information system that may have been divided into groups. This layer addresses security aspects both for clients, servers, and stand-alone systems. This layer includes the modules Telecommunication system, Laptop, and Client under Windows Vista, for example.
- Layer 4 examines the networking aspects not directly related to specific IT systems, but to the network connections and the communication. This includes the modules Network management, WLAN, VoIP, as well as VPN, for example.
- Layer 5 ultimately addresses the actual applications used on the information system. Amongst other things, the modules Groupware, Web server, Fax server, and databases can be used for modelling in this layer.
The task for modelling according to IT-Grundschutz now consists of deciding for the modules of each layer whether and how they can be used to model the information system. Depending on the module considered, there may be different types of target objects in the map: individual business processes or components, groups of components, buildings, properties, organisational units, etc.
The approach used to model an information system is described in detail below. In this, particular importance is attached to the general conditions as to when it is appropriate to use an individual module and which target objects it should be applied to.
When modelling an information system according to IT-Grundschutz, the problem that there are target objects that cannot be mapped adequately using the existing IT-Grundschutz modules may arise. In this case, an additional security analysis should be performed as described in the IT-Grundschutz approach.
2.2 Assignment based on the layer model
When modelling an information system, it is recommended to assign the modules based on the layer model. The completeness check is then performed directly after modelling.
Layer 1: Comprehensive aspects of information security
In this layer, all aspects of the information system superordinate to the technical components are modelled. In doing so, the focus is on the concepts and the regulations derived from these concepts. These aspects should be controlled uniformly for the entire information system so that the corresponding modules must only be applied once for the entire information system in most cases. Information security management, the organisation of IT operations, as well as training and sensitisation programmes for the personnel are of particular importance in this. The implementation of the safeguards relating to this is of fundamental importance for the secure use of business-relevant information and information and communication technologies. For this reason, the corresponding modules must always be applied, regardless of which technical components are used.
- Module S 1.0 Security management must be applied once to the entire information system. A properly functioning information security management system is the essential foundation for achieving an adequate level of security. If outsourcing is used, special rules apply to the application of this module with these rules being described in the BSI document "IT-Grundschutz Certification of Outsourced Components".
- Module S 1.1 Organisation must be used at least once for each information system. If parts of the present information system are assigned to another organisation (or organisational unit) and are therefore subject to different general conditions, the module should be applied separately to each organisation (or organisational unit). If outsourcing is used, special rules apply to the application of this module with these rules being described in the BSI document "IT-Grundschutz Certification of Outsourced Components".
- Module S 1.2 Personnel must be used at least once for each information system. If parts of the present information system are assigned to another organisation (or organisational unit) and are therefore subject to different general conditions, the module should be applied separately to each organisation (or organisational unit). If outsourcing is used, special rules apply to the application of this module with these rules being described in the BSI document "IT-Grundschutz Certification of Outsourced Components".
- Module S 1.3 Emergency management must at least be applied if components with high or very high protection requirements regarding the availability were identified within the framework of the protection requirements determination or if larger IT systems and/or comprehensive networks are operated. When working through the module, special attention should be paid to these components. If outsourcing is used, then special rules apply to the application of this module with these rules being described in the BSI document "IT-Grundschutz Certification of Outsourced Components".
- Module S 1.4 Data backup policy must be applied once to the entire information system.
- Module S 1.5 Data protection is intended to provide users in Germany with a basic guide if components processing or otherwise using personal or person-related data were identified during the protection requirements determination. It should be checked whether the module should not only be applied to individual information systems or procedures, but to the organisation as a whole.
- Module S 1.6 Protection against malware must be applied once to the entire information system.
- The bundle of security safeguards relating to the crypto-concept are presented in the following. Safeguards from other modules are not repeated here.
- Module S 1.8 Handling security incidents must at least be applied if the protection requirements determination identified components with high or very high protection requirements in terms of the three fundamental values or if the failure of the entire information system would lead to damage categorised as high or very high. If outsourcing is used, then special rules apply to the application of this module, with these rules being described in the BSI document "IT-Grundschutz Certification of Outsourced Components".
- Module S 1.9 Hardware and software management must be used at least once for each information system. If parts of the present information system are assigned to another organisation (or organisational unit) and are therefore subject to different general conditions, the module should be applied separately to each organisation (or organisational unit). If outsourcing is used, then special rules apply to the application of this module, with these rules being described in the BSI document "IT-Grundschutz Certification of Outsourced Components".
- Module S 1.10 Standard software must at least be applied once to the entire information system. If there are parts in the information system having different requirements or regulations regarding the use of standard software, module S 1.10 should be applied to each of these parts separately.
- Module S 1.11 Outsourcing must at least be applied if all of the following conditions are met:
- IT systems, applications, or business processes are outsourced to an external service provider, and
- a long-term contract has been concluded with the service provider, and
- the information security of the customer is affected by the service, and
- the service provider also regularly performs significant information security management tasks within the framework of providing the contracted services.
- Module S 1.12 Archiving must be applied to the information system if internal or external specifications require long-term archiving of electronic documents or if a system for long-term archiving of electronic documents is already in operation.
- Module S 1.13 Information security awareness and training must be applied to the entire information system.
- Module S 1.14 Patch and change management must at least be applied to larger information systems, i.e. when larger IT systems and/or comprehensive networks are operated. For smaller and less complex information systems, it is sufficient to implement S 2.221 Change management.
- Module S 1.15 Deleting and destroying data must be applied once to the entire information system.
- Module S 1.16 Compliance must be applied once to the entire information system.
Layer 2: Security of the infrastructure
The structural circumstances relevant to the present information system are modelled with the help of the modules in layer 2 "Security of the infrastructure". The corresponding module from the IT-Grundschutz Catalogues is assigned to each building, room, or protective cabinet (and/or groups of such components).
- Module S 2.1 General building must be applied once to each building and/or group of buildings.
- Module S 2.2 Cabling must normally be applied once per building and/or group of building (additionally to module S 2.1 General building). Furthermore, module S 2.2 may also be applied to individual rooms and/or groups of rooms, for example server rooms or computer centres, if these rooms are characterised by particularities in terms of electrical cabling. Module S 2.12 IT cabling must be applied additionally to IT cabling.
- Module S 2.3 Office / local workplace must be applied to each room or area and/or each group of rooms the employees are located in to perform their tasks.
- Module S 2.4 Server room must be applied to each room and/or group of rooms where servers or telecommunication systems are operated. Servers are IT systems that provide services in the network. Module S 2.4 does not need to be applied additionally to rooms module S 2.9 Computer centre is applicable to.
- Module S 2.5 Data media archives must be applied to each room and/or group of rooms data media are stored or archived in.
- Module S 2.6 Technical infrastructure room must be applied to each room and/or group of rooms technical devices are operated in that do not require any or only a low amount of manual operation (e.g. distribution cabinet, backup power supply system).
- Module S 2.7 Protective cabinets must be applied once to each protective cabinet and/or group of protective cabinets. Protective cabinets may serve as a replacement for a dedicated server room, if necessary.
- Module S 2.8 Home workplace must be applied once to each home workplace and/or each group (if corresponding groups were defined.)
- Module S 2.9 Computer centre must be applied once to each computer centre. A computer centre refers to the equipment and rooms needed for operating a larger data processing system used centrally by several locations. Module S 2.4 Server room does not have to be applied additionally to rooms module S 2.9 is applied to.
- Module S 2.10 Mobile workplace must always be applied if there are employees frequently no longer working only on the premises of the company and/or government agency, but at alternating workplaces outside of the organisation instead. Laptops are typical target objects for module S 2.10.
- Module S 2.11 Meeting, event and training rooms must be applied once to any such room and/or group of rooms (if the corresponding groups have been defined).
- Module S 2.12 IT cabling generally must be applied once per building and/or group of buildings (in addition to module S 2.1 General building). Furthermore, module S 2.12 may also be applied to individual rooms and/or groups of rooms, for example server rooms or computer centres, if these rooms are characterised by particularities in terms of IT cabling. Module S 2.2 Cabling must also be applied additionally to the electrical cabling.
Layer 3: Security of the IT systems
Security aspects related to IT systems are addressed in this layer. This layer is divided into Servers, Clients, Network components, and Miscellaneous for reasons of clarity.
Similar to the "Security of the infrastructure" area, the modules of the "Security of the IT systems" area can be applied both to individual IT systems and to groups of such IT systems. This will not be emphasised separately in the following.
Servers
- Module S 3.101 General server must be applied to each IT system offering services (e.g. file or print services) in the network as a server.
- Module S 3.102 Server under Unix must be applied to each server running this operating system.
- Module S 3.107 S/390 and zSeries mainframes must be applied to each S/390 or zSeries mainframe.
- Module S 3.108 Windows Server 2003 must be applied to each server running this operating system.
- Module S 3.109 Windows Server 2008 must be applied to each server running this operating system.
Note: Module S 3.101 General server must be applied to each server (and each mainframe) in addition to the operating system-specific module S 3.101, since this module summarises the platform-independent security aspects for servers.
Clients
- Module S 3.201 General client must be applied to each client. Clients are workstation computers operated regularly or at least occasionally in a network (in contrast to stand-alone systems).
- Module S 3.202 General stand-alone IT system must be applied to each stand-alone system. Stand-alone systems are workstation computers not operated at all or only in exceptional cases in a network (in contrast to clients).
- Module S 3.203 Laptop must be applied to each mobile computer (laptop).
- Module S 3.204 Unix client must be applied to each stand-alone computer or client running this operating system.
- Module S 3.208 Internet PCs must be applied to each computer only intended for using internet services and not connected to the internal network of the organisation. In this special scenario, no additional modules from the IT-Grundschutz Catalogues need to be applied to this computer (and/or this group of computers).
- Module S 3.209 Windows XP client must be applied to each stand-alone computer or client running this operating system.
- Module S 3.210 Client under Windows Vista must be applied to each stand-alone computer or client running this operating system.
- Module S 3.211 Client under Mac OS X must be applied to each stand-alone computer or client running this operating system.
- Module S 3.212 Client under Windows 7 must be applied to each stand-alone computer or client running this operating system.
Note: Either module S 3.201 General client or module S 3.202 General stand-alone IT system must always be applied to each client in addition to the operating system-specific module, since these modules summarise the platform-independent security aspects for clients.
Network components
- Module S 3.301 Security gateway (firewall) must always be applied if networks with different levels of trustworthiness are connected. A typical application case includes the protection of an external connection (for example at the interface between an internal network and the internet or links to networks of business partners). However, the module must also be applied when two internal networks of an organisation with different protection requirements are linked, for example when separating the office communication network from the network of the development department, because particularly confidential data is processed there.
- Module S 3.302 Routers and switches must be applied in each active network used withinthe present information system.
- Module S 3.303 Storage systems and storage networks must always be applied if dedicated storage systems are used to store data. Typical target objects of this module include NAS (Network Attached Storage) systems and SAN (Storage Area Network) systems.
- Module S 3.304 Virtualization must be applied to each virtualization server or each group ofvirtualization servers.
- Module S 3.305 Terminal server must be applied to each terminal server of the information system considered
Miscellaneous
- Module S 3.401 Telecommunications system must be applied to each telecommunications system and/or each corresponding group.
- Module S 3.402 Fax machine must be applied to each fax machine and/or each corresponding group.
- Module S 3.404 Mobile telephone should at least be applied once if the organisation (or organisational unit) being considered does not generally prohibit the use of mobile telephones. If mobile telephones are used in several different areas of application (for example when there are several mobile telephone pools), module S 3.404 must be applied separately to each area.
- Module S 3.405 PDAs should at least be applied once if the organisation (or organisational unit) being considered does not generally prohibit the use of PDAs. Module S 3.201 General clients does not have to be applied additionally in this case.
- Module S 3.406 Printers, copiers, and all-in-one devices should be applied at least once per information system. Here, an all-in-one device is a device offering several different paper processing functions, for example printing, copying, and scanning, but also fax services.
Layer 4: Security in networks
This layer addresses security aspects in networks that cannot be associated with specific IT systems (e.g. servers). Instead, this layer addresses security aspects related to the network connections and the communication between the IT systems.
In order to reduce the level of complexity, it makes sense to consider each section individually instead of examining the network as a whole. The network as a whole must be divided into subnetworks based on the following two criteria:
- within the framework of the protection requirements determination, connections were identified that should never be used to transport certain types of data. These connections are used as "interfaces" between subnetworks, i.e. the end points of such a connection should be located in separate subnetworks. On the other hand, connections transporting data with high or very high protection requirements should not connect to computers outside the bounds of the subnetwork. This results in the definition of subnetworks with as uniform protection requirements as possible.
- Components only linked through a long-distance connection should not be assigned to the same subnetwork, i.e. subnetworks should not extend across several locations or separate properties. This is desirable both for reasons of clarity and with regard to efficient project implementation.
If these two criteria do not result in a suitable division of the network into subnetworks (for example because some of the resulting subnetworks are too large or too small), the network can be divided into subnetworks at the organisational level as an alternative. In this case, the areas of responsibility of the individual administrators or teams of administrators are used to divide the network into subnetworks.
It is impossible to provide a generally applicable recommendation as to which division of a network into subnetworks should be preferred if the requirements specified above are basically incompatible with the present information system. Instead, the decision as to which division of a network in subnetworks is most practicable in terms of the modules if the IT-Grundschutz Catalogues to be applied must be made on a case-by-case basis.
- Module S 4.1 Heterogeneous networks must normally be applied once to each subnetwork. If the subnetworks are too small and a single team of administrators is responsible for several different subnetworks, it may be sufficient to apply module S 4.1 just once to all of the subnetworks, however.
- Module S 4.2 Network and system management must be applied to each network and/or system management system used in the present information system.
- Module S 4.3 Modems must be applied to all external connections established using modems.
- Module S 4.4 VPN must be applied once to any kind of remote accesses to the information system, i.e. internal networks of IT systems. This includes connections established using data networks, e.g. site-to-site, end-to-end, or remote-access VPNs, and using telecommunications connections, e.g. analogous switched lines, ISDN, or mobile telephony.
- Module S 4.5 LAN connection of an IT system via ISDN must be applied to all external connections established using ISDN.
- Module S 4.6 WLAN must be applied to all communication networks implemented according to the IEEE 802.11 series of standards and their extensions.
- Module S 4.7 VoIP must be applied to all communication networks VoIP technology is used in. If line switching telecommunications systems exchange information using an IP network, module S 4.7 VoIP must be applied as well.
- Module S 4.7 VoIP must be applied to all communication networks VoIP technology is used in. If line switching telecommunications systems exchange information using an IP network, module S 4.7 VoIP must be applied as well.
Layer 5: Security in applications
The applications are modelled in the lowest layer of the information system to be modelled. State-of-the-art applications are seldom restricted to just a single IT system. In particular, core applications used throughout a government agency or company are generally implemented as client/server applications. In many cases, the servers themselves access other downstream servers, for example database systems. The security of the applications therefore needs to be examined separately from the IT systems and the networks.
- The recommendations of module S 5.1 Peer-to-peer services were integrated into moduleS 3.201 General client in 2009.
- Module S 5.2 Exchange of data media should be applied once to each application that serves as a source of data when exchanging data media or processes data received on exchanged data media.
- Module S 5.3 Groupware must be applied to each Groupware system (internal or external) of the information system considered.
- Module S 5.4 Web server must be applied to each server of the considered information system providing websites (e.g. intranet or internet).
- Module S 5.5 Lotus Notes / Domino must be applied once to each server with Lotus Domino and each Lotus Notes client and/or each corresponding group in the information system.
- Module S 5.6 Fax server must be applied to each fax server and/or each corresponding group.
- Module S 5.7 Databases should be applied once per database system and/or per group of database systems.
- Module S 5.8 Telecommuting must be applied to each telecommuter workplace and/or each corresponding group.
- Module S 5.9 Novell eDirectory should be applied once to each directory service implemented with the help of Novell eDirectory. Additionally, module S 5.15 General directory service must be applied at all times.
- Module S 5.12 Microsoft Exchange/Outlook must be applied, in addition to module S 5.3, to each workgroup or email system based on Microsoft Exchange and/or Microsoft Outlook.
- Module S 5.13 SAP System must be applied to each business process application (or group of such applications) based on software provided by SAP.
- Module S 5.14 Mobile data media should at least be applied once to each information system.
- Module S 5.15 General directory service should be applied once to each directory service, regardless of the selected product.
- Module S 5.16 Active Directory should be applied once to each directory service implemented with the help of Microsoft Active Directory. Additionally, module S 5.15 General directory service must be applied at all times.
- Module S 5.17 Samba must be applied to each Samba server of the information system considered.
- Module S 5.18 DNS server must be applied to each DNS server and/or each group of DNS servers operated in the information system.
- Module 5.19 Internet usage must always be applied if internet services are to be used at the workplace.
- Module S 5.20 OpenLDAP should be applied once to each directory service implemented with the help of OpenLDAP. Additionally, module S 5.15 General directory service must be applied at all times.
- Module S 5.21 Web applications must be applied to each web service of the information system considered(e.g. intranet or internet) designed as web application.
- Module S 5.22 Logging must at least be applied to larger information systems, i.e. when larger IT systems and/or comprehensive networks are operated. For smaller and less complex information systems, it is sufficient to implement S 2.500 Logging IT systems.
Completeness check
Finally, a check must be performed to ensure the model of the overall system is complete and nothing has been left out. It is recommended to again use the network plan or a comparable overview of the information system to this end and to systematically go through each of the individual components. Each component must be assigned to a group or be modelled individually.
If the network was divided into subnetworks in layer 4, it must be checked whether:
- each subnetwork has been modelled completely and
- the sum of all subnetworks completely reflects the entire network.
It is not only important to model all hardware and software components technically, but also to ensure that all corresponding organisational, personnel, and infrastructural aspects have been completely taken into account.
If gaps are found when checking the model, the corresponding missing modules must be added. Otherwise, there is a risk that integral parts of the overall system or important security aspects are not taken into consideration while applying the IT-Grundschutz.

