S 3.404 Mobile telephones

Description
By now, mobile phones have become integral parts of the communication infrastructure. This poses the question of how to use them securely.
This chapter considers digital mobile communication systems according to the GSM standard (D and E networks). In order to guarantee their secure use, different components and their interaction must be considered (see figure):
- mobile phone
- base statopm
- fixed network
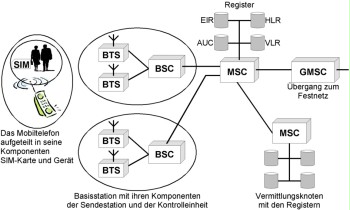
Figure: Different components for secure use of mobile communication systems
Mobile phone
A mobile phone consists of two components: The mobile communication device itself and the identification module, the SIM card (SIM - Subscriber Identity Module). This allows differentiation between user and device in the GSM network.
The mobile communication device is characterised by its internationally unambiguous serial number (IMEI - International Mobile Equipment Identity). The user is identified with the help of his/her customer number stored on the SIM card (IMSI - International Mobile Subscriber Identity). It is assigned to the subscriber by the network operator when concluding the contract. It must be differentiated from the assigned telephone numbers (MSISDN). This separation allows a subscriber to use different mobile communication devices with his/her SIM card.
Amongst other things, the subscriber-related telephone number (MSISDN) is stored on the SIM card. Likewise, the cryptographic algorithms for authentication and user data encryption are implemented there. Furthermore, short messages, information on rates and charges, and a personal telephone book may be stored there.
SIM toolkit
Since 1999, mobile phones and SIM cards with extended menu functions are available. This new "SIM toolkit" standard defines new functions between SIM card and mobile communication device. This way, new data and programs can be downloaded from the network operator during live operations. Using SIM toolkit, completely new service offers can be implemented. For example, it provides the card holder with the option of adapting the menu structure of the mobile phone to the customers' needs. If the customer wants to book a hotel room or a journey using his/her mobile phone, the menu structure of the mobile phone is adapted accordingly by the service provider. However, both the card and the device must support the "SIM toolkit" standard.
Base station
Every network operator operates a large number of transmission stations (BTS - Base Station Transceiver System). Each of these stations may supply an area with a radius of approx. 250 m to 35 km, depending on the transmitting power and the topography of the area. The area of supply of a transmission station is referred to as a radio cell. Several radio cells are controlled by a controller station (BSC - Base Station Controller). The system consisting of transmission station and controller station in turn is referred to as Base Station Subsystem (BSS) or shortly base station.
The base station is the interface between the network and the mobile phone. It provides the channels for signalling and network traffic. The base station is controlled by the network node. This network node assumes all technical functions of a fixed network node, e.g. routing, signalling path switching, and service attribute processing. If there are connection requests to a subscriber in the fixed network, these are forwarded to the fixed network by the network node using a coupling path (GMSC).
When compared to the fixed network, the particularity of the GSM network is that the data is encrypted at the air interface, i.e. between mobile phone and base station. This is intended to protect the subscriber against eavesdropping.
Registers
In order for the network operator to be able to actually provide all required services, the operator must store different data. For example, the network operator must know which subscribers want to use the network and which services they want to use. This data, e.g. subscriber, customer number, and services used, is stored to the Home Location Register (HLR). If a connection, e.g. from a fixed network connection to a mobile phone, is to be established, the network operator must know the location of the subscriber and whether the subscriber switched on his/her mobile phone. This information is stored in the Visitor Location Register (VLR) and in the Home Location Register (HLR). In order to check whether the subscriber is actually authorised to use the mobile communication network (has a card contract), the network operator maintains the identification register (AUC). The security code of the SIM card and the PINs defined by the subscriber are stored here.
Furthermore, the network operator may additionally maintain a device register, the EIR. This register contains all mobile communication devices admissible in the network, divided into three groups: the so-called white, grey, and black lists. The white list contains all harmless devices, the grey list contains all devices which are possibly faulty, and the black list contains all devices registered as being faulty or stolen. However, not all network operators maintain a device register.
In order for the network operator to be able to draw up a detailed settlement of the services used by the customer, the call detail records must be stored. For example, these include information about communication partners (e.g. telephone number of the person called), time and duration of the connection, and the location identifiers of the mobile terminal devices.
Connection establishment
As soon as the owner switches on his/her mobile phone, it registers with the network operator using the nearest base station. With the SIM card and the cryptographic algorithms contained on it, the subscriber identifies him/herself to the network operator. The authentication is performed with the help of a key known only to the network operator and the subscriber. The network operator logs and stores data about the user's identity, the serial number of the mobile phone, and the ID of the base station used for registration. This is performed even if no call is made using the mobile phone. Furthermore, every attempt to
Fixed network
The term fixed network refers to the traditional public telephone network with its connection routes.
Since fixed networks are also used during every mobile communication connection, a host of fixed network threats is also applicable to the use of mobile communication networks. The cabled part of a GSM network is a special case of an ISDN network. Therefore, the threats and safeguards applicable to ISDN are also relevant for GSM for the most part. Module S 4.5 LAN connection of an IT system via ISDN must be taken into account for the field of data exchange.
This chapter considers those security features of mobile phones relevant for the users when using mobile phones. This module illustrates a systematic method for creating a concept for the use of mobile phones in an organisation and how its implementation and integration can be ensured.
Threat scenario
The following typical threats to the IT-Grundschutz are assumed to exist regarding the use of mobile phones:
Organisational Shortcomings
| T 2.2 | Insufficient knowledge of rules and procedures |
| T 2.4 | Insufficient monitoring of security safeguards |
| T 2.7 | Unauthorised use of rights |
Human Error
| T 3.3 | Non-compliance with IT security measures |
| T 3.43 | Inappropriate handling of passwords |
| T 3.44 | Carelessness in handling information |
| T 3.45 | Inadequate checking of the identity of communication partners |
Technical Failure
| T 4.41 | Non-availability of the mobile communication network |
| T 4.42 | Failure of the mobile phone or PDA |
Deliberate Acts
| T 5.2 | Manipulation of information or software |
| T 5.4 | Theft |
| T 5.80 | Hoax |
| T 5.94 | Misuse of cards |
| T 5.95 | Bugging of indoor conversations over mobile phones |
| T 5.96 | Tampering with mobile phones |
| T 5.97 | Unauthorised transfer of data over mobile phones |
| T 5.98 | Interception of mobile telephone calls |
| T 5.99 | Analysis of call data relating to the use of mobile phones |
| T 5.126 | Unauthorised photography and filming with portable terminal devices |
Method recommendation
To secure the information system examined, other modules will need to be implemented in addition to this module. These modules are selected based on the results of the IT-Grundschutz modelling process.
A host of safeguards must be implemented for mobile phones, from the planning phase to the usage phase and to the contingency planning phase. The steps to take to accomplish this as well as the safeguards to implement in each phase are listed in the following.
Planning and design
A security policy describing the safeguards to be implemented should be drawn up so that the possibilities for using mobile phones securely are actually used in practice.
Purchasing
If mobile phones provided by the company or the government agency are used frequently and for different official purposes, it may make sense to set up a pooled storage facility for these telephones.
Implementation
Safeguard S 4.114 Use of the security mechanisms provided on mobile phones provides an overview of the most important security functions of these devices.
Operation
A controlled and reliable use of mobile phones requires the implementation of a number of safeguards, including safeguarding the power supply and, if required, protection against caller identification. If the device is used for transmitting data, a couple of specific safeguards must also be taken into consideration in order to guarantee secure functionality on the one hand and, on the other hand, to provide protection against misuse. If the telephone is lost, the SIM card of this telephone should be blocked immediately in order to avoid misuse and unnecessary costs.
Contingency Planning
Safeguard S 6.72 Precautions relating to mobile phone failures describes important precautions the user may take in order to provide protection against failure or loss of a mobile phone.
In the following, the bundle of security safeguards for the use of mobile phones are presented.
Planning and design
| S 2.188 | (A) | Security guidelines and rules for the use of mobile phones |
| S 2.190 | (Z) | Setting up a mobile phone pool |
Implementation
| S 4.114 | (A) | Use of the security mechanisms provided on mobile phones |
Operation
| S 2.189 | (A) | Blocking of the mobile phone in the event of its loss |
| S 4.115 | (B) | Safeguarding the power supply of mobile phones |
| S 4.255 | (A) | Use of the IrDA interfaces |
| S 5.78 | (Z) | Protection against mobile phone usage data being used to create movement profiles |
| S 5.79 | (Z) | Protection against call number identification during use of mobile phones |
| S 5.80 | (Z) | Protection against bugging of indoor conversations using mobile phones |
| S 5.81 | (B) | Secure transmission of data over mobile phones |
Contingency Planning
| S 6.72 | (C) | Precautions relating to mobile phone failures |

