S 1.79 Formation of security zones
Initiation responsibility: Planner, Head of Internal Services, IT Security Officer
Implementation responsibility: Internal Services
The protection requirement of rooms in a building depends on their use. The required security safeguards must be adapted to this protection requirement. The constructional design of walls, windows and doors as well as the supplementary provision of safety and monitoring technology must be made correspondingly. When planning a new building or evaluating an existing building, rooms with similar protection requirements should be grouped in zones. This allows for uniform treatment of comparable risks as well as for reduction of the costs for implementation of safeguards.
So that it is not necessary to permanently lock or monitor each individual room in the building, zones having visitors should be separated from areas that have protection requirements. Public rooms such as a canteen, attracting external persons, or semi-public rooms such as meeting rooms, training rooms or event rooms should be located close to the entry of the building. Then it is possible for a gatekeeper, for example, to monitor access to the building parts with internals areas such as offices. Particularly sensitive areas such as a development department, rooms of building services or IT rooms should be protected by an additional access control.
For physical protection of a building and, if applicable, of the surrounding property, planning and implementation of a protection concept with multi-level security measures (layered principle) has proved to be successful. A proven method is the division into four security zones - external area, controlled internal area, internal area and high-security area:
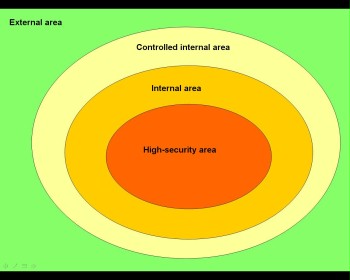
Figure: Security zone model
Security zone 0, i.e. the external area, is surrounded by the property's border. If possible, this legal border should be visually emphasised by a fence. Here, first access and entry control can be performed. Public building areas should be allocated to this zone.
Security zone 1 is the controlled internal area. An appropriate access control, e.g. by a gatekeeper or an access control system, ensures that only authorised persons (employees, invited visitors) will be granted access to this zone. In case of high protection requirements, this zone should already have the requirement to wear ID cards that are always visible. The outer shell of zone 1 (outer shell of building) should be protected against sabotage and burglary by constructional and technical measures.
Zone 2, being the internal area, can only be accessed by a limited amount of authorised persons. Here, defined access authorisations are applicable. Rooms and building sections of zone 2 should only have one entry, respectively. Further entries must only serve as escape and rescue routes and must always be closed during operation. They must be monitored permanently and must be secured by electromechanical security devices (escape route safeguarding systems) to prevent misuse.
Zone 3 is the high-security area (e.g. management areas, critical IT rooms). The number of authorised persons is very limited. The security safeguards should be correspondingly high. Example: Access is only possible via a security gate with two-factor authentication and separation; leaving is possible with one-factor authentication and separation. If access is balanced as soon as no more persons are reported as being present, the burglar alarm will be activated automatically.
Mail rooms, delivery zones and loading zones should be located in security zone 1. Their design should allow for acceptance of deliveries without the supplier being required to access further areas of the building. The doors of these areas should not be open for a longer period. In case of higher protection requirements, it should only be possible to open either the external door or the door to the internal areas. Incoming deliveries should already be checked at the delivery zone for any possible connected risk (see S 2.90 Checking delivery). This kind and extent of checking depends on the corresponding risk potential (e.g. letter bombs). Incoming and outgoing deliveries should be stored separately from each other as far as possible.
Review questions:
- Has a security zone concept for building and property been developed and documented?

