S 2.73 Selecting suitable basic structures for security gateways
Initiation responsibility: Head of IT, IT Security Officer
Implementation responsibility: IT Security Officer, Administrator
After a security policy has been drawn up for the security gateway, a decision must be taken as to the components with which the security gateway will be implemented. A suitable configuration must be selected.
Basic structures of security gateways
Essentially, there are two recommended basic structures that can serve as a starting point for setting up a security gateway. The basic structures are explained below.
1. Packet filter - Application Level Gateway - packet filter (P-A-P)
Under this basic structure, a packet filter, an Application Level Gateway (ALG) and a second packet filter are arranged "back-to-back", so that all data traffic has to cross all three components. For example, the diagram below illustrates several possible ways of setting up a "Demilitarised Zone" (DMZ), in which other components of the security gateway can be operated in a protected environment.
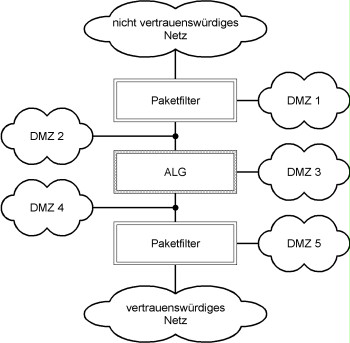
Figure 1: multi-layer structure consisting of packet filter - ALG - packet filter
This type of security gateway is above all used to segregate two networks that differ significantly as regards the trust level (e.g. to segregate the internet from an intranet) or to segregate two subnetworks in the internal network that have very different security requirements.
The two packet filters do not necessarily have to be dedicated IT systems (computers or appliances). If the routers used possess integrated packet filter functionality, then the routers can take on the function of packet filter in the security gateway.
However, often the packet filter functionality provided in routers is somewhat restricted, so that in certain operational scenarios a dedicated packet filter can be necessary.
2. Only packet filters
The simplest security gateway consists of just one packet filter.
The basic problem in filtering communications simply by means of a packet filter is that the decision as to whether access should be allowed or denied is made on the basis of the data contained in the headers of the various IP-based protocols, which is easy to falsify.
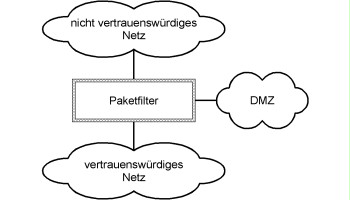
Figure 2: single-layer structure consisting of one packet filter
This structure is used primarily as follows:
- to segregate two networks which differ only slightly as regards the trust level (e.g. to segregate the internet from an intranet that has only low protection requirements);
- to segregate two networks within the organisation;
- private area (protection of the "native" computer during access to the internet).
The use of an additional IP proxy can prevent information in the IP header, such as the IP ID or the "Time-To-Live" (TTL), from leaving the trusted network. With the IP ID it is possible, despite network address translation for the number of computers in a trusted network to be determined, and the TTL gives clues as to the operating systems used. Packet filter rules or appropriate routing must be used to ensure that the IP proxy cannot be circumvented.
Advantages and disadvantages of the basic structures
In principle, the P-A-P structure presented above is recommended as a way of achieving a high level of security in all application contexts. If components of this structure are dispensed with, there is always a downside in terms of lost security.
The table below describes the advantages and disadvantages and the operational environments both for the P-A-P structure and also for the individual packet filters.
| Packet filter - ALG - packet filter (P-A-P) | Packet filter |
|---|---|
|
|
Table 1: advantages and disadvantages of the P-A-P structure compared with packet filters
Proxy processes (often also referred to as proxy servers) run on the application gateway. These establish the connection with the destination computer after the user has been authenticated and filter the data in accordance with the application layer information. Connections without proxy processes are not possible.
Computers on which individual components of the security gateway are implemented have to be configured in such a way that only those programs which are absolutely essential run on them (minimal system). The programs used must be correctly configured and all known weaknesses must be eliminated.
If several systems are used in series to achieve a high level of security, it is strongly recommended to implement these systems on different systems (e.g. involving multiple operating systems). This will ensure that it is not possible for an attacker to get past the security gateway particularly easily by exploiting the same security gap on all the systems involved.
Information on the selection of a basic structure
The question of which type of security gateway should be used depends on the one hand on the difference in trust level of the networks to be segregated (i.e. "how little trusted" the non-trusted network is) and on the other hand on how great the protection requirement of the network that is to be protected by the security gateway is.
In this context, the internet is the network that is the least trusted of all. If the organisation's own network is to be connected to the internet, then generally the multi-layer P-A-P structure should be chosen. Only in exceptional cases can one depart from such a structure, for example, in the case of very small networks in which a multi-layer security gateway would constitute a disproportionately high expense, or where the organisation's own network has only a low protection requirement. However, even in such cases at least one packet filter must be used, and this must be configured with extreme care.
If the less trusted network is "only slightly untrustworthy", the networks do not need to be segregated using a multi-layer security gateway. In this case, a carefully configured packet filter will generally be sufficient.
Examples of networks which can be viewed as "only slightly untrustworthy" might be:
- other internal networks/networks internal to the organisation
- networks that are not connected to the internet
- networks that are connected to the internet but are compartmentalised from the internet by means of special security safeguards (e.g. through a separate security gateway).
The following table summarises the recommendations:
| Application | Recommended structure |
|---|---|
| Segregation of two subnetworks on the internal network with the same protection requirement | Packet filter. For normal protection requirements, a router with integrated packet filter function will be sufficient. |
| Segregation of two subnetworks of the internal network that have different protection requirements (especially: subnetwork with high protection requirements and subnetwork with normal protection requirements) | As a minimum, packet filter.If access is required from the less trusted network to a service on the network that has the high protection requirement, then it is recommended that this access is protected with an ALG. |
| Segregation of a subnetwork with special security requirements from another internal network | Multi-layer structure consisting of packet filter - ALG - packet filterIn this case, a supplementary security analysis is additionally required.The multi-layer structure can serve here only as the basis for very high security. Generally, additional safeguards will be necessary, for which, however, it is not possible to make any general recommendations. |
| Segregation of the organisation's own network from the internet | Basically, multi-layer structure consisting of packet filter - ALG - packet filter.In exceptional cases (very small network, low protection requirement) a packet filter (e.g. in combination with a NAT router) may be sufficient.For services like e-mail and HTTP, it is strongly recommended that an appropriate proxy server is used, as a minimum.Where the protection requirement is normal, it may be possible to dispense with the inward-facing packet filter.If a P-A-P structure is not chosen, it is strongly recommended that an additional risk assessment is carried out. |
Table 2: recommendations for basic structures
Other structures
In addition to the structures described thus far, other structures that generally result from dispensing with components in the P-A-P structure are also possible. However, this is always at the expense of some of the security.
For example, occasionally the "inward-facing" packet filter, which segregates the ALG from the trusted (or internal) network, is dispensed with. However, since most routers already offer integrated packet filter functionality and the cost of an appropriately equipped computer is comparatively low, there are no convincing reasons for dispensing with one of the packet filters.
Appliances
A number of vendors offer security gateways as appliances. These are pre-configured devices which are partly constructed from normal computer components and run under a conventional operating system adapted to this purpose, but are built and configured solely for a precisely predefined end use (i.e. as packet filter or ALG). The bandwidth of the equipment offered ranges from pure packet filters to multi-layer solutions that integrate several components of a security gateway into a single device.
Compared with a security gateway that is constructed out of "normal" computers (either operated by the organisation or through a service provider) that are appropriately configured, appliances often have the advantage of a simpler configuration. On the other hand, most of them have the disadvantage that the configuration is less flexible and there is less scope for tailoring to individual requirements.
Appliances that operate several functions (e.g. packet filter and ALG) under a single operating system installation have the further advantage compared with the security gateway that is implemented through three separate systems that an attacker only has to get past the security mechanisms of a single operating system in order to compromise the security gateway completely. This aspect must be considered when planning the security gateway. If an appropriate device is nevertheless to be used, then it may be necessary to take additional security safeguards to achieve the desired security level.
Documentation
The decision to go for a particular structure should be documented in a traceable manner, together with the critical reasons behind the decision.
Review questions:
- Have suitable structures for the security gateway been selected on the basis of the security policy?

