S 2.161 Development of a cryptographic concept
Initiation responsibility: IT Security Officer
Implementation responsibility: IT Security Officer
Today, companies and government agencies depend more and more on their information infrastructure. For this reason, security services which go beyond mere encryption are required and must be integrated into an overall system.
Due to the diversity of cryptographic problems and different influencing factors, there are also manifold approaches to solutions and implementation options. One must not assume that there is one solution that can be used to eliminate all security problems in computer networks and/or communication systems. Rather, coordinated interaction of suitably selected components is important in order to reach the required level of security. Therefore, it is necessary to develop a cryptographic concept that is integrated into the security policy of the government agency and/or company.
In so doing, the selection of suitable cryptographic components must be based on this policy. Key management is a critical element in the entire encryption concept. Concepts and approaches to solutions can only be drawn up successfully and implemented in a targeted manner if it is made clear which specific security functions and/or security services are needed. Furthermore, there is a host of system-relevant questions and aspects not specifically covered by the field of security technology. For example, these include performance requirements, system connection or interoperability requirements, and default conformity requirements.
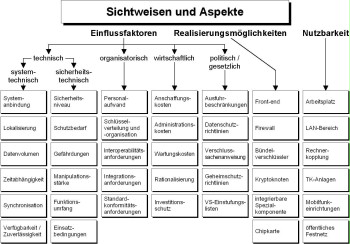
Figure: Perspectives and aspects
In networked IT infrastructures, it is no longer sufficient to guarantee the security of a single domain. Rather, the security of all involved end devices and transmission systems must be coordinated. This coordination is particularly difficult in such cases where these do not only include networked devices within a single organisational unit (e.g. LAN environment), but a network of IT installations with different spheres of responsibility and fields of application.
The use - but also the functionality and technological design - of an IT security system depends on numerous influencing factors, e.g. localisation, level of security, frequency and extent of application, constituting important basic and decision-making conditions for security management. Furthermore, the technical options for implementing and designing a security system are manifold, e.g. integrated into an application on the workstation computer, into a firewall, or as a special component for network components such as switches and routers. An affordable price level for an encryption product can only be achieved by a cross-sectional availability. For example, a standardised system connection, uniform application conditions, etc. play an important role in this regard. A final point refers to the interaction of the security services at different logging layers. The security services of the higher logging layers (according to OSI reference model) normally only provide sufficient protection if the lower layers also provide for protection (see S 4.90 Use of cryptographic procedures on the various layers of the ISO/OSI reference model).
Furthermore, it is important to define a encryption policy specific to the organisation. In doing so, the following must be clarified from a management point of view:
- which protection requirements and/or which level of security must be attained,
- what budget and personnel are available in order to implement the planned security mechanisms and - very importantly - to also guarantee operations,
- which system connection is aimed at and/or which application conditions prevail for security components,
- which scope of functions and services is to be targeted, and
- who will ultimately be responsible.
Furthermore, the technical and/or organisational use of the cryptographic products must be described in the cryptographic concept, e.g.:
- who will be granted which access rights,
- which services are offered remotely,
- how is the management of passwords and keys to be handled with regard to the period of validity, the use of characters, length, granting,
- whether, when, and how the data must be encrypted or signed,
- who is allowed to communicate with whom in a cryptographically protected and/or unprotected manner,
- who is allowed to grant certain rights, etc.
Depending on the system-related basic conditions regarding
- the data volume to be considered and the time dependency,
- the availability requirements and the threat scenario, and
- the type and frequency of applications to be protected, etc.,
suitable implementation options can be analysed based on the aforementioned and specific fields of application such as a PC workplace, in the LAN area, or in connection with a PBX system can be planned and designed technically. Such a holistic perspective is the only way to compile decision-making bases and conditions for cryptographic products, the use of which is both appropriate from a security point of view and reasonable from an economic point of view. However, it should be pointed out that the classification made is by no means mandatory or of fundamental importance, but helpful at best. The only important thing is that the scope of questions consistently reflects the idea regarding a clarification of the initial situation that is as comprehensive as possible. Naturally, in practice, interactions and dependencies between some questions and/or answers result which generally provide a contribution to completing the overall picture, however.
The diverse influencing variables regarding the use of cryptographic procedures must be defined and documented in a comprehensible manner (see S 2.163 Determining the factors influencing cryptographic methods and products). Then, a suitable approach for their use must be developed and documented. Ultimately, the Top Management must issue an implementation order.
The results should be collected in a cryptographic concept in such a way that they can be updated and extended. One possible structure of a cryptographic concept is outlined in the following table of contents, for example:
Table of Contents cryptographic concept
- Definitions
- Cryptographic procedures
- ...
- Threat situation for motivation
- Dependence of the organisation on the database
- Typical threats such as ...
- Organisation-relevant causes of damage
- Damage events in the organisation
- Definition of an internal security strategy for the organisation
- Definition of responsibilities
- Objective, level of security
- Influencing factors
- Identification of the data to be protected
- Confidentiality requirements of the data
- Integrity requirements of the data
- Availability requirements of the data
- Performance requirements
- Key distribution
- Data volume
- Type of data (local/distributed (LAN/WAN)
- Type of applications cryptographic procedures are to be used for
- Frequency of using the cryptographic procedure
- Requirements regarding the resistance of the algorithms and/or procedures (manipulation resistance)
- Ability of the backed up data to be restored
- Required personnel
- Required functionality
- Costs, including consequential costs (maintenance, administration, updates, etc.)
- Know-how/data processing-specific qualifications of the IT users
- Definition of the use
- Type of cryptographic procedures
- Application conditions for the cryptographic products
- Frequency and time of use
- Appointment of persons in charge
- Definition of the organisational regulations
- Performance of personnel measures (training, substitution arrangements, commitments, role assignment)
- Documentation of the application conditions / configuration
- Interoperability, default conformity, investment protection
- Key management
- Individual aspects of this concept are described in more detail in the safeguards S 2.162 Determining the need to use cryptographic procedures and products, S 2.163 Determining the factors influencing cryptographic methods and products, S 2.166 Provisions governing the use of crypto modules, etc.
- The process of drawing up a cryptographic concept is not a once-off task, but a dynamic process. Therefore, a cryptographic concept must be adapted regularly to the current circumstances.
Individual aspects of this concept are described in more detail in the safeguards S 2.162 Determining the need to use cryptographic procedures and products, S 2.163 Determining the factors influencing cryptographic methods and products, S 2.166 Provisions governing the use of crypto modules, etc.
The process of drawing up a cryptographic concept is not a once-off task, but a dynamic process. Therefore, a cryptographic concept must be adapted regularly to the current circumstances.
Review questions:
- Is there an up-to-date cryptographic concept? Is the cryptographic concept integrated into the security policy of the organisation?
- Is the cryptographic concept integrated into the security policy of the organisation?
- Does the cryptographic concept contain descriptions of the technical and organisational use of cryptographic products?
- Are all relevant IT components and communication links included in the cryptographic concept?
- Is the cryptographic concept regularly adapted to the current circumstances?

