S 2.276 Functional description of a router
Initiation responsibility: Head of IT, IT Security Officer
Implementation responsibility: Administrator
In large networks, the use of routers may be relinquished. Routers are used both in LANs and in WANs (see also module S 4.4 VPN). Without the use of routers, the internet would not be functional.
Routers are able to support different protocols (e.g. IP, IPX) and topologies (e.g. Ethernet, Token Ring, FDDI, ATM, Frame Relay, ISDN) at the same time. Thus, routers are able to seamlessly connect LANs to WANs. If nothing else, this function of routers contributed to the rapid development of the internet in the past.
A router has two main tasks. On the one hand, an appropriate connection between the source system and/or network and the destination system and/or network is determined and on the other hand data packets are transported along this connection. If the destination system (network) is connected directly to the router - i.e. router and destination system are located in the same subnet - the data packet sent by the source system is sent directly to the destination system.
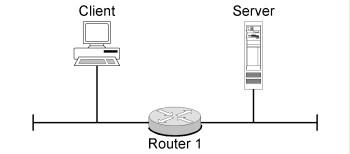
Figure: Routing
If the destination system (network) is not connected directly to the router, the router sends the data packet to an adjacent router connected closer to the destination system (network), the so-called next hop. The last router in this chain of links is always connected directly to the destination network and sends the data packet to the destination system.
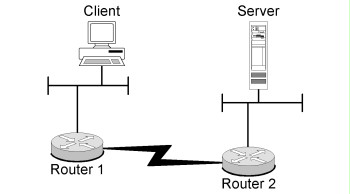
Figure: Routing
The task of a router is to either directly transfer incoming data packets to the addressed recipient or forward them to the next network. The so-called routing metric decides which network the data packet is forwarded to if it cannot be delivered directly. The metric is a measure for the quality of the connection between sender and/or router and the destination of the packet. The router uses the metric to decide which next hop it transfers the packet to. Routing metrics do not exclusively refer to the length of the route between sender and recipient, but may also incorporate other features such as the quality of the lines, the bandwidth, or the utilisation into their decision, for example. The criteria applied depend on the routing protocol used.
The routing information is administered in so-called routing tables. Routing tables contain information as to which adjacent routers may be used as next hop for certain destination networks. Routers make the decision as to which next hop a received data packet is forwarded to based exclusively on these routing tables. Therefore, it is particularly important to protect these tables against manipulations. A host of attacks exploiting the manipulability of routing tables are known. The following figure illustrates the content of a routing table by way of example.
| Destination | Next hop | Hop count |
|---|---|---|
| 210.23.125.98 | 210.23.122.4 | 3 |
| 127.200.45.123 | 5 | |
| 203.2.67,187 | 8 | |
| ... | ... | ... |
Table: Exemplary excerpt from a routing table
In this example, the router would forward a packet with the destination address 210.23.125.98 to the next hop 210.23.122.4. The so-called hop count specifies how many intermediate stations the packet must pass in order to arrive at its destination using the corresponding next hop. If several adjacent routers are available as next hops for a certain destination, the hop count may be used as a routing metric in order to determine the "most favourable" next hop. The hop count is also used as routing metric for the RIP routing protocol.
Static and dynamic routing
Regarding routing, a differentiation between static and dynamic routing is made. These two methods differ in terms of routing table administration.
For static routing, these tables are maintained manually with the help of system commands.
For dynamic routing, the routing tables are maintained automatically. This is performed with the help of routing protocols. Here, we differentiate once more between the Interior Gateway Protocols (IGP) and the Exterior Gateway Protocols (EGP). IGP is used in networks under one's own administration responsibility. The summary of networks operated independently is also called routing domain. With the help of EGP, routing information is exchanged between different routing domains.
The following figure illustrates this:
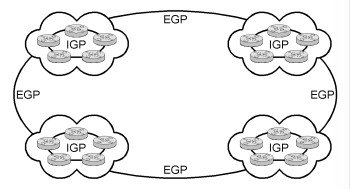
Figure: Exchange of routing information
The most popular and standardised routing protocols include the Routing Information Protocol (RIP), Open Shortest Path First (OSPF), and the Border Gateway Protocol (BGP), with the Border Gateway Protocol being an Exterior Gateway Protocol. These protocols are enhanced by proprietary routing protocols of different manufacturers. The most popular protocols include the Interior Gateway Routing Protocol (IGRP) and the Enhanced Interior Gateway Routing Protocol (EIGRP) of the manufacturer Cisco.
Since routing protocols automate the administration of routing tables, attackers have long since learned to exploit security gaps of these protocols in order to modify the routing tables and to redirect data packets or decommission entire networks this way (see T 5.51 Abuse of routing protocols).
When implementing dynamic routing between two networks, the security functions of the routing protocols used must be taken into consideration predominantly (see S 5.112 Security aspects of routing protocols). The administrator must attach particular importance to the secure authentication of the adjacent routers when exchanging routing tables. Only those routing protocols that support encrypted authentication when exchanging routing tables should be used.
The time required for manually maintaining routing tables is too long to be able to dispense with dynamic routing in complex networks. The use of dynamic routing from a security point of view must be evaluated before commissioning .
In general, no dynamic routing should be used in networks with high protection requirements, if possible. If dynamic routing must be implemented for important reasons, at least only those routing protocols offering secure authentication of the participating devices and secure transmission of the routing information should be used.
S 2.278 Typical operational scenarios in which routers and switches are used describes another scenario where the use of routing protocols is advised against.
Routers as packet filters
Many routers may also be used for filtering data packets, i.e. the router is used as packet filter (see module S 3.1 Security gateway (firewall)).
Broadcast packets are not normally transported between different connected networks by a router. As a result of this, the router divides the connected networks into different broadcast domains.
However, routers are usually equipped with advanced filter functions. For example, so-called access control lists (ACL ) can be configured. The router uses these lists in order to control data traffic between the participating networks. Advanced security aspects for access control lists can be found in S 5.111 Configuration of access control lists on routers.
The use of packet filters is usually insufficient as the only method for controlling data traffic between networks with different protection requirements. More information can be found in module S 3.1 Security gateway (firewall), for example in S 2.73 Selecting suitable basic structures for security gateways and S 2.74 Selection of a suitable packet filter.
Routers as VPN gateway
Some routers available on the market support the Virtual Private Network (VPN) function. These routers are specifically used if sensitive data is transmitted using a network. The use of routers with VPN functionality has the advantage that no encryption mechanisms must be present on the application side. Encryption is transparent for the communication partners. Communication on the link as far as the first encrypting network switching element, however, takes place without encryption, and therefore holds a residual risk. Authentication is only possible between the switching elements. The actual communication partners are not authenticated (S 5.68 Use of encryption procedures for network communications).
Review questions:
- Are only those routing protocols that support encrypted authentication used for dynamic routing when exchanging routing tables?
- Has the use of dynamic routing been evaluated from a security point of view before commissioning?
- Is no dynamic routing used in networks with high protection requirements, if possible?
- Has the residual risk of unencrypted transmission up to the first network switching element been analysed and evaluated when using VPN?

