S 2.338 Creating target group oriented security policies
Initiation responsibility: IT Security Officer, Top Management
Implementation responsibility: IT Security Officer
Conveying security topics to the right target groups
An important factor for successfully reaching an adequate level of security is responsible and competent employees who are able to work together in a co-ordinated fashion. Management, IT users, administrators, and security experts all have different qualifications in different areas of expertise and perform different tasks in this context. While the management of the company or government agency bears overall responsibility, sets goals, and defines general conditions, the administrators must be highly qualified technically and possess detailed knowledge in order to operate and securely configure the systems.
Using the IT-Grundschutz Catalogues, the people responsible for security are able to create a comprehensive security concept. The security concept is often many pages long when it is intended to cover all areas of information security. The preparation and communication of the contents of the security concept for specific target groups is an important task of security management. The goal is to ensure that all employees know which security aspects affect them and their area of responsibility and what precautions they should take.
It is therefore recommended to create different security policies or detailed security subconcepts that represent individual security issues as needed. This enables employees to obtain exactly the information they need on a certain subject.
Separate security policies for IT systems or services that are located in an area critical to security, whose configurations are complicated, or that are difficult to use may contain technical instructions for administrators that normal users will not understand. In the documents for the employees, though, the security topics should be prepared appropriately and not contain any unnecessary details.
Hierarchical structure of policies
When formulating the policies, experience has shown that is best to work at different levels.
In the first level, the general security objectives and the security strategy should be formulated briefly and concisely in a policy for information security (see S 2.192 Drawing up an information security policy). The strategy does not contain any technical details and must be approved by management. In the next level, basic technical security requirements should be derived from the strategy designed in the first level.
The general security concept should include documents describing the various aspects of information security (e.g. a policy for using the Internet or a virus protection concept) but should not mention any specific products.
In the third level, technical details, specific safeguards, and product-specific settings are described. This level contains numerous documents that are changed regularly and are usually only read by the experts responsible.
The following figure shows the structure described above graphically.
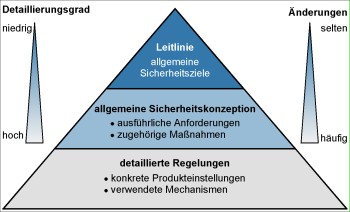
Figure: Hierarchical structure of policies
Contents of special security policies
The following topics are suitable topics to be handled in special security policies for specific target groups, for example:
- codes of conduct and security notes for IT users
- codes of conduct and security notes for administrators
- security gateways (see also S 2.70 Developing a concept for security gateways)
- virus protection (see also S 2.154 Creating a security concept against malware)
- contingency planning (see also S 6.3 Development of an Emergency Procedure Manual)
- data backups (see also S 6.33 Development of a data backup policy)
- archiving (see also S 2.243 Development of an archiving concept)
- use of Groupware (see S 2.455 Defining a security policy for Groupware)
- outsourcing (see S 2.251 Specification of the security requirements for outsourcing projects)
Security policy for IT usage
It is recommended in many cases to specify the general objectives of the policy for information security in more detail in a security policy for IT usage and summarise the most important organisation-wide safeguards of the security policy in a guideline that does not contain any technical details and that can be understood by everyone. This guideline describes the basic rules for the use of IT throughout the organisation and guides the employees through the security concept.
The following subjects could be handled in a general security policy for IT usage:
- handling information requiring protection (specification of information owners, the duty to classify information according to the level of protection it needs)
- relevant laws and regulations
- short descriptions of important roles (e.g. the IT Security Officer, administrator, users)
- training of the personnel
- duty to arrange for a substitute
- IT administration requirements (purchasing, usage, maintenance, auditing, and disposal)
- basic security safeguards (access to rooms and access to IT systems, encryption, virus protection, data backup, and contingency planning)
- regulations for specific IT services (data transmission, Internet usage)
The BSI offers various sample policies and concepts as examples on its web site in the IT-Grundschutz section.
Review questions:
- Are security policies tailored to specific target groups by representing relevant security issues as needed?

