S 2.343 Protection of SAP systems in a portal scenario
Initiation responsibility: Head of IT, Head of Development, IT Security Officer
Implementation responsibility: Developer, Administrator
SAP systems are being used more and more often in portal scenarios. In the following, it is assumed that the portal is an internal government agency or corporate portal used to access an SAP system. This safeguard does not address the security of the government agency or corporate portal and instead addresses the security of an SAP system located in the environment of the portal. The corresponding safeguards for SAP systems in internet scenarios can be found in S 2.344 Secure operation of SAP systems on the Internet. Access in portal scenarios is generally obtained using HTTP, and users obtain access through a browser.
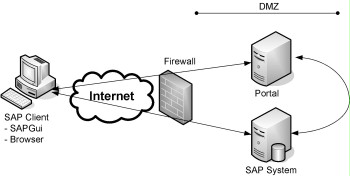
Figure: SAP system in the portal scenario
In portal scenarios, it is often incorrectly assumed that the portal used accesses the "downstream" SAP system. Direct access to the SAP system by the users would not be necessary in this case. In general, though, the portal only redirects the user queries to the SAP system so that the SAP system is actually queried directly. This often happens without the user even noticing it, since the data displayed in the browser is shown in a frame of the portal page called. For this reason, safeguard S 2.344 Secure operation of SAP systems on the Internet is also relevant for portal scenarios.
The following basic aspects are generally important for SAP systems in portal scenarios:
- Architecture of the network and the system design (see also S 2.341 Planning the use of SAP)
- Securing communications (see also S 5.125 Protection of communication with SAP systems)
- The security of applications when used in the internet
- Detection of attacks (intrusion detection systems)
- Protection against viruses when uploading or downloading files (see also S 4.271 Computer virus protection for SAP systems)
Special consideration must be given to the following aspects, which are derived directly from the portal scenario:
Restricting system accesses
All SAP systems to be accessed through a browser must be accessible to the users. This fact must be taken into account when performing the risk analysis and affects the position of the SAP system in the network as well, for example because it needs to be placed in the DMZ (demilitarised zone).
Access to the affected SAP systems must be restricted by a firewall to the ports used to process HTTP and/or HTTPS requests only. Depending on the scenario, access to the SAP system should pass through a reverse proxy so that the SAP system is not accessed directly.
Restricting dialogue accesses
In general, SAPgui access should only be allowed to a limited extent for the SAP systems accessed via the portal. In particular, access using the SAPgui must be prohibited for users who only access the portal using a browser. It is possible in this case to assign the "internet user" user type to these users when access to the port is not blocked by the firewall. In general, it must be possible for administrators to access the SAPgui, which means the firewall must be configured accordingly. It is also possible to use a separate administration network as an alternative.
If the Internet Transaction Server (ITS) is not used to access the SAP system, ITS access should be disabled, since it offers access to the SAP system that is similar to SAPgui access. An ITS component needs to be installed as a separate component (WGate, AGate) when using version 6.40 or older versions of the SAP Web Application Server. If this is the case, these components should not be installed or should be uninstalled.
Version 6.40 and higher of the SAP Web Application Server integrates the ITS so that the corresponding services need to be disabled in the ABAP stack (e.g. webgui) and Java stack (e.g. mi or me). They are disabled in the ABAP stack by disabling the ICF service "webgui" (see also S 5.127 Protection of the SAP Internet Connection Framework (ICF)). In the Java stack (see also S 4.266 Secure configuration of the SAP Java Stack), the applications "mi" and "me" must be disabled using the deploy service.
Authentication/single sign-on
Single sign-on is configured generally for the portal and the SAP system. For this reason, it must be ensured that accounts with the same name in both systems are assigned to the same person. If this cannot be ensured, the user mapping mechanism of the portal must be used.
The account information stored is used in this case when accessing the SAP system. In this case, it must be ensured that the user mapping information is consistent.
Authorisations
In portal scenarios, it is possible for situations to arise in which applications that run in the portal (front-end applications) can access the SAP system directly. Depending on the design of the application, a technical account or the account of the user currently logged in is used to obtain access. In the SAP system, this account must only be allowed to call those ABAP function groups needed for the portal application.
In general, it must be ensured that the authorisations of the users maintained in the SAP system are specified so that they are only granted the minimum authorisations necessary. When planning, it should also be assumed that it is possible to circumvent the authorisation check performed by the front-end application. If the portal only redirects the users, the users access the SAP system directly. For this reason, the authorisations in the SAP system should always be configured in such a way that only those functions can be called that are allowed by the portal application. This is especially important when portal users are able to gain access through a dialogue.
Application session management
All applications of the ABAP and Java stacks that are used via the portal should have secure session management implemented. In particular, the applications must be programmed to ensure that session information expires once a user logs off the portal.
It must be noted that logging out of the portal does not automatically log the user out of the SAP system. This is always a problem when a client computer is used by more than one person, since a subsequent user may be able to access the data of the previous user in the SAP system under some circumstances.
SAP provides programming frameworks (for example Business Server Pages or BSPs) that offer functionality for automatically logging users out of the SAP system. This must be taken into consideration for software developed in-house when deciding which technology or framework will be used to implement the software.
Review questions:
- Have SAP systems that must be available for the users and that are called by redirected browser queries been taken into consideration in the risk analysis?
- Is access to the SAP systems concerned restricted to HTTP and/or HTTPS ports with the help of a firewall in the portal scenario?
- Is dialogue access to the SAP system prevent when it is not needed?
- Has it been ensured that eponymous accounts in the portal and the SAP system are assigned to the same persons?
- Are the authorisations in the SAP system configured in such a way that only those functions can be called that are allowed by the portal application?
- Are the applications used equipped with a secure session management system that also works in portal scenarios?

