S 2.392 Modelling of virtualisation servers and virtual IT systems
Initiation responsibility: Head of IT, IT Security Officer
Implementation responsibility: Administrator, Head of IT
To achieve an adequate level of overall security for IT operations, all virtualisation servers and all virtual IT systems must be taken into account systematically in the security concept. In terms of the IT-Grundschutz methodology, this means in particular that all virtual IT systems must be integrated into the structure analysis and the modelling process.
Modelling in the IT-Grundschutz methodology refers to the assignment of modules to the existing target objects (IT systems, applications, rooms, etc.). In general, the virtual IT systems are modelled according to the same rules as for stand-alone physical IT systems. This means that the information in Section 2.2 of the IT-Grundschutz Catalogues must be taken into account. The IT-Grundschutz modules are assigned primarily according to the function of the IT system (i.e. as a server, client, etc.), the operating system used (Unix, Windows, etc.), and the applications running on the IT system (databases, web servers, etc.).
To facilitate maintenance of the security concepts and reduce their complexity, an organisation should take special care when checking the extent to which the virtual IT systems can be grouped. In principle, it is also possible to place virtual IT systems located on different physical computers together in a single group. However, the ability to do this must be examined on a case-by-case basis. Information on how to form groups can be found in the IT-Grundschutz methodology.
If a fully functional and stand-alone base operating system is operated below the virtualisation layer, then this operating system must be included in the model separately from the virtual IT systems. It is also necessary in this case to check if it is possible to group some of the virtual IT systems together.
Example scenario
As an example, we will consider a physical server S1 on which three virtual servers VM1, VM2, and VM3 are operated with the help of a virtualisation layer. A version of Unix is used as the base operating system on the physical server S1. The virtualisation layer in this example is a software component that runs on Unix, i.e. a host-based server virtualisation (type 2). The two virtual servers VM1 and VM2 are operated using Windows 2003, but Unix is installed on VM3. Applications can be run on the three virtual servers as well as directly on the base operating system of the physical server, Server S1 (by bypassing the virtualisation layer).
The following figure shows a diagram of the configuration in this example:
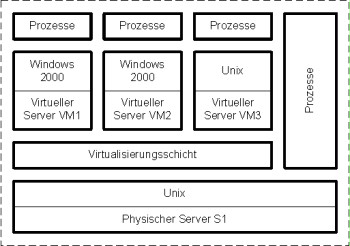
Figure: Diagram of the configuration in the example with three virtual servers
Note: Not all solutions for virtualisation use a base operating system with full functionality below the virtualisation layer.
If the prerequisites for placing VM1 and VM2 in a group are met, then the model for the example scenario presented above could appear as shown below (excerpt):
| Modules | Target object |
|---|---|
| S 3.101 General server | S1 |
| S 3.101 General server | VM3 |
| S 3.101 General server | Group with VM1 and VM2 |
| S 3.102 Servers under Unix | S1 |
| S 3.102 Servers under Unix | VM3 |
| S 3.108 Windows Server 2003 | Group with VM1 and VM2 |
Table: Module to target object assignments
Review questions:
- Is there a plan for the use of virtual IT systems that considers the goals of the use and the effects on the IT risks?
- Is the use of virtual IT systems compatible with the security objectives of the organisation?
- Have the requirements for virtual IT systems in terms of their isolation from each other and availability and throughput been defined?
- Are checks made as to whether adequate response times and/or processing speeds are achieved before transferral of virtual IT systems?
- Has it been specified which applications are based on virtual IT systems?
- Have the effects on the administrative and operational processes on the virtual IT systems been examined?
- Have the effects on the users on the virtual IT systems been examined?
- Are all virtual systems taken into account in the IT security concept?
- Have all virtual systems been included in the IT structure analysis, the definition of the protection requirements, and the modelling process?
- Are the administrators trained in the planning, configuration, and operation of virtual IT systems?
- Are the performance data of the virtual IT systems monitored?

