S 2.501 Data protection management
Initiation responsibility: Top Management
Implementation responsibility: Data Protection Officer, IT Security Officer
Data protection management refers to the processes necessary to ensure the implementation of the legal requirements of the data protection laws when planning, configuring, and operating procedures used to process information, as well as when taking these procedures out of operation. Data protection management is the superior implementation of data protection in an organisation or for large-scale procedures. In the following, a sample process for data protection management to be considered as an exemplary process and suggestion will be described. The process is oriented on the BSI standards 100-1 and 100-2 and must be deemed an integral part of the security process according to IT-Grundschutz, but can also be treated as an independent process if the data protection aspect is to be addressed primarily. For logical reasons, this process is not implemented and operated for individual procedures, but for the entire organisation and all procedures personal data is processed in.
The data protection process
The data protection process is the core of data protection management. Just like the security process, it is designed as a cyclic process in order to be able to continuously ensure compliance with the applicable data protection law in a modified environment. It covers the tasks of an organisation resulting from a strategic, tactical, or operative level. In doing so, the process uses individual safeguards described in the following. The process is designed in such a way that it allows establishment of data protection management even in organisations not yet disposing of any structures for implementing data protection. The following figure illustrates the process:
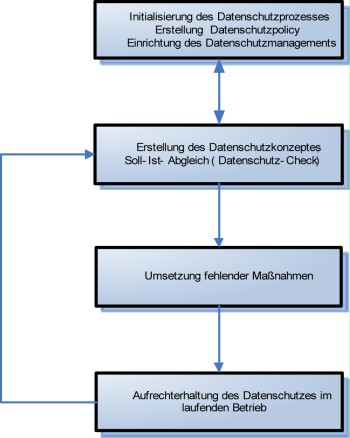
Figure 1: Data protection process
The individual process steps and/or sub-processes are explained below.
Initialisation of the data protection process
This process step contains the safeguards which have strategic objectives (period of validity of up to five years). They include:
drawing up a data protection policy, normally within the framework of a government agency- or company-wide security policy: this policy may formulate the following objectives, amongst other things:
- compliance using minimum efforts or
- data protection as competitive edge ("USP": Unique Selling Proposition)
establishing data protection management, normally within the framework of security management. Important partial aspects include the management of responsibilities (role and function of the Data Protection Officer distinguished from and in collaboration with the Data Security Officer), process definitions, and the provision of resources (personnel capacities).
Creation of a data protection concept
The data protection concept is the equivalent to the security concept (period of validity of up to three years). Safeguard S 2.503 Aspects of a data protection concept is referred to regarding the content.
Implementation of the required safeguards
This process step includes the implementation of the safeguards defined in the data protection concept, but not yet implemented. The safeguards are implemented within the framework of classic project management, including a project and work schedule.
Maintenance of data protection during operation
This sub-process is designed to allow reactions to changes or malfunctions during operation of the procedures personal data is processed in. These mainly include:
- changes to the data protection law
- changes to the IT procedures
- malfunctions regarding the operative procedures to be classified as security incidents
- technical progress and reduced time and expenditure for safeguards not yet implemented.
To this end, a host of sub-processes accompanying the security process is required independently which process and/or resolve changes and malfunctions from a data protection point of view. The results may also involve structural changes to data protection management or updates of the data protection concept, if necessary.
The following figure illustrates the sub-processes in an overview:
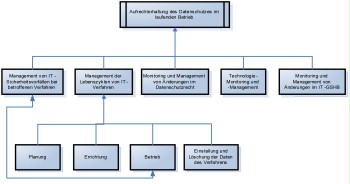
Figure 2: Sub-process regarding the maintenance of data protection during operation
Management of security incidents
The process of managing security incidents for IT procedures during operation must also address the incidents and their consequences in terms of the applicable data protection law, if necessary. Expediently, this is performed in collaboration with the IT Security Officer heading the security incident team. The tasks of accompanying data protection management may include:
- prioritisation of technical and organisational measures for problem analysis and solution and/or preservation of evidence from data protection points of view
- addressing legal aspects from data protection law points of view.
From a process integration point of view, it makes sense that the security process triggers the corresponding data protection management and/or starts the corresponding sub-process. In practice, this may mean that the Data Protection Officer automatically becomes a member of the security incident team in the event of security incidents relating to procedures personal data is processed in, for example. This way, the Data Protection Officer can be optimally involved in the information and processes. This management also includes a description as to where and/or by whom data protection incidents are managed in the company or government agency.
Management of the lifecycles of IT procedures from data protection points of view
Within the framework of managing the lifecycles of IT products and procedures, a lifecycle model is used based on the general lifecycle model of the BSI standards and the IT-Grundschutz Catalogues.
In the respective phases, a series of safeguards from module S 1.5 Data protection must be taken into consideration. These safeguards include:
- when planning and designing: S 2.501 Data protection management to S 2.505 Definition of technical/organisational safeguards according to the state of the art for processing of personal data
- when implementing the planning and the concept up until operation: S 2.506 Obligation/briefing of staff members for the processing of personal data to S 2.512 Regulation of linkage and usage of data regarding the processing of personal data
- when operating: S 2.513 Documentation of admissibility regarding data protection to S 2.515 Deletion/destruction in compliance with data protection
- upon configuration up to permanent deletion of the procedure and all related data: S 2.508 Maintaining application registers and compliance with compulsory registration regarding the processing of personal data, S 2.110 Data protection guidelines for logging procedures to S 2.515 Deletion/destruction in compliance with data protection
Furthermore, it should be checked when planning and designing new IT procedures whether Privacy Enhancing Technologies (PETs) can be used. PETs technically support the implementation of data protection principles such as data economy, appropriation, or the transparency order. Examples for PETs include protocols such as P3P (Platform for Privacy Preferences) and data anonymisation and pseudonymisation procedures during network transfer, data storage in databases, or Data-Mining (Privacy Preserving Data Mining, PPDM). However, the aforementioned also includes resubmission functions in programs supporting the compliance with deletion periods when storing personal data.
Management of changes regarding the data protection law
Changes to the data protection law must be followed up and assessed regarding their impacts on the procedures personal data is processed in. This sub-process can also be integrated into the government agency- or company-wide monitoring of changes in relevant legislation.
Technology monitoring
Technology monitoring pursues the state of the art referring to information security and data protection, together with the security management. In accordance with the relevant data protection legislation and its application, this sub-process provides impulses for the further development of data protection and security concepts.
Monitoring and management of changes in the IT-Grundschutz Catalogues
Updates to the BSI standards and to the IT-Grundschutz Catalogues, particularly to the data protection module, must be taken into consideration within the framework of general monitoring. Along with impulses for the further development of data protection and security concepts, the interfaces to security management must also be examined and adapted, if necessary.
Summary
The suggested process model offers manifold starting points and therefore synergies to the corresponding security processes of the BSI standards. These synergies may include a cooperation of the processes, the integration of documents (e.g. data protection and security concepts) and documentation, as well as the complete integration of the processes. This may also include the functionaries: an IT Security Officer may assume the role of the Data Protection Officer if he disposes of the adequate specialised knowledge and does not simultaneously perform conceptional and operative tasks in the field of IT (avoiding a conflict of interests). This is of particular importance in small organisations.
The following figure 3 illustrates this schematically:
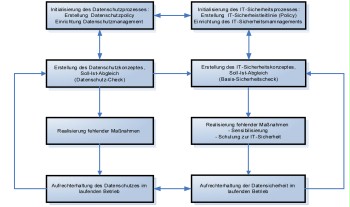
Figure 3: Schematic representation of interactions and synergies between data protection and data security processes
Review questions:
- Is there a current data protection policy?
- Are data protection management and security management aligned?
- Are changes to the data protection law and other general conditions followed up and integrated into the data protection process?

