S 3.23 Introduction to basic cryptographic terms
Initiation responsibility: IT Security Officer, Head of IT
Implementation responsibility: Head of IT, IT Security Officer
The use of crypto products can result in additional effort for the users or, depending on the complexity of the products used, even require in-depth knowledge. Therefore, all employees who are to use cryptographic procedures and products should be made aware of the value and necessity of cryptographic procedures and introduced to basic cryptographic terms. Of course, this applies especially to those who are to create a crypto-concept and/or select, install or support crypto products.
The following text is supposed to provide a basic understanding of the essential cryptographic mechanisms. In the following, examples are used to explain in which situation which cryptographic technique can be used.
Cryptography elements
Mathematical methods and techniques that can be used to protect information against unauthorised acquisition and/or deliberate manipulations are referred to as cryptographic methods and techniques. The protection of information applying cryptographic procedures is in contrast to infrastructural and technical security safeguards of mathematical-logical nature.
For cryptographic procedures, a mathematical arithmetic procedure, i.e. an algorithm, is implemented into a concrete technique. Its efficiency is based on the fact that a potential attacker cannot solve a certain mathematical problem, and this not because of a lack of skills, but due to a lack of knowledge of very specific "key" information.
Cryptographic procedures always refer to the following situation: A sender A (as is usual in cryptography, referred to as "Alice") sends a message to a recipient B (referred to as "Bob") using an insecure channel.
Here, senders and recipients can also be identical; in this case, "channel" refers to any transport medium. When encrypting local data, the sender and recipient are of course identical; in this case, "channel" refers to the storage medium.
Basic cryptographic objectives
Due to theoretical and practical considerations, a distinction is made between four basic cryptographic objectives:
- Confidentiality/non-disclosure: No unauthorised third party E (referred to as "Eve") should be able to access the contents of the message or file.
- Integrity: It should be possible to detect unauthorised manipulations to the message or file (e.g. inserting, omitting, replacing parts).
- Authenticity:
- Proof of identity (authentication of communication partners): A communicating party (e.g. a person, organisation or IT system) must be able to prove their identity beyond doubt to another party.
- Proof of origin (authentication of messages): A must be able to prove to B that a message originates from A and has not been altered.
- Non-repudiation (binding nature): Compared to message authentication, here, the main focus is on verifiability regarding third parties.
- Non-repudiation of origin: It should be impossible for A to deny having sent a certain message to B after the event.
- Non-repudiation of receipt: It should be impossible for B to deny having received a message sent by A after the event.
It is obvious that there are relationships between these objectives, but one basic understanding of modern cryptography is the following: Ensuring confidentiality and/or authenticity are independent basic objectives of a cryptographic system: Authentication limits the group of potential senders of a message, whereas non-disclosure restricts the group of potential recipients.
The essential cryptographic procedure to protect confidentiality is encryption, the essential procedures to ensure integrity, authenticity and non-repudiation are hash functions, Message Authentication Codes (MACs), digital signatures and cryptographic logs. In the following, the individual cryptographic concepts are presented briefly.
I. Encryption
Encryption (coding) transforms a clear text depending on an item of additional information (known as the key) into a corresponding secret text (cipher text or enciphered text), which should not be decryptable for anyone not in possession of the key. The reverse conversion - restoring the clear text from the cipher text - is known as decryption or decipherment. In all modern encryption algorithms, clear texts, secret texts and keys are available as bit sequences in each case.
To be able to be used in practice, encryption algorithms must fulfil the following minimum requirements:
- They should be decipherment-resistant, i.e. without knowing the key, it must not be possible to decrypt the cipher text, the amount of potential keys in particular must be "sufficiently large" for this purpose, as it would be otherwise possible to simply try all keys,
- they must be easy to use and
- encryption/decryption must be "fast enough".
The requirement of decipherment resistance must always be taken into consideration based on the current technical and mathematical possibilities. When assessing encryption algorithms, it is important that it should be virtually impossible at the time of use to decrypt the cipher text without knowing the key, i.e. not using the then available technique within an acceptable period of time.
When A and B want to set up a confidential connection, they proceed as follows:
- they agree upon a ciphering procedure,
- they agree upon a key and/or a key pair,
- A encrypts a message and sends it to B,
- B decrypts the cipher text sent by A.
There are two classes of ciphering procedures:
Symmetric encryption procedures use the same key both for encryption and for decryption. Thus, symmetric procedures are sometimes also referred to as "one-key" procedure, since knowing one key is sufficient to be able to cipher and decipher.
Well-known symmetric encryption procedures are, for example, DES, Triple-DES, IDEA or RC5.
For symmetric procedures, a further distinction is made between stream ciphers and block ciphers.
For stream ciphers, the key is used to generate a bit sequence looking as randomly as possible (a bitstream) that is added to the clear bit sequence (modulo 2). The clear bit sequence is thus encrypted bit by bit (adding key stream bits). For the security of stream ciphers, it is essential that two (different) messages are never encrypted using the same key stream; this must be ensured by means of special safeguards (synchronisation information in the form of a message key). Examples of stream ciphers are RC4 and SEAL.
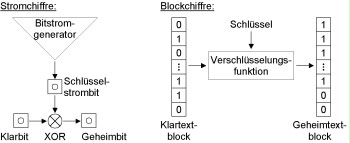
Figure: Ciphering
For block ciphers, however, an entire block of bits is encrypted in every encryption cycle; today, this block usually amounts to 64 bits. Most symmetric encryption procedures are block ciphers; they also include DES, IDEA or RC5. For block ciphers, a number of operating modes are defined (and standardised). These modes include:
- the ECB (Electronic Code Book) mode; in this mode, each block is encrypted separately, i.e. independently from other blocks,
- the CBC (Cipher Block Chaining) mode and the CFB (Cipher Feed Back) mode; in these modes, a dependency of the cipher text blocks on all previous cipher text blocks is created after an additional initialisation vector has been selected, as well as
- the OFB (Output Feedback Modus) mode; this mode can be interpreted in such a way that the used block cipher is used to generate a "block stream" which is added to the clear blocks bit by bit (modulo 2).
When applying symmetric procedures, it must be generally taken into account that the key(s) has(have) been previously exchanged between the communication partners. The keys must be exchanged using a secure channel (e.g. courier, personal handover) and both parties must keep the key secret afterwards. There are different secure key exchange procedures. In closed systems, the keys can be usually exchanged without any problems, since "secure channels" are available in most cases. In open systems with a large number of communication partners, exchanging the keys is more difficult. In general, however, there is the problem that a corresponding number of keys must be exchanged prior to the actual communication if there is a large number of potential communication partners and that the potential communication partners must be known in advance.
Asymmetric (public key) ciphering procedures, however, use two different (but mathematically related) keys: a "public" key for encryption and a "private" key for decryption. Here, the key pair must have the following characteristic: For all persons who know the "public key", it must be virtually impossible to determine the associated "private key" or to decrypt a message encrypted using the "public key".
Asymmetric encryption has thus an "one-way" characteristic: A message cannot be restored if the "private key" was forgotten or deleted.
The designation "public key" encryption is due to the fact that the "public key" can be made public without compromising the security of the procedure. The "private key", however, must be kept secret.
If Alice now wants to send a message Bob in encrypted form, Alice gets Bob's public key from a freely accessible file and encrypts the message using this key. Upon receipt of the message, Bob uses his secret key to decrypt the message received by Alice. When Alice and Bob use an asymmetric procedure for confidentiality purposes, they do not require a secure channel for exchanging the keys, but Alice must be sure that she actually uses Bob's public key and not a false key made available to her as Bob's key If Alice encrypted a message with a false key made available to her, the perpetrator knowing the suitable secret key would be able to decrypt the message. In general, the sender needs the confirmation by a trusted third party that the public key of the recipient actually belongs to the latter. In general, this confirmation, the "certificate", is also generated by a cryptographic procedure and added to the public key.
Two known asymmetric encryption procedures are the RSA procedure (named after the inventors Rivest, Shamir, Adleman) and the class of ElGamal procedures. The last class of procedures also includes encryption procedures based on elliptic curves.
To some extent, symmetric and asymmetric ciphering procedures have complementary advantages and disadvantages:
Advantages of (good) symmetric procedures:
- They are fast, i.e. they have a high data throughput.
- The security is basically defined by the key length, i.e. there should be no attacks if there are good symmetric procedures, which are better than trying all keys (brute-force attacks).
- They offer a high degree of security with a relatively short key.
- The generation of keys is easy, since usually every bit sequence of a fixed length is allowed to be used as key and a random number can be selected as key.
Disadvantages of symmetric procedures:
- Each participant must keep secret all keys of their communication partners.
- For key distribution, they are less suited than asymmetric procedures, especially for a large number of communication partners.
- For confidentiality purposes, they are less feasible than asymmetric procedures, because it cannot be readily noticed when using symmetric keys which of the two communication partners has encrypted the message. This can only be ensured by a third party as intermediary who is involved in the message flow by means of corresponding cryptographic logs.
Advantages of (good) asymmetric procedures:
- Each participant of a confidential communication must only keep their own private key secret.
- They can be easily used for digital signatures.
- They offer elegant solutions for key distribution in networks, as the public keys and/or key certificates can be stored freely accessible on central servers without impairing the security of the procedure.
- They are well suited for non-repudiation purposes.
Disadvantages of asymmetric procedures:
- They are slow, i.e. they have a low data throughput in general.
- Security: For all known public key procedures, the following applies:
- There are considerably better methods of attack than trying all the keys one after the other, which is why (in comparison with symmetric methods) relatively long keys are required in order to achieve an equally high degree of security.
- Security is based "only" on the presumed (but recognised among experts) algorithmic difficulty of a mathematical problem (for example reducing a large number into its prime factors).
- n general, the generation of keys is complex and difficult, since the generation of "weak" key pairs must be avoided.
- In general, the generation of keys is complex and difficult, since the generation of "weak" key pairs must be avoided.
Hybrid procedures try to combine the advantages for both types of encryption: They use asymmetric encryption to transmit a session key for a symmetric procedure and encrypt the mass data applying the symmetric procedure. The session key is usually only used for a session (transmission) and destroyed afterwards. Depending on the circumstances, the asymmetric key pair is used for a long period of time.
II. Integrity protection
The goal of integrity protection is to ensure that a recipient of a message can determine whether they have received this message in an unaltered form. The basic principle of integrity protection is to send the message in an unencrypted and unchanged manner, but, at the same time, to also send along certain control information, allowing the recipient to check the integrity of the actual message. This requires, however, that the recipient receives the control data without any manipulation. Thus, the following conditions must be fulfilled for this control data:
- The scope of the control information must be as small as possible to minimise the information to be transmitted in addition.
- It must be possible to detect virtually any manipulation, even of only an individual bit of the message based on the control information.
- The control information must be transmitted so that it cannot be manipulated and/or it must be possible to detect manipulations.
To calculate the control information, two procedures are typically used: hash functions and Message Authentication Codes.
A (one-way) hash function is a data transformation with the following characteristics:
- Compression characteristic: Bit sequences of any length are converted to bit sequences of a more fixed, generally shorter length (typically 128 - 160 bits).
- "One-way" characteristic: It must be "virtually impossible" to find a message for a specified hash value, whose hash value is the specified hash value.
- Collision resistance: It must be "virtually impossible" to find two messages leading to the same hash value.
Using a hash function known to both communication partners, A and B can check the integrity of a message: Alice hashes her message and transmits it and the hash value to Bob in such a way that the integrity of the hash value is ensured. Bob also hashes the received message and compares his result with the hash value provided by Alice. If both values are identical, he can assume that no bit of the message has been changed.
A Message Authentication Code (MAC) is a cryptographic checksum to protect messages, i.e. it is a data transformation, in which a secret key with the following characteristics is additionally included in the calculation:
- Compression characteristic: Bit sequences of any length are converted to bit sequences of a more fixed, generally shorter length.
- Integrity protection: For anyone who does not know the key, it must be "virtually impossible" to calculate the MAC value of a new message even if they have gained access to several old messages with the associated MAC values.
If Alice and Bob have a MAC and a shared, secret MAC key, Alice authenticates her message simply by calculating the MAC value of the message and sending it together with the message to Bob. Bob, in turn, calculates the MAC value of the received message using the MAC key that is also known to him. If this value is identical to Alice's value, he can assume that the message is authentic (i.e. that it was not changed and actually sent by Alice). Alice has thus authenticated her message towards Bob using the key which is only known to her and Bob.
MACs are often created based on symmetric ciphering procedures. The best-known method is the encryption of a message using DES or another block cipher procedure in the CBC or CFB mode. In this case, the last block encrypted is appended to the message as the MAC. In addition, however, there are also MACs that are not based on ciphering procedures. The MAC value of a message can be considered to be a key-dependent, cryptographic checksum of this message ensuring integrity protection. When applying MACs for authentication purposes,
it is necessary that both parties protect the secret authentication key in a reliable manner. As a side effect of integrity protection, the recipient of the message is able to check at the same time using the procedures outlined above that the message verified to be free from any manipulation could only be sent by the actually known sender. This conclusion can be drawn, since only this sender knows the key required for encryption and/or determining the control information.
III. Proof of authenticity
For the authentication of users towards communication partners/IT systems and/or clients towards servers, the following requirements must be met:
- illegitimate access must be detected and seen off,
- legitimate access must be allowed and
- sensitive data must also remain protected when transmitted via networks.
For this purpose, procedures are required allowing all persons involved to clearly determine the identity of their communication partners. This includes a time aspect: Alice wants to convince Bob in "real time" that she is actually communicating with him. The main technique for this type of authentication are cryptographic challenge response logs.
Here, Bob sends data to Alice and asks her to provide him with proof (challenge), on the possession of a secret (i.e. a key information) and Alice demonstrates this possession to him without disclosing the secret itself by sending him an answer that is dependent on the secret ad his challenge (response). Bob, in turn, checks on the basis of Alice's answer that the correct secret was actually used for the calculation of the answer.
For "strong" authentication, the challenges must not be repeated. For challenge-response procedures, both symmetric and asymmetric techniques can be used.
Example: Alice and Bob agree upon a symmetric encryption procedure and a shared cryptographic key in advance. For authentication, Bob sends a random number to Alice as challenge. Alice, in turn, encrypts this random number using the shared secret key and sends the result back to Bob. In the next step, Bob decrypts the message and compares whether the result is identical to the random number previously selected by him. If they are identical, it is indeed Alice, because only she knows the secret key.
IV. Digital signature
The cryptographic construct of a digital signature serves the goal of being able to use an equivalent to the handwritten signature for digital files and messages. For this purpose, several of the cryptographic procedures explained above such as hash functions and asymmetric procedures are combined. The essential prerequisite for digital signatures is that each participant has only one secret know to them, with which they can create a digital signature for any files. Based on public information, it must be possible to check this digital signature.
In this context, a digital signature constitutes special integrity protection with additional particularities. A digital signature is an item of check information appended to a message or file and associated with the following characteristics:
- A digital signature can be used to unambiguously determine the identity of the person who created the signature, and
- it can be checked authentically whether the file the digital signature was appended to is identical to the file actually signed.
If it is also possible to verify the digital signature based on the publicly accessible information, the integrity of the signed file is ensured on the one hand and the non-repudiation on the other hand, because only the person who can be clearly assigned the digital signature has been able to create this signature based on their secret information. It should be noted that different files can also result in different digital signatures and that smallest changes to the files can result in signatures that cannot be verified.
Example: A widely used procedure for digital signatures is the reverse application of the RSA procedure. In this case, each participant only has one secret signing key known to them. Verification key certificates in which the suitable public key and information on the owner of the suitable secret signing key are linked with each other so that it cannot be altered can be publicly accessed. These certificates are issued by trusted bodies which have checked the participants' personal data in advance.
To calculate and check a digital signature for any file, the following steps are taken:
- Step: Alice calculates the hash value of the selected file.
- Step: Alice encrypts this hash value using the secret signing key only known to her. The result is Alice's digital signature for this file.
- Step: Alice transmits to Bob the digital signature together with the verification key certificate and the file.
- Step: Bob verifies the certificate (e.g. using the public key of a certificate authority).
- Step: Bob calculates the hash value of the received file.
- Step: Based on the public verification key contained in the verification key certificate, Bob decrypts the digital signature.
- Step: Bob compares the hash value calculated in step 4 and the decrypted signature. If they are identical, the digital signature is thus verified. If they are not identical, Bob cannot draw any further conclusions.
- Step: Following the verification of the digital signature, Bob can conclude as follows:
- If it has been ensured that only Alice is in possession of the secret key, Bob can be sure that the digital signature from Alice which is stated in the verification key certificate was generated
- The enclosed file is identical to the file Alice calculated the digital signature for.
It must be stressed that digital signatures only ensure the goals of integrity and non-repudiation, but do not guarantee the goal of confidentiality in no way. A digitally signed message is transmitted in clear text; if it is confidential, it must be additionally encrypted.
If a digitally signed file contains a declaration of intent of the signing person, this declaration of intent can be undeniably attributed to the signing person based on the signature, even before court if necessary.
The used verification key certificates, in turn, are themselves digitally signed files by the trusted body that can be checked analogously and provide information on the verification key and the person having the respective suitable secret signing key.
Please note the differences between MACs and digital signatures:
- The digital signature can be verified by anyone who has the verification key certificate, MACs, however, only by the parties knowing the secret authentication key.
- Alice's digital signature of a message can only be created by Alice, the MAC value of a message, however, by both parties, Alice and Bob (and all other persons knowing the secret authentication key). It is thus possible to use MACs for purpose of bindingness.
With Article 3 of the Information and Communication Services Act (Federal Law Gazette 1879, Part 1, 1997), a Digital Signature Act came into force for the Federal Republic of Germany. This Act regulates which security requirements have to be met by the technical components used for digital signatures and which tasks certificate authorities issuing the verification key certificates have. In addition, it is regulated how the required security of the components and certificate authorities is checked. Ultimately, digital signatures are also conceded a high level of security before court in accordance with the Signature Act.
Key management
Whenever using encryption, it is necessary to manage the keys appropriately. The question arises how
- generation/initialisation
- agreement/establishment
- distribution/transport
- change/update
- storage
- attestation/certification
- callback
- recovery in the event of destruction/loss
- destruction/deletion
- archiving and
- escrow
are carried out during the entire life cycle of the keys. The key management can and will usually also make use of cryptographic techniques. It must be carried out for all of the crypto modules of a security system based on cryptography. Secret keys must be protected against unauthorised disclosure, modification and replacement. Secret keys must be protected against unauthorised modification and replacement. An appropriate key management is the prerequisite to ensure that information can be protected by means of cryptographic procedures at all. Key management needs resources specifically dedicated to this task!
Certificate authorities
Trust centres and/or certificate authorities are required whenever you want to use asymmetric cryptographic procedures for the digital signature or for encryption for a number of participants that is no longer manageable. Such procedures require another key for generating signatures and/or encryption than the key required for checking signatures and/or decryption. For this purpose, a key pair of corresponding keys is generated in a user-related manner. A key, referred to as public key, is publicly disclosed. The other key, referred to as private key, must be kept secret under all circumstances. Using the private key, and only using this key, a digital signature can be generated and/or a text decrypted and verified and/or encrypted using the corresponding public key, and only using this key. If you want to ensure the authenticity of the public keys and the secure assignment of the keys to persons, trust centres / certificate authorities already mentioned above confirming the assignment of a person to a public key by means of a certificate are required.
Typically, the following tasks are carried out in such certificate authorities:
- Key generation: Key pairs must be generated for the certificate authority and, if necessary, for the participants.
- Key certification: The participant data, the corresponding public key and additional data are summarised in a certificate and digitally signed by the certificate authority.
- Personalisation: The certificate and, if necessary, the public and private keys are transferred to a signature component (among other things, a chip card).
- Identification and registration: The participants are identified and registered on presentation of a corresponding identification paper.
- Directory service: Certificates are kept in a public directory for retrieval. In addition to this, the directory service must also provide information on whether a certificate is blocked or not.
- Time stamp service: For certain data, it might be necessary to link it with a trusted time. For this purpose, the time is appended to the data and the result is digitally signed by the time stamp service.
In addition to this, trust centres can also offer the storage of keys as a service, when the cryptographic keys are to be used for encryption. In order to be still able to access the encrypted data when a key was lost, the owner of the key (and only the owner of the key) can receive a key duplicate that is stored securely in the trust centre.
Key distribution centres
The security of symmetric encryption procedures depends on whether the shared secret key is only known to the users authorised to access the protected information. With respect to the protection of stored data which is only to be accessed by its owners, this can be ensured relatively easily, as this owner must only protect the key in such a way that unauthorised persons cannot access it.
However, matters are quite different when messages to be transmitted by a sender to a recipient via an insecure transmission medium are to be protected using a symmetric encryption procedures. In this case, the secret key must be available to both the sender and the recipient, i.e. it must be possible to exchange the information between the two communication partners in a protected manner. In practice, this is often realised by the encrypted distribution of communication keys by key distribution centres (KDCs), in which case entire hierarchies of keys depending on each other from a security point of view are created. The procedures used in this context are sometimes very complex and depend on various components regarding their security, especially on the physical, organisational, personnel and technical security of the KDCs and the keys agreed upon with the KDCs for communication.
Compromising a secret key, i.e. its disclosure towards an unauthorised third party, results in the loss of the confidentiality of all data the encryption of which was carried out using this key and/or depends on this key. This is especially critical if one of the central keys of a key distribution hierarchy was compromised.
Use of cryptographic procedures
When used properly, cryptographic procedures are ideally suited to ward off the following threats:
- acquisition of information by unauthorised persons,
- deliberate manipulation of data by unauthorised persons and
- manipulations to the authorship of information.
Using only cryptographic procedures, however, is not sufficient to ward off all threats.
- The use of cryptographic procedures does not contribute anything to ensure the availability of data (the improper use of encryption might even result in the loss of data!).
- Cryptographic procedures cannot do anything against denial-of-service attacks (see also T 5.28 Denial of services). However, they can also contribute to detect such attacks at an early stage.
- They do not help to fight accidental falsifications of information either (for example, by means of "signal noise"). Based on these procedures, however, it is possible to subsequently recognise falsifications.

