S 3.64 Introduction to Active Directory
Initiation responsibility: IT Security Officer, Head of IT
Implementation responsibility: Administrator
The Active Directory is the central data store for all administrative data in a domain using the Windows Server 2000 or Windows 2003 Server operating systems as a basis. The server operating systems are collectively referred to in the following as "Windows Server". When viewed abstractly, the Active Directory forms a hierarchically organised and tree-like, object-based database. It is based on the X.500 directory service standard, and its internal structure and internal design are taken from this standard. However, it is not an X.500-compatible directory service.
At the domain level, the Windows Server domain concept is principally the same as the Windows NT domain concept: computers and users are consolidated in a domain and can be managed as a unit by the domain administrator. A domain boundary basically forms an administrative boundary and therefore also limits the effective scope of authorisations. In addition to this concept, Windows Server also allows you to relate domains with each other in a tree-like structure so that parent-child relationships can be created between domains. In this case, a child domain is also referred to as a subdomain, because the name of the child domain is derived from the name of the parent domain by appending the name of the parent domain to the name of the subdomain separated by a decimal point.
Example:
Name of the parent domain: company.com
Name of the subdomain: administration.company.com
The name space created this way is identical to the corresponding DNS name space and cannot be formed in a different way to the DNS name space. Domains having a common base name form a tree.
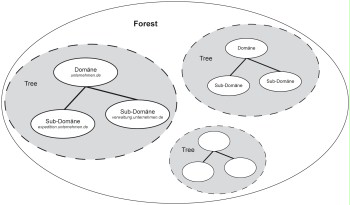
Figure: Active Directory structure
Domains containing several different trees, and which therefore span different name spaces, can still be administrated together.
Domain trees connected together in this manner form a forest. A single domain alone also forms a tree, and therefore simultaneously forms a forest as well.
Every forest also contains one domain that has a special role in the forest. It is the first domain created and is referred to as the forest root domain (FRD, the root domain of the forest). Its role is special, because administrators of the forest root domain have extensive authorisations throughout the entire forest. The domain boundaries are not administrative boundaries for members of the Enterprise Admins group, because they have access rights in all domains. When forming a Windows domain network, it must be noted that the first domain created is always the forest root domain. In particular, it is not possible to subsequently "transfer" the "role" of the forest root domain to another domain, and so it may be necessary to completely recreate the structure of the domain to obtain the desired form.
The Active Directory consists of various objects referred to as the Active Directory objects (ADOs). Every object contains one special type, e.g. a user object or computer object, and the object is assembled from various attributes according to its type. The various object attributes may adopt different values such as a telephone number or an IP address, for example. The Active Directory knows a variety of predefined object types:
- Domain object: This object is the root of all Active Directory objects in a domain and contains information about the domain such as its name, for example. Other objects can be placed below a domain object.
- Organisational unit objects: These objects are used to group other objects. The organisational unit (OU) object is available by default. An OU object may contain other OU objects as well as computer, user, and user group objects below it.
- Computer object: This object is used to represent Windows client computers. No other objects can be placed below a computer object. The Active Directory is only designed for the administration of Windows computers, which means computer objects can only represent Windows computers that interact with the Active Directory. By default, these computers must run the Windows NT operating system or a later version. Active Directory login components are available for other versions of Windows such as Windows 98, for example.
- User object: This object is used to represent domain users. No other objects can be placed below a user object.
- User group objects: These "security groups" are used to represent Windows groups. There are various types of groups that differ in terms of their scope (domain-wide, forest-wide) and in terms of the possible members of the group (domain or forest objects). The possible groups include the local, domain local, global, and universal groups. Security groups are used to assign authorisations. When compared to Windows NT, a Windows Server will have a significantly higher number of groups (several tens of thousands for larger companies) so that consideration may need to be given to using tool-based administration. The tool can be in the form of scripts written in-house, as well in the form of products from third party manufacturers. Whether or not it makes sense to use such tools, and if so, which tools should be used, must be decided on a case-by-case basis.
The general Active Directory structure can be illustrated as follows:
- The domain object is the root of the Active Directory tree of a domain.
- OU objects are created below the domain object in order to collect computer, user, and user group objects in a common structure. Since OU objects can be nested, the result is an organisation-specific tree structure.
In a standard installation, the Active Directory structure created by a Windows Server is flat and simple, and this structure then must be changed according to the Active Directory plan. Since the Active Directory is primarily used to administrate a Windows system, it should be taken into consideration when designing the structure of the Active Directory that the structure is intended to model administrative conditions. If the organisational structure of an organisation is instead modelled down to the smallest detail, this may result in problems with the administration.
The ways in which the Active Directory objects can be organised, meaning the specification of which object is allowed to contain which other objects, which attributes exist and which attributes can be used to form objects, is defined in the Active Directory scheme. The default Active Directory scheme provided by Microsoft may also be changed. However, changes to an Active Directory are major operations that must only be performed after careful planning. A scheme change will affect all domains administrated as a group, i.e. all domains in the forest. Since scheme changes are critical operations, they can only be performed on exactly one computer, which is referred to as the scheme master, by members of the group of Scheme Admins. Furthermore, under certain circumstances it may not be impossible to reverse scheme changes. It is therefore essential to assign membership to this group restrictively and to strictly monitor who is a member.
Members of the group of Enterprise Admins, which includes the administrator of the forest root domain by default, have special authorisations in all domains of the network.
Members of this group can add new domains to the forest and have administrator rights on all domain controllers of the Active Directory.
Within an individual domain, administration is performed by the members of the corresponding (domain-specific) group of Domain Admins. The members of this group have unlimited administrative privileges in a domain. However, it is also possible to allow other user accounts to perform individual administrative tasks, and so to delegate administrative tasks (see also S 2.230 Planning of Active Directory administration).
Delegation of the administrative tasks in a domain may also be achieved by delegating the administration of only a portion of the user accounts and computers in a domain. This is possible within the boundaries of the OUs used to group the user and computer accounts in the domain.
Numerous Windows client configuration parameters are consolidated in the group policies. In addition to the local group policies available on every single Windows client computer, there are also group policies that are stored in the Active Directory. These group policies permit the configuration of computers or user accounts at a central location. The group policies stored in the AD may apply to entire domains or OUs under some circumstances. In this case, OUs are used to place similarly configured computers or user accounts in a single group. Since OUs can be nested and several group policies may apply to any given OU, a variety of group policies may apply to an individual computer under some circumstances (see also S 2.231 Planning of group policy under Windows and S 2.326 Planning the Windows XP and Windows Vista group policies).
A relational, transaction-oriented database is used to store the data. This database is distributed between special servers, which are referred to as domain controllers. The domain controller uses the Active Directory in this case to provide central authentication and authorisation of users and computers in a domain. The following protocols are used for this purpose:
- Lightweight Directory Access Protocol (LDAP) to query objects and attributes in the Active Directory
- Kerberos for the authentication of users and computers
- Common Internet File System (CIFS) for transferring files in the computer network
- Domain Name System (DNS) for name resolution of the computer systems in the network
Each domain controller (with a few exceptions) contains only the data in its own domain in this case. The exceptions are listed below:
- Every domain controller contains the scheme data and configuration data of the entire forest.
- At least one domain controller in every domain also contains the "Global Catalog".
The Active Directory is stored on domain controllers and the domains are synchronised via replication. The Active Directory of a domain only contains information related to the domain. The Global Catalog (GC) is created to be able to access information in a forest quickly throughout the entire forest. It consists of some of the information on the Active Directory objects and is replicated throughout the entire forest so that it is possible to access the information in one domain directly from the other domains via the Global Catalog.
In addition to the tree-like and hierarchical structure described, Windows Server also automatically creates an additional and orthogonal structure. Computers that are near each other physically (which is determined by Windows Server using the network response time) are consolidated in objects referred to as sites. Sites are also used to control the replication structure of domain controllers, among other tasks. There must be at least one computer per site that stores a copy of the Global Catalog. The Global Catalog must be queried when a user attempts to log in, which means it must always be possible to access a Global Catalog server when a user logs in. The site structure automatically created by Windows Server should be adapted to reflect the conditions prevailing in the government agency or company, i.e. to represent sites in different cities or countries. Since this has an affect on the replication relationships in the Active Directory, it is necessary to create a concept for structuring the sites.
These roles are also referred to in Windows Server terminology as FSMO roles (FSMO = Flexible Single Master Operations). Certain changes can only be performed on the computer assigned this role in this case.
Two different replication mechanisms can be used to synchronise the data between the individual domain controllers. The mechanism used as well as the replication interval can be configured.
Through application of the distributed database concept, the Active Directory can achieve a certain level of reliability, but the computers assigned the role of an FSMO are a problem.
In Windows 2000 Server and higher, the data of the Active Directory is replicated among the domain controllers of an organisation using multi-master replication. In this case, every domain controller has a replica of the Active Directory that can be changed and used as the basis for future replications. The use of several domain controllers in an organisation creates redundant copies of the Active Directory, and therefore minimises the probability of a total failure.

