S 4.90 Use of cryptographic procedures on the various layers of the ISO/OSI reference model
Initiation responsibility: IT Security Officer
Implementation responsibility: IT Security Officer
The OSI reference model according to ISO
Cryptographic procedures can be implemented in various layers of the ISO/OSI reference model. This model briefly explained in safeguard S 5.13 Appropriate use of equipment for network coupling of this manual defines four transport-oriented layers and three application-oriented layers. Instances of a layer in different systems communicate with each other using logs. Each layer offers its services to the next higher layer. In addition to usual communication services, this can also be a security service. Which security service is to be placed in which layer of the layer model and which mechanisms can be used for this purpose is described in Part 2 of ISO 7498 (Security Architecture).
Even if concrete communication systems, reference models or logs do not always comply with the ISO reference model, being familiar with the ISO reference model helps to evaluate the security functions of products and thus also facilitates the systematic creation of "secure" overall systems.
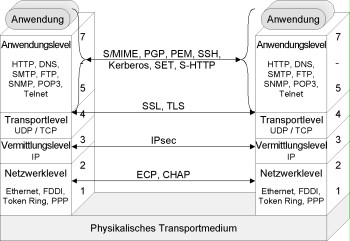
Figure: Evaluation of the security functions of products with the help of the ISO reference model
In the following, it is to be explained what advantages or disadvantages are related to the use of cryptographic procedures in the respective layers.
Cryptographic procedures are used to protect different information arising during communication, i.e. to encrypt information, to assign cryptographic checksums to it or to sign it. On the one hand, the data transmitted by the user can be protected, but on the other hand information resulting implicitly from the exchange of information (e.g. traffic flow information) can be also.
Security relationships can exist for different security services in different OSI layers at the same time. Above the layer in which a security service is realised, the information (regarding this service) is available in an insecure manner. Cryptographic mechanisms (encryption, digital signature and cryptographic checksums) contribute to the realisation of important security services (authenticity, confidentiality, integrity, communication and proof of the data source).
For this purpose, an overview of the aspects speaking in favour of or against the use of cryptographic procedures in different OSI layers is provided first:
| Use of cryptographic procedures in | |||
|---|---|---|---|
| upper layers: | lower layers: | ||
| +: | appropriate when the application data near the application is to be protected or when the "insecure channel" is to be kept as short as possible | +: | appropriate to connect two networks considered secure using an insecure connection, e.g. connection of two premises via public networks |
| +: | in any case whenever data is not protected in the lower layers | +: | to protect a network against unauthorised access |
| +: | appropriate for many, changing communication partners at different sites | +: | whenever traffic flow information is to be protected, e.g. address information |
| +: | users can use them in accordance with their own requirements | +: | all header and the user information at a higher level is encrypted |
| +: | protection closer and to the user and identifiable | +: | transparent for users, lower risk of improper use |
| -: | undermine protection by means of firewalls | +: | easier key management |
| -: | are often used improperly | -: | protection only up until the layer in which the security logs are realised |
| -: | often based on software, cryptographic keys and algorithms can be manipulated easily | -: | often hardware, and therefore expensive and inflexible |
| -: | higher dependency on the operating system or underlying hardware | -: | often does not offer any end-to-end security |
Table: Use of cryptographic procedures in OSI layers
In general, the key management is easy if group keys can be used, e.g. when setting up secure subnetworks (VPNs) whose accesses are equipped with crypto devices.
In most cases, the purchase price of cryptographic products for the lower layers is clearly above the purchase price of such products for upper layers; however, fewer products are required for lower layers. In addition, the amount of administration and implementation work is often lower, since security services do not have to be implemented in numerous applications. "Exotic" applications - without their own security functionality - can thus also exchange data in a secure manner.
In many cases, a combination of cryptographic services in different layers is also appropriate. This depends on the respective security requirements and the application conditions such as costs, performance and to what extent corresponding components are available. Decisive factors are also the assumed threats which the implemented security services are supposed to counteract as well as the underlying system architecture.
Security end devices <-> security connection elements
Security systems can be designed as an end device or part of an end device or as a connection element or part of a connection element. Connection elements are, for example, active network components such as routers or gateways.
In contrast to end devices, security connection elements usually have two network interfaces that are connected via a crypto module (hard- or software) in the layer typical for this system. One interface is connected to the "secure" network (e.g. internal network), whereas the other interface is connected to a network considered "insecure" (e.g. public networks).
Security end devices offer the advantage that the security mechanisms can be adapted well to the requirements of the application. Typical security end devices are crypto telephones, crypto fax machines or hard-/software-based security solutions for PCs. In general, security end devices offer solutions for individual workplaces. Sometimes, these solutions support only a single service. However, the limits are blurred (telephony via an Internet PC, crypto telephone with data input). In contrast to the connection element, the selection of the security layer is not limited in end devices, as they are generally complete, i.e. have 7 layers.
Security connection elements are often designed with such a performance capability that they can protect larger work units up to entire premises. In this respect, the manufacturers of such systems try to support as many services or superior logs as possible to allow universal application. The high degree of independence from the operating systems of the end devices also contributes to the universal applicability of connection elements. Of course, individual end devices can also be protected using security connection elements. However, the higher performance capability of the devices often results in higher costs. According to the definition, connection elements are incomplete OSI systems. Therefore, the implementation of security services is also restricted to the layers which the connection element has.
Combinations of these possibilities are also used. This requires that security end devices and security connection elements are harmonised with each other, especially with respect to the security mechanisms and security parameters used (e.g. cryptographic keys).
User, control and management information
A user is mainly interested in the transmission of user information to remote users. Depending on the concrete reference model (e.g. ISDN), however, control, signal and management information regarding the connection establishment/termination, negotiation of service quality parameters, configuration and monitoring of the network by network operators etc. are also transmitted between the systems (end devices, connection elements).
Here, the respective network has the task of transmitting user information in an unchanged and unevaluated manner, i.e. it is only necessary that user information can be interpreted by the end devices. Thus, this information can be protected independently from the remaining network infrastructure, if necessary even using proprietary security functions (closed user group). It is necessary that control, signal and management information of the transport layers can be evaluated, changed or created by the network elements of the network operator. Thus, this information largely escapes protection (e.g. encryption) that does not depend on the network operator. In addition to the corresponding standards, the protection of this information requires the trustful collaboration with the network operator. Threats might be the result of security functions of products being assessed improperly. When selecting crypto devices, it must be carefully checked which pieces of information are protected or filtered. By implication, it must also be checked which information remains unprotected despite the use of crypto devices and to which extent this has to be tolerated.
Example: For ISDN, the user information is generally transmitted via the B-channels. However, the D-channel primarily used for signalisation can also be used for the transmission of packetised data. If the aim is to protect all user data, it is obvious that the protection of the B-channels is not sufficient if packetised data is transmitted via the D-channel.
Security in circuit-switched networks
For circuit-switched networks, channels with a defined bandwidth are set up which, due to the connection establishment, are only available to the communication partners. After the connection has been established, the user data is transmitted and the connection terminated afterwards. The network operator can establish dedicated connections, for which the connection establishment and termination usually carried out by the participant is not required. ISDN is an example of a circuit-switched network.
Due to the establishment of the connection, user data channels are set up in OSI layer 1 between the communication partners, which are referred to as B-channels in terms of ISDN. To ensure the confidentiality of the transmitted user data, this channel can be encrypted. If the signalisation channel is to be protected in addition to this, for N-ISDN, i.e. the D-channel (layer 1-3), it is necessary to take into account that both the end device of the communication partner and the switch points of the network operator can occur as receivers of an end device. The D-channel is usually not encrypted, as special requirements would have to be placed on the network operator. In this case, the monitoring and filtering of the D-channel should be provided (see also S 4.62 Use of a D-channel filter).
The encryption of synchronous full-duplex dedicated connections must be considered to be a special case, as it is possible in this case to ensure the confidentiality, including the confidentiality of the traffic flow. If there is no data to be transmitted, filling data is encrypted to ensure that there is a continuous "signal noise" on the circuit at any time. The circuit encryptor constitutes an alternative to the installation of protected circuits.
Security in packet-switched networks
For packet-switched networks, a distinction must be made between connection-oriented and connectionless packet switching. For the connection-oriented packet switching, a virtual connection is set up during the connection establishment phase, subsequently defining the data path through the packet network. After the connection has been established, data packets are routed on the same path through the network based on the assigned virtual channel number. Sender and/or recipient addresses are no longer required for this purpose. An example of this is the X.25 network.
For connectionless packet switching, there are no connection establishing and terminating phases. Data packets, among other things equipped with source and target address, are switched individually. This is characteristic of LAN data traffic.
The selection of the layer in which the security mechanisms are effective defines which pieces of information are protected. The lower the selected security level, the more comprehensive is the protection of information. When the user data pass the instances of the layers 7 to 1 (senders), additional control information is added to the data. If it is not only about the protection of user data, but also about the protection of the traffic flow, it is recommended to select a lower OSI layer. On the other hand, the following applies: The lower the selected OSI layer, the fewer connection elements (repeaters, bridges, switches, routers and gateways) can be overcome transparently.
| Connection element | Highest layer of the connection element |
|---|---|
| Repeaters | 1 |
| Bridges, layer-2 switches | 2 |
| Routers, layer-3 switches, X.25-packet handlers | 3 |
| Gateways | 7 |
Table: Comparison: Connection element - ISO layer
If the security services are to be effective across the connection elements, they must be implemented in a layer above the highest (sub)layer of the connection elements. Thus, it is ensured that the transmission equipment can forward the protected information in an unprocessed/uninterpreted manner.
Examples and consequences of improper network configurations:
Example 1: All end devices of two LANs connected using a router and public communication networks are to be equipped with layer-2 encryption components to ensure the confidentiality, especially regarding public communication networks. The router must evaluate the addresses of layer 3 to forward the LAN data packets using the public network. Since, however, all layer-3 data is hidden due to the layer-2 encryption, the layer-3 addresses cannot be evaluated successfully. Thus, the data is prevented from being transmitted. As a remedy, the encryption components for layer 3 (upper sublayer) or higher must be used in this case.
Example 2: A major part of an organisation's correspondence is to be processed electronically using X.400 (layer 7) in the future. To protect the data integrity, the organisation plans to use layer-4 crypto components in the end devices (PCs in this case). For protection purposes, the data packets are equipped at the sender in layer 4 with cryptographic checksums which are checked by the associated layer-4 crypto component of the recipient. Only data packets with correct checksums are to be sent. If, however, not all MTAs (Message Transfer Agents, i.e. the switching agents for electronic messages in layer 7) are also equipped with interoperable crypto components, the MTAs without crypto component cannot generate any valid checksums so that the MTAs or end devices with a crypto component have to discard the data according to the specification.
But even if all MTAs used as well as the end devices are equipped with interoperable crypto components and security parameters, data integrity is not ensured. Then, the section-by-section protection of the data can be ensured, but a falsification of the data within the MTAs is possible without being noticed. Moreover, (depending on the log) individual layer-4 data packets could get lost, which results in gaps in the complete message whose integrity should actually be protected. In this case, the protection of the integrity of the data in layer 7 can be used as a remedy.
As the examples show, it must be examined in detail which network topology is applicable and which network areas have to be protected in which manner so that an adapted solution with the desired (security)characteristics can be found.
Section-by-section security <-> end-to-end security
Users of communication systems often expect that security services are rendered continuously (end-to-end security), i.e. from the input of information (data, language, images, text) on the end device A up to the output of information on a remote end device B. If no continuous security service is guaranteed, there are, besides the end devices involved, further systems on which information is available in an unprotected manner. If there is, for example, end-to-end encryption to protect the confidentiality of a communication relationship between two participants, the data is thus available in unencrypted form in at least one further network element. Such network elements must be localised and protected by means of additional safeguards. Personnel who have access to such unprotected network elements in particular (e.g. administrator) must be accordingly trustworthy. In this case, security services are not rendered continuously, i.e. end-to-end, but section by section. Attention must be paid to ensure adequate protection of all relevant sections.
Multiple protection in different OSI layers
No objections can be raised to multiple protection of the information to be transmitted in different OSI layers if certain rules are followed, which, however, are implicitly ensured in the event of products conforming to the standard. For encryption in particular, the bracket rules known from school must be applied. Thus, encrypting is equivalent to opening a bracket, whilst decrypting corresponds to closing a bracket. Within the bracket, still other security mechanisms can now be applied.
Multiple protection can have an adverse effect in that the data throughput is minimised due to additional operations or in that the amount of user data that can be transmitted is reduced by the fact that additional data have to be transmitted to increase the redundancy (e.g. cryptographic checksums). Data protected prior to the transmission using crypto systems, e.g. digitally signed documents, also results implicitly in multiple protection. Thus, the security of the data transmission is increased regarding the security services used.
Often, the security of the overall system can only be achieved by an combination of several security logs or security products. If, for example, application-related security solutions are available, the trusted implementation of which, however, was not examined (by an independent body) (e.g. evaluation according to ITSEC, CC) and if trusted transport-oriented security products are available at the same time to protect insecure network sections between remote premises, an overall security solution meeting the requirements can be created under certain circumstances due to the combination of the safeguards. In this respect, the higher amount of administrative work and/or higher procurement costs have an adverse effect.

