S 4.198 Installation of an application in a chroot cage
Initiation responsibility: Head of IT, IT Security Officer
Implementation responsibility: Administrator
In order to increase the security, an application can be installed in a so-called chroot cage. The chroot() system command restricts the access of a certain application to a part of the file tree in Unix. This is ensured by implementing all accesses to the file system performed by this application and the applications called by this application relative to the directory specified when calling the chroot() function. This way, the directory becomes the root of the virtual file tree, referred to as chroot cage or chroot jail. It is not possible to access superior directories and files. For example, several services can be separated from each other on one server this way.
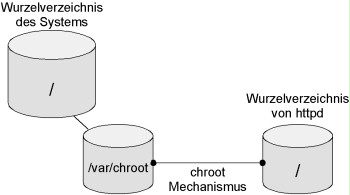
Figure: Root directory
In addition to the chroot() system command, there is also an eponymous executable program that can be used for starting any applications desired in such a chroot cage. For example, if an attacker manages to execute his/her own program code in the process space of the application, the direct damage would be contained by the fact that the attacker does not obtain direct access to the actual operating system. There are ways for breaking out of a chroot cage. However, an attacker must first notice that he/she is in a chroot cage. This delays the attack. During this time, the attack may possibly be detected and countermeasures can be initiated.
The chroot cage must contain copies of all files required for executing the application. Which files this refers to must be determined on the basis of the existing documentation. Normally, this includes the following files and directories: dev, lib, usr/bin, var, var/run, etc, and the application-specific files and directories.
If installing an application in a chroot cage is being considered, sufficient time must be allocated for planning and testing. During installation, it must be documented
- which is the root directory of the chroot cage and
- which operating system components are made available in the chroot cage.
In particular, some device files must be created in the chroot cage; furthermore, correspondingly adapted versions of the files /etc/passwd and /etc/group are required. All entries not required, except for the user and the group the application is to be operated by, should be removed from these files. Depending on the operating system, additional entries may be necessary that should be kept in the files.
Review questions:
- Has the configuration of the chroot cage been documented sufficiently?
- Has all necessary data been copied into the chroot cage?

