S 4.223 Integration of proxy servers into the security gateway
Initiation responsibility: IT Security Officer, Head of IT
Implementation responsibility: Administrator
HTTPS security proxy
The HTTPS proxy should decrypt the incoming data traffic, forward it to the content filter, and then re-encrypt the data traffic. The temporarily unencrypted data traffic can be examined for undesired content.
Ideally, the application level gateway (ALG) used supports an HTTPS proxy. The relatively simple design shown in the figure below can be used in this case. For the sake of clarity, the case where the data traffic is filtered by a separate component is considered. In many cases, though, filtering has already been integrated into the ALG by the manufacturer.
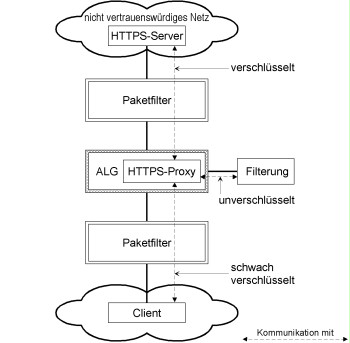
Figure: Integration of an internal HTTPS proxy
| Advantages of an "HTTPS proxy on the ALG" | Disadvantages of an "HTTPS proxy on the ALG" |
|---|---|
|
|
Table: Advantages and disadvantages of an HTTPS proxy on the ALG
If the ALG does not offer an HTTPS proxy, the structure shown in the figure below can be used. In this case, the HTTPS proxy is located in a separate DMZ. In contrast to the previous figure, the figure below illustrates the case where malicious content is filtered by the ALG.
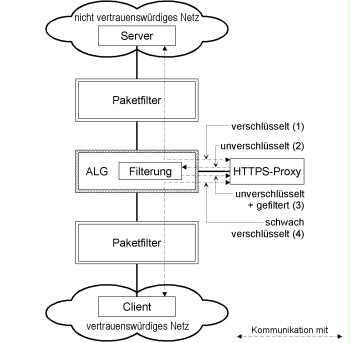
Figure: Integration of an external HTTPS proxy
| Advantages of an "HTTPS proxy in a DMZ" | Disadvantages of an "HTTPS proxy in a DMZ" |
|---|---|
|
|
Table: Advantages and disadvantages of an HTTPS proxy in a DMZ
The strength of the encryption in the trustworthy network could be adapted to the protection requirements and the trustworthiness of the participants in both of the solutions presented. It may also be possible to do without encryption in the trustworthy network or to use a less processor-intensive and weaker encryption procedure in order to increase the performance.
Caching proxy
When services are used, access to the untrustworthy network could be restricted to certain proxies (e.g. to a caching proxy for HTTP). The clients are not able to bypass the ("forced") proxy in order to communicate with external partners, since the IP address of the client is rejected by the security gateway (only the IP address of the caching proxy is accepted by the security gateway).
| Advantages of ("forced") caching proxies | Disadvantages of ("forced") caching proxies |
|---|---|
|
|
Table: Advantages and disadvantages of forced caching proxies
Reverse proxy
"Reverse proxies" are used in the context of providing (web) servers, but can also be used to achieve the following security objectives:
- Restriction of the communication links coming in from the untrustworthy network that need to be routed through a security proxy. This simplifies administration of the security gateway and reduces the likelihood of incorrect configurations.
- Hiding the identity of the web server (several web servers used for the purpose of load distribution will appear in the untrustworthy network under a single IP address).
- Recognising error messages from the web server that could provide an attacker with information he/she could use to compromise the system (this is actually a workaround, because the web server should solve this problem itself).
- Improving the protection of the web server, meaning that an attacker may be able to read the information of a transaction under some circumstances, but will not be able to gain access to the web server.
- Separating the IP stack of the server from the untrustworthy network.
- Filtering out undesired requests directed at the web server that originated in the untrustworthy network.
- Increasing availability through load distribution and reducing the load through the use of a cache.
The following figure illustrates a situation in which two servers are provided for access from the untrustworthy network. In the scenario shown, it is necessary to open two communication links that pass through the ALG and the external packet filter.
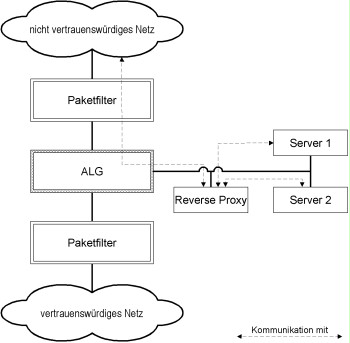
Figure: Reverse proxy used to reduce the number of communication links passing through the ALG. The reverse proxy and the servers are located in the same DMZ.
The number of communication relationships shown in the previous figure can be reduced with the help of a reverse proxy. In the figure, clients in the untrustworthy network are only allowed to access the reverse proxy while access to server 1 and server 2 is blocked. Only the reverse proxy can access these two servers.
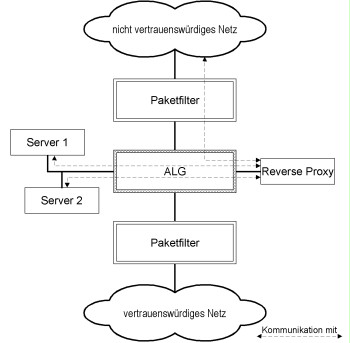
Figure: Reverse proxy used to reduce the number of communication links passing through the ALG. The reverse proxy and the servers are located in different DMZs.
To increase the security of the servers, the servers can also be operated in a separate DMZ where they are separated from the reverse proxy by a security proxy. It is more difficult to take control of a server in this case, but the number of communication relationships passing through the ALG increases.
Review questions:
- Refers to the use of a reverse proxy: Are there safeguards to be taken in the event of reserve proxy failure?
- Does the use of the proxies correspond to the security policies of the organisation?
- Refers to the use of a caching proxy: Is the caching proxy used in accordance with the specifications of the organisation's security policies?
- Refers to the use of a caching proxy: Are there safeguards to be taken in the event of caching proxy failure?
- Are there safeguards to be taken in the event of proxy failure?
- Refers to the use of a reverse proxy: Is the reverse proxy implemented in accordance with the requirements of the organisation's security policies?

