S 4.224 Integration of VPN components into a security gateway
Initiation responsibility: IT Security Officer, Head of IT
Implementation responsibility: Administrator
It is essential for the security of a VPN to integrate the VPN endpoints into the security gateways. The ideal placement of the VPN components depends on several factors in this case:
- the protection requirements of the VPN gateway against attacks from untrustworthy networks,
- the need to control and regulate the flow of the data transmission for accesses from the untrustworthy network to systems and services in the trustworthy network, and
- the protection requirements of the data transmitted
The most well known protocols for designing VPNs include IPSec, TLS/SSL, PPTP, and L2TP. Therefore, these types of VPNs are examined in the following. However, the recommendations shown here may also be applied to most other procedures. The decision to select a certain procedure depends on the particular application and the area in which it will be used. It may absolutely be expedient for an organisation to operate several VPNs using different VPN protocols and cryptographic procedures.
The decision regarding which procedure to use and how the individual VPN components should be arranged must be documented.
VPNs using IPSec or TLS/SSL
Where the VPN gateway is integrated relative to the packet filter of the security gateway depends on how many interfaces are available on the VPN gateway.
- VPN gateways with one interface:
If the potential for attack is high, the VPN gateway should be protected by a packet filter and should be located in the application level gateway (ALG). The outer packet filter provides protection against IP spoofing attacks since packets from the untrustworthy network with the IP-address of the VPN gateway as their sender address are not forwarded by the outer packet filter. The decrypted data traffic must pass through the ALG and the inner packet filter on its way into the trustworthy network. Since decrypted connections are only allowed on the DMZ interface of the ALG and not on the interface of the ALG to the untrustworthy network, it is significantly more difficult to establish unauthorised connections from the untrustworthy network when compared to the variants used before.
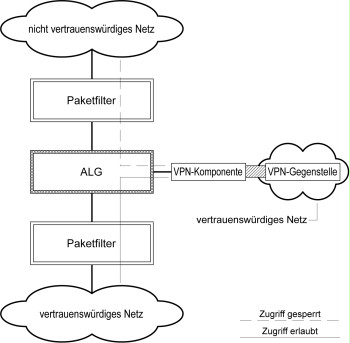
Figure 1: Placement of a VPN component with one interface
- VPN gateways with two interfaces:
Regarding VPN gateways with two interfaces, one network interface of the VPN gateway should be connected to the outer packet filter and the other interface to the ALG. When placing the VPN gateway on the outer packet filter the VPN component is protected against attacks from the untrustworthy network by the packet filter. Only connections to the VPN gateway needed for VPN communications are allowed to be established from the untrustworthy network. The decrypted data traffic can be controlled and restricted at the application level, because the connections pass through the ALG. In addition, the decrypted data traffic may be checked and restricted by the internal packet filter.
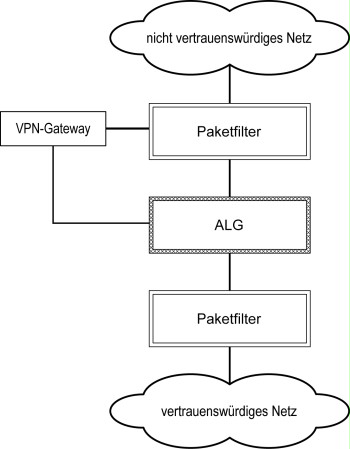
Figure 2: Placement of a VPN component with two interfaces
VPNs using Layer 2 protocols
Layer 2 VPNs can be implemented with the help of the PPTP (Point to Point Tunnelling Protocol) and L2TP (Layer 2 Tunnelling Protocol) protocols, for example. They are often used to build VPNs over public telecommunication networks, for example the GSM or ISDN networks. An ALG should also be used in Layer 2 VPNs between the LAN and the VPN connection for the purpose of network separation.
When connecting several different user groups with different rights, every user group should be assigned to a separate key class to ensure the data transmitted between the user groups remains confidential.
Review questions:
- Are the VPN components integrated into the security gateway in such a way that the data traffic can be controlled and filtered effectively?
- Has the decision regarding how the VPN components should be integrated into the security gateway been documented?

