S 4.226 Integration of virus scanners into a security gateway
Initiation responsibility: Head of IT, IT Security Officer
Implementation responsibility: Administrator
Malware such as viruses, worms, and Trojan horses (hereinafter collectively referred to as "viruses" for the sake of simplicity) can be filtered centrally on the security gateway on the one hand, but also locally on the workstation PCs and servers (i.e. on the endpoints of communication links passing through the security gateway).
Centralised filtering on the security gateway cannot completely substitute the use of local virus protection programs, since malware may also infiltrate the systems via other routes (for example via removable data media).
Centralised filtering is currently only possible when using an application level gateway.
Filtering directly on the ALG
If the ALG used offers a filtering option, it usually makes sense to check for malware directly on the ALG.
Filtering by the security gateway when using an ALG
ALGs frequently provide an interface for connecting anti-virus software from third-party providers. The anti-virus software receives the data and provides the ALG with a message containing the results of virus scanning. The ALG then processes the data based on the results of the virus scan.
For this reason, it is recommended to use the design shown in the following figure for the integration of the virus scanner, in which the virus scanner is placed "next to" the ALG in the DMZ of the security gateway. It is necessary to take into account several points in this design, since the computer running the anti-virus software is particularly at risk:
- The configuration of the computer with the anti-virus software must be particularly secure, for example by specifying a particularly restrictive operating system configuration (hardening). The security requirements are (at least) as high as for the other components of the security gateway.
- The computer must be isolated as much as possible from the rest of the network using corresponding packet filter rules. In particular, the packet filters should not allow any outgoing connections from this computer to the internal network or to the external network. Ideally, the computer is able to communicate directly with the ALG it receives the data stream to be scanned from and it returns the filtered data to. The only connections other than this connection that are allowed are those coming from a separate administration network.
- The regular integrity checks of the system should be performed at frequent intervals.
- The computer should possibly be equipped with a host-based intrusion detection system so that possible compromising of the computer can be detected as quickly as possible.
- The administration of the computer must be performed using an appropriately secure connection.
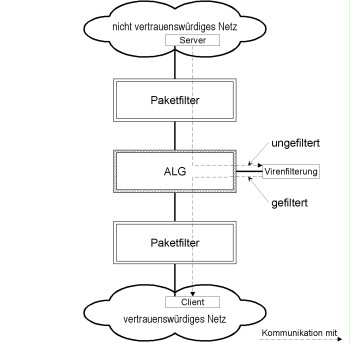
Figure: Integration of a virus filter
Filtering on the terminal devices (when using a packet filter)
Since packet filters do not have interfaces for virus filters, it is normally impossible for the security gateway to filter viruses centrally when using a single-tier security gateway consisting of only one packet filter. In this case, protection against malware may only be achieved using virus filters on the workstation computers or on the corresponding servers in the trustworthy network (for example on the email servers and news servers).
Module S 1.6 Protection against malware also must be taken into account in terms of virus protection.
Review questions:
- Is centralised filtering performed on the security gateway in addition to decentralised virus protection?
- Refers to the integration of anti-virus software on the application level gateway: Is the external computer for virus scanning secured when compared to the components of the security gateway?

