S 4.281 Secure installation and preparation of Windows Server 2003
Initiation responsibility: Head of IT, IT Security Officer
Implementation responsibility: Administrator
Preparation consists of all steps taken after planning and purchasing the server or group of servers until initiation of operation in production. The installation of the operating system is especially critical. During this phase, the protection mechanisms in Windows Server 2003 are not available. Many specifications in security policies can only be implemented on an installed server. On the other hand, important parameters for the subsequent operation phase are already specified during installation. For this reason, an installation concept according to S 2.318 Secure installation of an IT system must be created that accounts for the specific behaviour of Windows Server 2003. When installing on a group of servers or installing repeatedly, automation and standardisation of the installations becomes more important. In addition, the existing IT environment and any software management systems present will have an influence on the installation and preparation phases. Such considerations are often beyond the scope of the installation concept for an individual server. For this reason, it is recommended to create a more comprehensive, reusable preparation concept that takes the existing installation concepts into account. The concepts for installation and preparation should be created so that the administrator has specific instructions for exactly the installation task he needs to perform.
In addition to manual installation from unaltered Windows Server 2003 data media, there are also two other basic preparation variants: installation using a hard disk image and installation from an installation source using the setup program. Automation and standardisation is possible in both variants, but the way they achieve it is different.
The figure provides an example of the two preparation variants in the form of two possible installation paths:
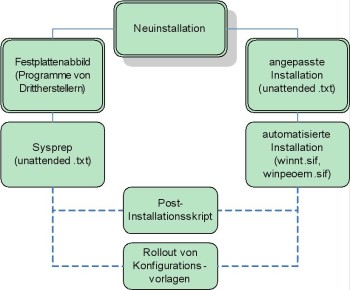
Figure: Preparation paths
From the figure, it is possible to derive the basic resources required for preparation and the order in which these resources need to be prepared. The scenario can be modified and expanded by using additional software. The administrator should be trained in the application of the resources shown here at a minimum since almost all procedures are based on them.
Aspects to take into account in the installation concept
A number of factors must be taken into account in the installation concept for an individual server:
- boot procedure and initiation of the installation
- drivers for mass storage devices and possibly network drivers need to be available for the boot procedure
- type of installation source (data media, network)
- integration of Service Packs into the installation source (referred to as slipstreaming)
- provision of the product key
- provision of hardware drivers
- installation of product updates (patches)
- membership in a domain, if necessary
- configuring server roles
- setting security-related parameters according to the security policies
- product activation of Windows Server 2003
For a preparation concept, these aspects and others are examined across all systems. You can find help on this subject in the Resources for IT-Grundschutz (see Preparation concept of Windows Server 2003 in the Resources for Windows Server 2003).
The common products for software management and distribution integrate and automate some basic Windows Server 2003 mechanisms, for example response files or drivers. For this reason, some generally applicable security aspects are explained in the following.
Security aspects
A hard disk image of a completely installed, operable server is taken and mirrored on another server. One drawback of this method is that the mirrored systems all have the same security ID (SID). Unique SIDs are absolutely necessary for the authentication procedures in a Windows environment. The procedure for changing the SID later on (using Sysprep or programs from third party providers) goes deep into the system and affects all objects critical to security. In addition, hard disk images are inflexible when changes are made to the hardware or software configuration. Mirrored systems must be activated, and for this reason, multiple license or volume license programs are recommended. Reliable operation of the mirrored systems should be verified in suitable test procedures.
Images permit a high degree of standardisation as well as protection against problems during installation. They are also easy to administer and archive. Software management programs are able to change certain system parameters when installing hard disk images. Further adjustments are made via Sysprep (with response file) and post-installation scripts. This concept clearly has advantages when there are a large number of images that do not need to be customised much.
Automatically customised installations are based on a response file for the installation procedure. They offer high flexibility and modularity when configuring hardware and software and can be changed with little effort. The installation itself is more prone to errors and attempts to compromise the system, but a separate log file is generated for every installation. It is recommended to use licensing programs with uniform product keys for fully automatic installation.
The installation logs should be saved at the end of the installation. These logs include the setuplog.txt file and all files with the .log extension in the root system directory (usually C:\WINDOWS) as well as all .log files in C:\WINDOWS\Security\Logs. The setuperr.log file must always be evaluated after installation.
Response files (unattended.txt, winnt.sif, winpeoem.sif, ini-files etc.) contain critical configuration information that can be misused by unauthorised persons to attempt to break into a system. For this reason, installation media or installation sources with customised response files should always be safe kept to protect against unauthorised access or should be assigned restricted permissions. The Setup Manager (SetupMgr.exe file on the installation CD or in \SUPPORT\TOOLS\DEPLOY.CAB on CD1 for Windows Server 2003 R2) is used to create the response files. Access to these files should be limited to administrators, and they should be subject to version control.
The planning of the installation accounts to be used during the preparation phase is particularly important. These accounts are just as critical as administrative accounts and should be monitored accordingly. They should be granted minimal authorisations, and the login capabilities should be limited.
Loading product patches during the installation process increases security. In spite of this, updates and patches should not be loaded directly from the Internet (Windows Update). Use of the Dynamic Update feature, which accesses a local source and allows the user to select the updates to be released individually, is to be preferred. To use this feature, the DUShare option must be entered manually in the response file. DUShare points to a folder on the installation source containing the update packages available in the form of .cab files.
Alternatively, product patches can be installed from a local update server after installing Windows using the Windows Update feature and post-installation scripts. One of the two methods described should be defined in the preparation concept.
Note: Manufacturer documentation on the subject of response files can be found in the ref.chm and deploy.chm files on the installation CD or in \SUPPORT\TOOLS\DEPLOY.CAB on CD1 for Windows Server 2003 R2.
In Windows Server 2003 with Service Pack 1 and higher, the local firewall is enabled with restrictive settings during and after the installation until the update process is executed again. Full connectivity is only available after the update process executes a second time. This mode protects the server when the product is activated and updated directly over the Internet. For low protection requirements, this scenario is adequate, but is not a replacement for an isolated installation network.
Conformity with security policies
Conformity with the current security policies when introduced into productive operation must be guaranteed by the preparation procedure. Security templates are usually transferred to the server and activated there using group policies and Active Directory. The templates can be installed with the aid of post-installation scripts as an alternative or in addition to using group policies and Active Directory. The finished installation must be tested with the current templates and the other current security policies. The implementation of the templates and settings should be part of the installation concept and the preparation concept.
Documentation
The preparation concept is to be documented understandably and in detail. A current installation instruction manual should be available for each server.
Review questions:
- In case of a high number of Windows Server 2003 systems: Is there a more comprehensible and reusable preparation concept in addition to the installation concept?
- Are the installation logs of Windows Server 2003 stored, and are the error notifications generated evaluated?
- Regarding script-controlled installation of Windows Server 2003 systems: Does the preparation concept take into account the installation by image or by response file?
- Is the installation of new systems made via separate accounts, and are these accounts provided with the required minimum authorisations?
- Does the preparation concept define installation of patches and updates in the new Windows Server 2003 system?
- Regarding script-controlled installation of Windows Server 2003 systems: Is it ensured that the response files do not include plain text passwords from the productive environment?

