S 4.365 Use of a terminal server as graphical firewall
Initiation responsibility: Head of IT, IT Security Officer
Implementation responsibility: Administrator
Generally, access options to an insecure network and the protection of the basic values constitute a conflict of objectives in a secure IT infrastructure.
On the one hand, Internet services with active content must be used, for example. On the other hand, access is performed using applications that must access the insecure network in each case. In classic client/server networks, these applications are executed in a protected manner downstream of port, packet, or application filters on the client and in the context of the user. Compromising the client software endangers the security of the client and of the internal network. At this point, terminal servers provide an additional level of security by encapsulating the applications on a separate IT system using the terminal server to access the insecure network. A terminal server accessing the insecure network in place of the client is referred to as a graphical firewall.
Viruses, worms, and other malware may not be executed on the client of the user at any time if a graphical firewall is planned and designed consistently, since only image information, as well as input and output data are transmitted between the terminal server and the terminal.
When designing a graphical firewall, essentially two possible additional objectives to be aimed at play a role.
- The protection of the internal IT systems against the insecure external network.
- The prevention of confidential data leaking into the external network due to technical defects, malware, or sabotage. However, the strict prevention of any exchange of information between the internal and the external network required for the aforementioned, e.g. by means of file transfer or the clipboard, significantly limits the practical use.
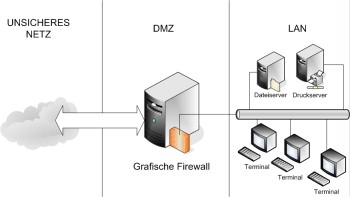
Figure: Graphical firewall in a separated zone.
In both cases, it is important for the efficiency of the safeguard that the communication to the insecure network is only performed using the graphical firewall. Moreover, the terminal server, as illustrated in the figure above, should be located in a zone separated from areas requiring protection (DMZ, demilitarised zone of the security gateway) in order to not endanger the internal network when the terminal server is compromised.
Here, it makes sense to only permit the transport protocol and the ports of the terminal server service along the route between the two network segments in order to minimise the number of attack vectors to the secure network. The following table lists the default settings of some terminal server services.
| Service | Protocol | Server port | Server zone |
|---|---|---|---|
| Windows Terminal Server | RDP | 3389 | DMZ |
| Citrix Presentation Server | ICA | 1494 | DMZ |
| X-Window | X11 | 6000 | LAN |
| X-Window with SSH | X11+SSH | 22 | DMZ |
| VNC | VNC | 5900 | DMZ |
Table: Protocols and part numbers of different terminal server solutions
It may be necessary to open further ports in order to grant access to the file server or the printer services in the LAN, for example. In order to avoid this, the data traffic for diverse services can be transmitted directly in the flow of data of the terminal server protocols for some solutions. Protocols which offer this option by means of virtual channels include the RDP protocol of the Windows Terminal Server or ICA in Citrix Metaframe, Presentation Server, or XenApp. Furthermore, tunnel connections may be used with SSH for the X-Window system, for example, which is capable of doing this ex factory.
Moreover, the technical particularities of the X11 protocol must be taken into consideration when using X-Window. Whereas in the otherwise common procedure the terminal obtains the output from the terminal server, the applications and therefore the graphical firewall in this case actively send their screen outputs to the X-server executed on the client of the user. As a consequence, port 6000 must be routed from the DMZ into the LAN in the router. For every additional client in the LAN communicating using the terminal server, an additional port above port number 6000 must be opened. In this scenario, this results in a large number of accesses to the internal network and should be avoided. Instead, it is recommendable to establish the connection using an SSH tunnel or a VPN.
Due to the particular threat to the graphical firewall, the use of an anti-virus scanner according to S 4.3 Use of virus protection programs is obligatory. Safeguards S 5.163 Restrictive granting of access rights on terminal servers and S 4.368 Regular audits of the terminal server environment ensure that the least privilege principle is applied.
Review questions:
- Is communication to the insecure network exclusively performed using the graphical firewall?
- Has the terminal server used as graphical firewall been located in a zone separated from the areas requiring protection (DMZ)?

