S 5.14 Shielding of internal remote accesses of PBX systems
Initiation responsibility: IT Security Officer, PBX System Manager
Implementation responsibility: Administrator
PBX systems often provide for remote maintenance access ports for management functions. These access ports can be used for performing all administration and maintenance work, as well as other management tasks such as alarm signalling and processing. Such remote access ports are particularly useful in complex PBX systems and are sometimes indispensable.
Often, the remote access can be used via the following technologies:
- access via an IP network
- direct dial-in via DISA (Direct Inward System Access)
- access via dedicated management ports using a modem
The use of remote access ports should be restricted as far as possible. Furthermore, it should be possible to log all accesses and all activities during an administration session.
Fundamentally,
- remote access in the organisation's own PBX system cluster (internal access) and
- remote access from external networks (external access, see S 5.15 Shielding of external remote accesses of PBX systems)
must be differentiated between.
For internal remote access, the protection of remote maintenance is considered within a PBX system cluster. Here, the term system cluster means an overall system consisting of several separate system parts connected to each other with the help of a separate network. If this connection is routed using public switching facilities, the safeguards described in S 5.15 Shielding of external remote accesses of PBX systems must be implemented additionally. When networking using closed user groups within public networks or using virtual private networks (VPNs), the safeguards for internal remote accesses and, if possible, the items highlighted with an "*" from the safeguards for external remote accesses should be implemented.
The most important aspect for shielding the internal remote access is to be able to prevent and possibly also detect attempted intrusions from external networks in an efficient manner. Furthermore, it should be possible to restrict the accesses from the organisation's own network to the authorised stations and persons. Depending on the type of access technology, there are different methods for this.
Shielding an internal remote access port using IP networks
If the PBX system is connected to an IP network, for example for the system to be configured and monitored, similar recommendations as for classic IT systems, including servers and clients, are applicable. Analogous to these IT systems, remote maintenance must be protected (see S 1.1 Compliance with relevant standards and regulations).
The PBX system must be configured in such a way that only authorised administrators may log in to the PBX system upon appropriate authentication. For this, a corresponding authentication method must be selected (see S 4.133 Appropriate choice of authentication mechanisms). If possible, the PBX system should be configured in such a way that only authorised IT systems are allowed to access the PBX system, for example by means of a separate configuration network or packet filters (see S 4.98 Restricting communication to a minimum with packet filters and S 4.238 Use of local packet filters).
In order to prevent the information transmitted between the IT systems of the administrators and the PBX system from being intercepted, the information transmitted should be encrypted (see S 5.68 Use of encryption procedures for network communications).
Furthermore, it must be checked whether the PBX system should be integrated into the security concept against malware.
Shielding an internal remote access port using a modem
The following figure represents a typical scenario of an internal remote access port addressed via a remote administration port using a modem. The PBX system PBX 1 is administrated directly from the maintenance location using the V.24 maintenance interface. The PBX system PBX 2 is administrated from the maintenance location using modem 1 - PBX 1 - PBX 2 - modem 2 - V.24 maintenance interface.
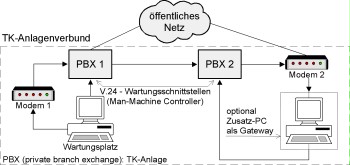
Figure: Establishing remote administration via modem
In such a case, the following safeguards for separating against accesses from external networks may be taken:
- No direct outward dialling for the connection from modem 2
The modem connection used to establish access to the administration port of the system should not be authorised to direct outward dialling in any case! This minimum requirement should be checked first. This is to prevent it being possible for the modem to be dialled directly from the outside. - Non-disclosure of the telephone number of the maintenance port of modem 2
In order to make any misuse more difficult right from the beginning, the telephone number of the maintenance device should not be disclosed in telephone directories. Only the persons who directly require this number should know it. - Use of dedicated lines (optional)
The use of dedicated lines not routed over switching facilities for remote connections is one of the most secure methods for preventing external access to the remote access ports. Since this method is normally very expensive, it will only be used in exceptional cases.
In order to ensure that only the authorised stations within the organisation's own network are able to access the remote access ports, the following safeguards must be implemented:
- Formation of closed user groups (CUGs)
In some PBX systems, CUGs can be established in a cross-system manner. These closed user groups constitute a network within the network. Therefore, all required remote accesses should be consolidated with the stations respectively authorised to access in such CUGs. - Automatic callback
The callback option of the modems should be used (see S 5.30 Activating an existing call-back option). If a PC gateway is used, the callback should be started from there. - Restriction of the rights of the remote port (optional)
If the PBX system supports rights administration for different ports, this option may be used in order to prevent security-critical activities using remote access ports and to only allow these locally. Many PBX systems do not have this option, however. In such cases, the transactions executable using a port may be restricted by additional products such as port controllers.
In order to ensure that only the authorised persons within the organisation's own network are able to access the remote access ports, the following safeguards must be implemented:
- identification and authentication,
- challenge response procedures for authentication (optional).
Shielding an internal remote access port using ISDN networking
A PBX system may also be accessed remotely using ISDN. To this end, the PCs with management tasks must be equipped with ISDN cards. In order to shield the access, a closed user group should be established by evaluating the telephone number of the management PC (CLIP: Calling Line Identification and Presentation). In many PBX systems, this limitation of the remote access to a telephone number is integrated.
Shielding direct system access ports (Direct Inward System Access, DISA)
Direct system access ports should be blocked as far as possible. If this is not possible, the authorisations should be set in such a way that direct system access may only be performed using a dedicated port. This way, it is possible to route the DISA access via a gateway. An example of such a shielding is illustrated by the following figure:
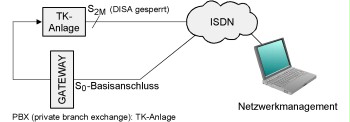
Figure: Shielding direct system access ports
Establishment and accommodation of a network management centre
The advantage of central network management is that no physical access to the PBX system is required for the day-to-day administrative activities, along with a comfortable system administration.
If establishing a central network management is considered, this must be accommodated in a secure area. Access to this centre must be controlled by organisational safeguards. Corresponding specifications can be found in module S 2.4 Server room. The management computers that may be used to perform the work should also be protected by appropriate safeguards. Examples can be found in S 3.9 Windows XP client and S 3.4 Unix client.
Review questions:
- Has the external remote maintenance of the PBX system been prevented?
- Are the users of the remote access port of the PBX system known?
- Has the access to the PBX remote maintenance centre been restricted to the necessary persons?
- Has the administration access of the PBX system been protected against unauthorised access?

