S 5.62 Suitable logical segmentation
Initiation responsibility: IT Security Officer, Head of IT
Implementation responsibility: Administrator
With the help of appropriate network components, it is possible to segment a network logically even if a fixed physical segmentation is already in effect. This can be achieved using switches which operate on layers 2 and 3 of the OSI model. As these switches recognise the protocols used on layers 2 and 3, virtual LANs (VLANs) can be formed by controlling the data flow between the switch ports. This makes it possible to create network groups which are not mapped as such by the physical segmentation. In particular, this allows a quick and dynamic formation and rearrangement of groups without any modifications to the physical layout of the network.
As in the case of physical segmentation on layers 2 and 3, criteria concerning confidentiality, availability and integrity are also to be applied here. Criteria for suitable logical segmentation can be applied in a similar way to the criteria for physical segmentation. Here, it must be taken into consideration that VLANs on a switch are not necessarily suitable to securely separate two subnetworks with different protection requirements. If two subnetworks with different confidentiality requirements of the transmitted data are to be implemented as VLANs, additional safeguards will generally be required in order to ensure secure separation.
The following illustration shows one possibility of forming a VLAN with the help of several layer-3 switches. The physical links between the stations and the switches are represented by the connecting lines. Logical segmentation is performed through grouping into VLANs using switches.
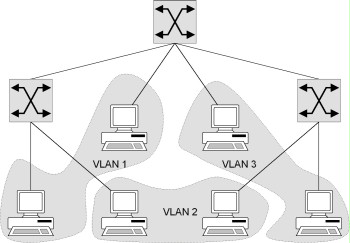
Figure: Formation of VLANs using several switches
If the VLAN structure shown above were to be achieved by means of a conventional physical segmentation, the layout shown in the figure below would be the result. The individual LANs can be mapped here by means of shared Ethernet segments, for example, and linked together with a bridge.
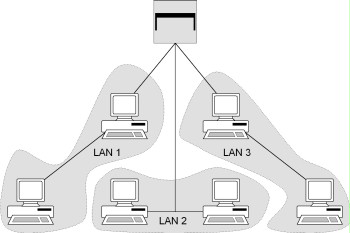
Figure: Formation of VLANs using a bridge
On the basis of VLAN-compatible network components, virtual LANs can be formed without any physical restructuring. Depending on the technologies used, these VLANs are created through segmentation on layers 2 and 3, in a similar way to LANs. Like LAN segmentation, this allows a network to be separated into areas (see S 5.61 Suitable physical segmentation). Depending on the product in use, different functions are available for the formation of VLANs. Some products allow the formation of VLANs on layers 2 and 3, which can only be coupled by means of routers (and are thus termed secure VLANs). In this case, filter rules need to be defined for the router in order to ensure controlled transmissions between the individual VLANs. Other manufacturers even implement a routing function in layer-3 switches, which allows VLANS to be linked without the need for additional routers. In particular, the intended technologies and products must be checked to determine whether they fulfil requirements concerning the confidentiality and integrity of data.
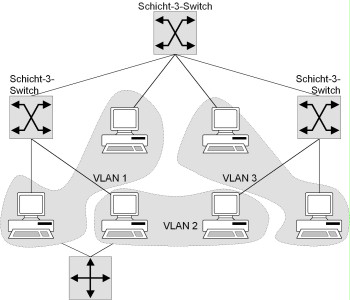
Figure: Formation of secure VLANs with layer-3 switches
In the case illustrated in the figure above, layer-3 switches are used to configure secure VLANs on layer 3 of the OSI model. The switches illustrated here do not have a routing function. VLAN 1, VLAN 2 and VLAN 3 operate as though they have been segmented by means of a router, although no routing takes place between them. In other words, VLAN 3 is not linked with any of the other VLANs; only VLAN 1 and VLAN 2 can communicate with each other via a router. Communications can be controlled by configuring the router in the required manner. Other products which implement a routing functionality in the layer-3 switches eliminate the need for the displayed router, and allow routing with the help of the switches.
A general recommendation concerning logical segmentation cannot be made. During the installation of a new network however, a check must be made as to whether VLANs would help fulfil requirements concerning availability, confidentiality and integrity more easily than a more elaborate physical segmentation. However, it must be noted that it is not easily possible to implement subnetworks with different protection requirements as regards confidentiality or integrity of the transmitted as VLANS on the same switch.
One advantage of logical segmentation is the easy and central configuration of new segments and reconfiguration of existing ones. On the other hand, secure remote access to the active network components also requires particular attention in this case, as segmentation here is only based on software configurations. During segmentation using VLANs, a balance therefore needs to be struck between the security requirements of the network (both as regards protection against unauthorised reconfiguration and against the possible overcoming of boundaries between the different VLANs) and the need for flexible reconfiguration of the network.
Review questions:
- Have requirements concerning availability, confidentiality and integrity been taken into account for logical segmentation of the network?
- Use of VLAN: Are all network components in use VLAN-compatible?
- Use of VLAN: Are all network components in use interoperable with regard to the VLAN function?

