S 5.77 Establishment of subnetworks
Initiation responsibility: IT Security Officer, Head of IT
Implementation responsibility: Head of IT, Administrator
IT systems in government agencies and companies are typically integrated into local networks (LANs), which in turn are connected to other networks. For technical reasons alone it is usually necessary to divide a medium-sized and large LAN into several subnetworks, for example because the number of IT systems per subnetwork or the total length of the cables is limited.
However, it is also recommended to establish subnetworks for information security reasons. On the one hand, it will then be possible to restrict sensitive data to certain areas in the LAN (confidentiality), and on the other hand to prevent incidents or attacks in a given subnetwork from having a negative impact on the operability of other subnetworks (integrity and availability).
Even if it is possible to establish communication connections to the LAN from outside, the network should be separated into subnetworks accordingly so that the LAN is protected against attacks from outside. VPN servers in particular should be placed in a special network referred to as an access network. This can be achieved by implementing additional demilitarised zones (DMZs) on the security gateway, for example.
It is first necessary to specify which IT systems should be operated in a common subnetwork. It is recommended to refer to the results of the protection requirements determination for this purpose and to proceed as follows:
- All IT systems and communication connections in a subnetwork should have the same protection requirement in terms of the basic value of confidentiality. This allows sensitive data to be restricted to a specially protected subnetwork whenever possible. The corresponding required safeguards can then be concentrated on these subnetworks.
- IT systems and communication connections with high or very high protection requirements in terms of availability or integrity should be operated in a separate subnetwork if possible. This ensures that incidents in other subnetworks will not have a negative impact on the proper operation of these components. Furthermore, it is also possible to quickly locate incidents and eliminate them.
The second step consists in the selection of suitable components for the connection of the subnetworks formed. Recommendations on this topic can be found in safeguard S 5.13 Appropriate use of equipment for network coupling.
Consideration should be given to the use of security gateways, especially for the connection of subnetworks containing components with very high protection requirements. This permits specific and secure control of the flow of data into the affected subnetwork and out of the subnetwork.
The following graphic shows an example of how the overall structure of a LAN could look after separating a subnetwork with a high protection requirement from the rest of the network using a security gateway. For the purpose of simplification, the security gateway is illustrated using one symbol even though it usually consists of several components (packet filter, application level gateway).
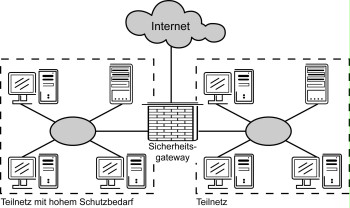
Figure: Example of the overall structure of a LAN
Recommendations for the technical realisation of the segmentation of the LAN can be found in the following safeguards:
- S 5.61 Suitable physical segmentation and
- S 5.62 Suitable logical segmentation
Review questions:
- Was the local network divided into subnetworks appropriately, based on the results of the protection requirements determination?
- Are VPN servers placed in isolated access networks?
- Have the network switching elements needed to separate the network into subnetworks been specified?

