S 5.118 Integration of a DNS server into a security gateway
Initiation responsibility: Head of IT, IT Security Officer
Implementation responsibility: Administrator
The Domain Name System (DNS) is used to convert computer names into IP addresses and vice-versa. It also provides information on the computer systems available in the network. This information is sometimes required for the internet connection to work properly, for example information about DNS servers or email exchangers for a domain. On the other hand, domain information may also be exploited by potential attackers when preparing attacks. For example, if a computer has a name such as "mssql01", an attacker may use this information to conclude that this presumably is a computer with a Microsoft operating system running a Microsoft SQL server.
Therefore, a separation between the name resolution for internal purposes and the "external" name resolution should be introduced for DNS. Internal domain information should be hidden from the untrustworthy network. Computers in the internal network should not be equipped with any DNS names that may be resolved from the outside if they have a "public" IP address. If private IP addresses from the address ranges of the RFC 1918 are used in the internal network, these must be resolved by an internal name server anyway.
Specifically DNS server products have again and again constituted a source of problems in the past due to security gaps. Due to the special importance of the domain information and the increased susceptibility of the DNS software as basis for attacks, a special design is required in order to be able to securely provide and use domain information.
DNS servers for a three-tier security gateway
The design illustrated in the following figure is recommendable for securely integrating DNS into a three-tier security gateway, where no direct connection between the client in the trustworthy network and a DNS server in the untrustworthy network (or vice versa) is established. Two separate DNS servers are used.
The advertising DNS server containing the externally available information is located in a DMZ of the outer packet filter. It is configured as the "primary name server" for the domain of the trustworthy network and only contains the absolutely required information, for example:
- name and IP address of the external email server (MX entry)
- names and addresses of information servers providing information to the public. A differentiation between the servers located upstream of the application level gateway (ALG) and servers located downstream of the ALG must be made. For the former, the address of the server must be entered; for the latter, the address of the ALG must be entered.
The resolving DNS server is installed in a DMZ of the internal packet filter. It contains the information about the computers of the internal network. For computers of the internal network, the resolving DNS server is entered as DNS server: All clients of the trustworthy network exclusively use the resolving DNS server, for example, for Unix computers with the help of entries in the file /etc/resolv.conf. If a client in a trustworthy network requires domain information from the untrustworthy network, it provides the resolving DNS server with the request. As "forwarder", this server uses a public DNS server (or possibly a specifically configured forwarder) for queries referring to external names. Direct access to the resolving DNS server from the untrustworthy network should be prevented by packet filter rules so that the domain information of the trustworthy network is only visible in the trustworthy network.
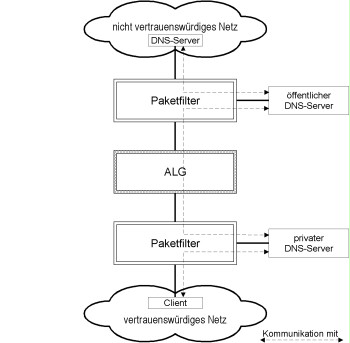
Figure 1: Integration of the DNS servers for secure communication between trustworthy and untrustworthy networks
The packet filter used must be configured in such a way that only the DNS service is permitted between the DNS servers, i.e. port 53 as source and/or destination port (depending on the perspective). No connections should be permitted from the advertising DNS server to the internal network. The server should be administered with the help of correspondingly secured connections (SSH).
The following table describes a possible configuration for access control that may be implemented using the corresponding packet filter rules. Here, it is assumed that the servers are administered with the help of an SSH connection from the internal network and that UDP is used as a carrier protocol for DNS. Logged data is transmitted to a log server using Syslog.
| Source | Destination | Decision | Notes |
|---|---|---|---|
| Communication of the public DNS server with the internet | |||
| External network | Advertising DNS server UDP port 53 | Permit | DNS queries and answers from the public network |
| External network | Other ports of the advertising DNS server | Prohibit | |
| Advertising DNS server | DNS server on the internet, all ports TCP and UDP | Permit | Resolution of external names by the DNS server |
| Communication of the external DNS server with the internal network | |||
| Advertising DNS server | All connections to the internal network | Prohibit | |
| Internal network (possible restriction to administration network) | Advertising DNS server port 22 (SSH) | Permit | Administration and data transmission are performed via SSH and SCP |
| Internal network | All other accesses to the Advertising DNS server | Prohibit | DNS queries from the internal network are performed using the internal server |
| Communication of the two DNS servers with each other | |||
| Resolving DNS server | Advertising DNS server UDP port 53 | Permit | The resolving DNS server forwards queries to the advertising server (a separate forwarder may possibly be set up) |
| Advertising DNS server | Resolving DNS server all ports UDP | Permit | |
| Communication of the internal DNS server with the internal network | |||
| Internal network | Resolving DNS server UDP port 53 | Permit | DNS queries from the internal network are performed using the resolving DNS server |
| Resolving DNS server, UDP port 53 | Internal network | Permit | DNS answers to the internal network |
| Resolving DNS server, other source ports | Internal network | Prohibit | |
| Internal network (possible restriction to administration network) | Resolving DNS server port 22 (SSH) | Permit | Administration and data transmission are performed via SSH and SCP |
| Logs | |||
| Resolving and advertising DNS servers | Log host UDP port 514 | Permit | Transmission of the logged data to the log host |
Table: Configuration for access rules
DNS servers in a simple security gateway
If only a simple security gateway (packet filter) is used, it is recommendable to nevertheless use two separate DNS servers (advertising and resolving DNS server). If the two DNS servers are located in two separate DMZs of the packet filter, the same rules as described above may be applied.
If the time and expense required for setting up two separate DMZs is too high or if setting up two separate DMZs is not possible due to technical reasons, more simple designs may be used. However, these only offer lower levels of protection and therefore it must be considered on a case-by-case basis whether the security level is still acceptable.
The advertising DNS server should be placed in a DMZ of the packet filter in any case. The resolving DNS server may be installed in the internal network, if required.
If only one DNS server is available which has to assume both the internal and external name resolution, this server should be installed in a DMZ of the packet filter. If possible, the DNS server software should be configured in such a way in this case that a differentiation is made between queries from the internal and queries from the external network and different data is provided, if required. However, this solution only provides sufficient levels of protection for small networks without any specific security requirements.
Domain registration with external service provider
For this alternative, important domain information is stored with an external service provider and made available by a separate DNS server. The difference to the scenarios described above mainly consists in the no longer applicable advertising DNS servers. DNS queries from the external network regarding domain information from the internal network are not sent to and answered by the internal advertising DNS server of the organisation, but to the DNS server of the external service provider. In the event of queries for external DNS names or IP addresses, the resolving DNS server uses the security gateway directly to access a DNS server in the external network, usually operated by the internet service provider.
For this integration variant tool, only the absolutely required domain information should be offered externally, for example name and IP address of the email server and the ALG. For particularly harmless internal users of the organisation, the resolving DNS server may also be operated in the internal network instead of in a DMZ of the internal packet filter, which makes packet filter administration easier (if only to a small extent).
The advantages of this variant include the low investment costs and the low complexity when integrating into a security gateway. Moreover, a service provider may dispose of redundant systems, which often is not the case for internal solutions of an organisation.
Review questions:
- Are the name resolution for internal addresses and the name resolution for external addresses separated?
- Has the information entered on the public DNS server been restricted as far as possible?
- With regard to to DNS servers in a three-tier security gateway: Has a public DNS server been set up as primary name server for the domain of the trustworthy network?
- with regard to DNS servers in a three-tier security gateway: Has the private DNS server been installed in a DMZ of the internal packet filter?
- With regard to DNS servers in a three-tier security gateway: Do all clients of the trustworthy network only use the private DNS server?
- With regard to DNS servers in a three-tier security gateway: Does the private DNS server use the public DNS server as forwarder for queries with regard to the external names?
- With regard to DNS servers in a three-tier security gateway: Is direct access to the private DNS server from the untrustworthy network prevented by packet filter rules?
- With regard to DNS servers in a three-tier security gateway: Have the packet filters been configured in such a way that only the DNS service is permitted between the DNS servers?
- With regard to DNS servers in a three-tier security gateway: Has it been ensured that no connections are permitted from the public DNS server to the internal network?
- With regard to DNS servers in a simple security gateway: Has the public DNS server been installed in a separate DMZ of the packet filter?

