S 5.137 Use of NAT for VoIP
Initiation responsibility: IT Security Officer, Head of IT
Implementation responsibility: Head of IT, Administrator
NAT (Network Address Translation) allows private/internal IP addresses to be translated to public/external IP addresses. When converting the addresses, private source IP addresses and the associated private source ports are translated to public source IP addresses with public source ports by a corresponding NAT gateway. In order for the NAT gateway to be able to forward return packets and/or incoming packets directed to the public IP address to the correct internal host, it maintains a corresponding assignment table containing the public IP address/port to private IP address/port assignments.
Through NAT, the source IP address and the source port number are modified in the UDP and/or TCP header of the media stream. The information on the source IP address and the source port in the message part of the signalling information remains unchanged, though. As a result, media streams cannot be sent to a VoIP telephone located behind a NAT gateway. VoIP devices located in the internet cannot send any media streams to a VoIP telephone located behind a NAT gateway, since the private IP address will not be routed to the internet.
The following sections point out the possibilities available when operating VoIP in a NAT environment.
MIDCOM
MIDCOM stands for Middlebox Communications and is a draft from the IETF that offers a solution for the NAT and firewall problems arising in conjunction with VoIP. A MIDCOM system consists of a middlebox and a server controlling and/or configuring the middlebox. The control server is a VoIP server (H.323 gatekeeper, SIP proxy, etc.) located in the signalling path that monitors the exchange of the SDP (Session Description Protocol) data. Based on this data, the server controls the middlebox (NAT gateway, firewall) that enters the assignments in the NAT table and opens the corresponding ports using the MIDCOM protocol. The MIDCOM architecture is illustrated in the following figure.
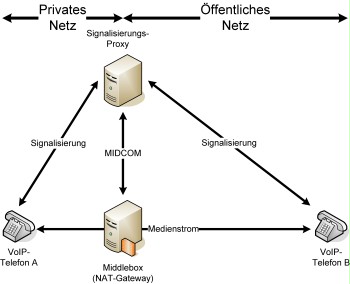
Figure: Diagram of the MIDCOM architecture
Since the control server needs to communicate with the internet, this server must also be protected by a firewall. A successful attack on the control server may make other attacks possible under some circumstances, especially on the middlebox (NAT gateway, firewall) it controls. This may lead to additional, serious threats.
Session Border Controller
Since MIDCOM is still in the draft phase, manufacturers have begun to launch proprietary solutions solving the problems associated with NAT and firewalls. These session border controllers often offer additional functionality, for example the ability to monitor service level agreements (SLA), call admission control, and charge calculation (billing). The systems are offered as appliances or servers. The following figure shows an example of the use of a session border controller consisting of one signalisation proxy and one RTP proxy.
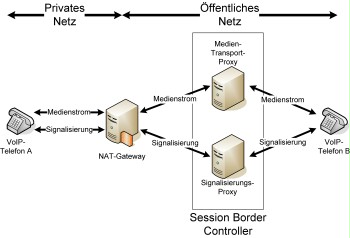
Figure: Example of the use of a session border controller
In this example, all traffic (signalisation and media stream) passes through the session border controller. VoIP telephone B does not know the actual IP address of VoIP telephone A.
UPnP
UPnP (Universal Plug and Play) is an industry standard that is being used more and more often, especially for private use. The UPnP architecture is intended to make it easier to network PCs and terminal devices (for example, printers, scanners, WLAN access points). Using UPnP, applications can learn the public IP address of the NAT gateway, specify the NAT assignment to be used, and then remove the specification after terminating a session. A so-called lease time may also be specified determining how long the NAT assignment is valid. When several NAT gateways are connected in series, though, UPnP cannot be used to go through the NAT gateways.
STUN
With the help of STUN (Simple Traversal of User Datagram Protocol (UDP) Through NATs), end systems located behind a NAT gateway are able to determine their public IP address and learn the NAT assignments in the gateway. Symmetric NAT is not supported by STUN, though. The NAT assignments are transmitted in the signalling protocol for VoIP so that incoming RTP streams can be sent to the appropriate NAT assignment in order to reach the VoIP telephone located behind the NAT gateway. The STUN technology is already supported by many VoIP telephones and is offered by most VoIP Providers.
TURN
TURN (Traversal Using Relay NAT) permits systems behind a NAT gateway or firewall to receive incoming TCP and UDP connections. At the same time, TURN prevents this capability from being used to operate publicly accessible servers such as web servers and email servers by only allowing one session per peer for each combination of an IP address and a port. In contrast to STUN, the use of TURN also permits systems behind symmetric NAT gateways to receive incoming connections. TURN is a simple client/server protocol with authentication being performed based on passwords.
ICE
Since all media streams are fed through the TURN server when TURN is used, it only makes sense to use a TURN server when it is impossible to receive incoming connections using STUN. ICE (Interactive Connectivity Establishment) is a method for SIP in order to allow the use of NAT based on several addresses made known using SDP, with the protocols STUN, TURN, RSIP, and MIDCOM being used. It is assumed that a client has several addresses available (for example addresses it learned from STUN or TURN) it can use to receive the media streams. Since the end systems do not know which address works, the addresses are checked one after the other according to their priority, whereby the address with the highest priority is checked first. The priorities are specified based on the lowest cost and the maximum QoS (quality of service) and are then listed one after the other in the SDP. ICE is designed for SIP, but also works with RTSP and H.323, and permits end devices to be operated independently from the NAT environment.
If the LAN is connected to the internet via a NAT gateway, it is recommended to select all of the mechanisms presented. The decision made must be documented.
Review questions:
- Is NAT (Network Address Translation) used within the framework of VoIP operations?
- Has the VoIP architecture been secured according to the security policy in accordance with the state-of-the-art?
- Is the communication of the VoIP component implemented using state-of-the-art procedures and protocols?

