S 5.152 Exchange of information and resources using peer-to-peer services.
Initiation responsibility: Head of IT, IT Security Officer
Implementation responsibility: Administrator
Peer-to-peer (often abbreviated to P2P) refers to the exchange of information between IT systems with equal rights (peers). With peer-to-peer every IT system can offer or use services. The communication connection established for this purpose can be used by several IT systems to share resources with each other in a decentralised manner. The typical functions of a server and a client are thus united on one IT system.
Peer-to-peer applications are often used to provide the following services to other peers:
- use of printers which are connected locally to an IT system by users of other IT systems,
- access to storage areas of hard disks installed in the IT system or connected locally (file sharing),
- direct communication via short messages(messaging), and
- internet telephony.
Advantages of peer-to-peer services
In contrast to a server-based architecture, peer-to-peer services offer numerous advantages:
- A dedicated server increases purchase and operation costs.
- If the central server fails, the resources are no longer available (single point of failure). If a client fails in peer-to-peer services there are generally enough other clients to take over.
- Geographically adjacent clients can directly exchange information with each other in a more efficient manner than when a server is used for this which is installed far away.
- Servers require a higher bandwidth, more CPU performance, and larger hard disks and memories than clients. In peer-to-peer networks, these requirements can be distributed over the clients where unused resources can be used.
- Shared information is often stored on several clients simultaneously and therefore redundantly.
However, the use of peer-to-peer services has also a large number of disadvantages which in may cases are due to the lack of centralisation (see also T 2.147 Lack of centralisation with peer-to-peer). For example, it is not possible to centrally check the exchanged information for malware.
Architecture
Depending on the requirements, peer-to-peer services can be used in a local network only or in the entire internet. The number of IT systems which can share these resources with each other ranges from only a few selected peers to an unmanageable number of unknown peers. Generally, two types of peer-to-peer services can be differentiated:
- Local peer-to-peer services
In local peer-to-peer services, individual clients can share resources with other clients in a LAN. These shares can often be administrated directly by the operating system. An example of this is file and printer sharing in Windows operating systems.
The access of these services can often be restricted using passwords or a selection of IP addresses. In general, these services are not used beyond the local network and are rejected at the security gateway (firewall).
As these services do not require their own server, it is possible to save costs of purchasing hardware and software.
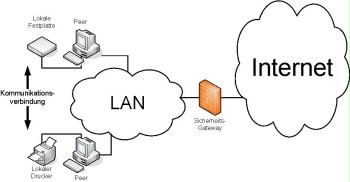
Figure: Local peer-to-peer services in a LAN
- Public peer-to-peer services
Public peer-to-peer services can be used to exchange information with users who do not have access to the LAN. For this, additional applications must be installed on the relevant IT system to enable the users to use the services provided by other peers. As in peer-to-peer services information is exchanged directly between two or more IT systems, additional information on who these IT systems can be reached is required in order to establish a connection. For this reason, especially in case of very large peer-to-peer networks, an overview of which peer which resources are provided on should be available.
On principle, the following types exist:- Central peer-to-peer services:
The installed application establishes a connection to a server that administers information about other peers. For this purpose, the application of the peer must first transmit information about the resources it would like to provide to the server. Only after this step can IT system generally access information about the other peers logged in. This includes, for example, the IP address, the user, and the content provided. With the help of this information a direct connection can be established to the remote peer and its resources can be used. In case of a failure of the central server, the contact information is no longer available to the excluded IT systems and the peers are no longer able to establish data connections between each other. This results in a failure of the entire peer-to-peer network. - Distributed peer-to-peer services:
For distributed peer-to-peer services, no central server is required to administer the users connected. The IT systems of the users of these services establish data connections between each other in order to exchange information about the resources provided. In addition to searching the resources of the IT systems to which a direct connection has been established, it is also possible to retrieve information about other peers which have established a data connection in turn. Since every peer can establish a connection to several peers, a network is created which can be used by every peer to retrieve information about the resources provided by other peers. These distributed peer-to-peer services require that the application be established by a peer which is part of this network in order to be able to also become a member of the network. The contact information required for this must be previously known. Since many networks benefit from a large number of connected IT systems, this contact information is often published on websites. - Hybrid peer-to-peer services
Hybrid peer-to-peer services are similar to central peer-to-peer services. The only difference is that several independent servers can be used. As with central peer-to-peer services, the peers transmit the resources they provide and contact information on how they can be reached to a server. The servers then forward this information to other servers. If required, the peers can access the resources of other peers which are not administered by the same server.
- Central peer-to-peer services:
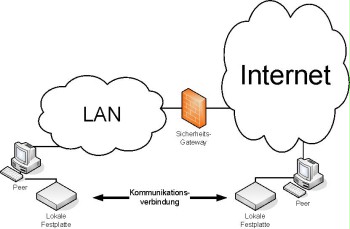
Figure: Public peer-to-peer via internet (file sharing)
Alternatives for the use of peer-to-peer services
There are only a few services where peer-to-peer communication between IT systems is absolutely necessary. For example, resources can also be provided centrally by servers. Only the use of servers allows for central implementation of specifications, for example, that only authorised persons may access the information. The following services which can usually be distributed over peer-to-peer networks can be provided centrally:
- Provision of printers
If several persons in a LAN require access to printers these can be made available centrally in the network. The use of network-capable printers and administration via printer servers is suitable for this (see S 3.6 Printers, copiers, and all-in-one devices). - File sharing
Instead of sharing storage on several clients (peers) in the LAN, information can be stored centrally on a file server. If only the users within a LAN should be able to access the server, Samba servers (see S 5.17 Samba) or NFS servers (see S 3.2 Servers under Unix), for example, can provide the information.. If external users should also be able to access the information, the information can be stored on an externally accessible web server (see S 5.4 Web server). - Messaging
If it is necessary to send short messages without using e-mail, operation of an Instant Messaging Server, such as Jabber, should be considered. This server can be used to centrally check the messages for malware.
Communication with external communication partners can also be realised by means of a central Instant Messaging Server which is operated by the organisation and which can be accessed from inside the organisation as well as well as from the outside. - VoIP (Voice over Internet Protocol) and internet telephony
VoIP solutions as described in module S 4.7 VoIP differentiate between signalling and media transport. Signalling often requires servers on which the subscribers are administrated. In many solutions, the voice information is exchanged directly between the users after a call has been initiated between two or more users via signalling. This type of peer-to-peer makes sense in a LAN and should be used.
Peer-to-peer should not be used for telephony outside the borders of a LAN; for example, an organisation should not allow VoIP communication for the purpose of communicating with external communication partners ("internet telephony"). In this case, signalling as well as media transport should be bundled on a concentrator, similar to a proxy (see S 4.289 Restricting the accessibility via VoIP). In this way, the establishment of direct connections between individual peers to external communication partners, who are located in the internet, for example, is avoided.
Recommendations for the use of local peer-to-peer services
If possible, dedicated servers should be used for exchange of information instead of shares via peer-to-peer services. In exceptional cases, however, the use of peer-to-peer solutions may be necessary, for example, for VoIP. Therefore, it must be defined:
- which peer-to-peer services may be used,
- which information may be exchanged, and
- which services may be used.
If required, the users must be trained in the use of peer-to-peer services. It must be ensured that the peer-to-peer services are restricted to the LAN only.
Recommendations for the use of public peer-to-peer services
In general, uncontrolled flow of information from a LAN must be prevented. This also includes direct peer-to-peer connections from peers to IT systems which are not located in the LAN. Due to lack of centralisation, information can leave (e.g. confidential information) or enter (e.g. malware) the LAN unchecked. The following safeguards can be implemented to prevent the use of public peer-to-peer services:
- Local packet filters
Using local packet filters, it is possible to restrict the communication of the client to a few IT systems. For example, the filter rules can be defined such that communication is only allowed with servers.
Based on the IP address of the server and the port number of the permitted service, undesired communication can be made more difficult. Using local packet filters, the use of local as well as public peer-to-peer networks can be prevented. - Central filtering at the security gateway (firewall)
In general, the security gateway should only allow the necessary communication in or from the local network; all other connections should be rejected (see S 3.1 Security gateway (firewall)). If the security gateway prevents communication of the clients from the LAN with IT systems in the internet, the use of public peer-to-peer networks can be prevented. - Policy
In addition to technical recommendations, the employees of the organisation should not be allowed to use peer-to-peer services. This instruction can be laid down in the security policy for users.
If peer-to-peer services are to be used in the organisation this must be decided by the management of the organisation. The IT security officer must be involved in this decision and the decision including the residual risks must be documented.
Review questions:
- Does a policy that covers the use of peer-to-peer services exist?
- Has it been documented which peer-to-peer services are used by whom and which information is exchanged?
- Are safeguards implemented to prevent unauthorised use (persons, information, services) of peer-to-peer services?
- Has the use of peer-to-peer services been approved by the management and have the residual risks been documented and accepted?

