S 3.303 Storage systems and storage networks
Description
Several servers or even end devices can use a storage system simultaneously over a storage network. Advantages include lower administration costs and simpler data backup procedures. Since storage systems consisting of several networked units usually use a dedicated storage network, these systems are often referred to in the literature as "storage networks". Since not only the network but many other components too must work together during the storage process, this module examines storage systems and storage networks together. A storage system here refers to a central instance that provides the other systems with storage space. The data backup devices connected to the storage system are examined in module S 1.12 Archiving. Design aspects of the data backup are explained in module S 1.4 Data backup policy.
The use of storage systems makes storage consolidation possible in the organisation. Consolidation means the following:
- Storage capacity is "drawn off" the individual servers and collected in central systems.
- An increase in the disk space requirements can be fulfilled flexibly through the use of the disk space available centrally without requiring modifications to the hardware.
- Applications can share the disk space and the information contained there.
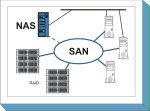
Storage systems are designed as Network Attached Storage systems (NAS) or as Storage Area Networks (SANs). In extremely simplified terms, NAS systems are special servers in the network. Access to the memory is "file-based". SAN systems, on the other hand, are a special, high-performance, but also technically complex way of connecting disk space to server machines. Access to this system is "block-based".
Network attached storage systems use the existing Ethernet network with a TCP/IP protocol such as NFS (Network File System protocol) or CIFS (Common Internet File System), so that the connected computers can access the data media. They often operate as pure file servers. For this reason, many providers use the term "filer" for such systems. To NAS systems, module S 3.101 General server must thus also be applied.
Storage area networks are generally created using a dedicated network between the storage systems and the connected servers. A SAN consists of one or more disk systems, the active elements in the storage network (SAN switches), additional storage systems (e.g. tape drives), and the connected servers. Module S 4.1 Heterogeneous networks must also be implemented for the dedicated storage network of SAN systems and for combined storage systems.
Threat scenario
The following typical threats to the IT-Grundschutz of storage systems are assumed to exist:
Force Majeure
| T 1.2 | Failure of the IT system |
Organisational Shortcomings
| T 2.1 | Lack of, or insufficient, rules |
| T 2.4 | Insufficient monitoring of security safeguards |
| T 2.5 | Inadequate or non-existent maintenance |
| T 2.7 | Unauthorised use of rights |
| T 2.27 | Lack of or insufficient documentation |
| T 2.54 | Loss of confidentiality through hidden pieces of data |
| T 2.82 | Poor planning of the archive system location |
| T 2.109 | Lack of, or inadequate, planning of the storage system |
Human Error
| T 3.9 | Improper IT system administration |
| T 3.38 | Errors in configuration and operation |
| T 3.79 | Incorrect assignment of SAN resources |
Technical Failure
| T 4.13 | Loss of stored data |
| T 4.53 | Insecure default settings for storage components |
Deliberate Acts
| T 5.1 | Manipulation or destruction of equipment or accessories |
| T 5.2 | Manipulation of information or software |
| T 5.4 | Theft |
| T 5.7 | Line tapping |
| T 5.8 | Manipulation of lines |
| T 5.18 | Systematic trying-out of passwords |
| T 5.20 | Misuse of administrator rights |
| T 5.28 | Denial of services |
| T 5.57 | Network analysis tools |
| T 5.102 | Sabotage |
| T 5.129 | Manipulation of data via the storage system |
| T 5.130 | Manipulation of the configuration of a storage system |
Method recommendation
To secure a storage system, other modules in addition to this module must be implemented depending on the results of the modelling process performed according to the IT-Grundschutz guidelines.
A series of measures must be implemented for the successful design and operation of a storage system. It starts with the strategic decision of which type of system to select. The concept covers all phases from installation to operation. When the end of the operating phase is reached, measures for the proper disposal of the system must be implemented.
Parallel to the operating phase, a suitable contingency plan must ensure that operations can also be maintained in the event of an emergency. In addition, information security management and auditing ensure that the guidelines are also complied with.
The steps to be taken to accomplish this as well as the safeguards to be implemented in each phase are listed in the following:
Planning and Design
A requirements analysis must be performed in order to make a decision on which type of storage system can be used in the organisation, and then a storage system is selected. It must first be clarified which technology is appropriate (see also S 2.362 Selection of a suitable storage system and S 2.351 Planning the use of storage systems). Planning must always start with the applications to be supplied with memory. The security requirements on the storage system and the storage network can only be defined reasonably when the applications are examined first. Important planning parameters include the expected future growth of the applications as well as the necessary performance and security requirements. The design of the NAS or SAN components must be defined taking foreseeable developments and well-founded growth forecasts into account so that these central IT components will fulfil the requirements of the organisation in the long term.
In addition to the estimation and planning of the storage capacity required, it is especially important to examine where the NAS or SAN systems could be installed (see S 1.59 Suitable siting of archive systems). When looking for a location, it is necessary to critically examine if the server rooms or the computer centre are technically and organisationally suitable for the installation of storage systems. It is then sited and installed securely in the implementation phase.
An appropriate data backup policy must be planned in conjunction with the planning of a storage system. To do this, the data backup policy (S 1.4 Data backup policy) of the organisation must be adapted organisationally and technically to the requirements resulting from the use of a storage system.
The requirements on the storage systems, which are derived from the requirements of the organisation, are to be specified in writing in a security policy (see S 2.352 Drawing up a security policy for NAS systems and S 2.353 Drawing up a security policy for SAN systems)
When higher demands are placed on the availability or scalability, it is recommended to use a high availability storage system (see also S 2.354 Use of a high availability SAN configuration).
Purchasing
Once the organisation has defined the basic requirements for the storage systems, possible providers and suppliers must be examined (S 2.355 Selection of suppliers for a storage system).
Service level agreements must be made with the suppliers of the hardware components of the storage system. These service level agreements must include response times which, when considered realistically, are appropriate for the Service Level Agreements defined in planning and, altogether, for the requirements placed on the availability of the system (S 2.356 Contractual arrangements with SAN service providers).
Implementation
After the organisational and planning preparation has been performed, the NAS system can be installed or the SAN system can be built together with the dedicated network and storage components. Here, the following safeguards must be taken into account:
- A secure basic configuration of the authorisation mechanisms of the storage system is necessary (see S 4.274 Secure basic configuration of storage systems).
- The storage system should be placed in a secure network for administration purposes, if this is possible (S 2.357 Setting up an administration network for storage systems).
In this phase, the security policies and the requirements specified by the organisation must be coordinated. All administrators dealing with the NAS or SAN system must be trained on the implemented solution (see S 3.54 Administrator training on the storage system).
When building a SAN system, the logical assignments between servers and components of the storage system are to be specified according to the requirements and plan specified in writing (see S 5.130 Protection of SANs by segmentation).
System documentation must be prepared using the knowledge gained during the test phase. All hardware and software used as well as all installation steps and each individual configuration must be documented in the system documentation (see S 2.358 Documenting the system settings of storage systems).
Operation
After the initial installation and a test operation phase, regular operations can be initiated. The following security aspects must be taken into account in this phase:
- Secure operation of the storage system is a prerequisite for the ability of the storage system to provide its functionality. The utility programs used to support the operating functions of the storage system and which require a high level of authorisation must be secured (see S 4.275 Secure operation of storage systems).
- Storage systems must be monitored during operation, and they must also be maintained. The maintenance tasks required for a storage system are described in S 2.359 Monitoring and administration of storage systems.-
- In addition to monitoring and maintenance, which are intended primarily to ensure the technical availability, there are other security-related aspects that need to be monitored (S 2.360 Security audits and reporting for storage systems).
Disposal
Recommendations for the deinstallation of individual components and for complete systems, for example after the routine operation phase is over, can be found in safeguard S 2.361 Deinstallation of storage systems.
Contingency Planning
The use of storage systems requires the existing IT contingency plans to be revised and adapted to the new situation. Recommendations for contingency planning can be found in safeguard S 6.98 Contingency planning for storage systems.
The bundle of security safeguards for this module is presented in the following.
Planning and design
| S 2.351 | (A) | Planning the use of storage systems |
| S 2.352 | (A) | Drawing up a security policy for NAS systems |
| S 2.353 | (A) | Drawing up a security policy for SAN systems |
| S 2.354 | (Z) | Use of a high availability SAN configuration |
| S 2.362 | (A) | Selection of a suitable storage system |
Purchasing
| S 2.355 | (C) | Selection of suppliers for a storage system |
| S 2.356 | (C) | Contractual arrangements with SAN service providers |
Implementation
| S 1.59 | (A) | Suitable siting of archive systems |
| S 2.357 | (B) | Setting up an administration network for storage systems |
| S 2.358 | (A) | Documenting the system settings of storage systems |
| S 3.54 | (A) | Administrator training on the storage system |
| S 4.80 | (B) | Secure access mechanisms for remote administration |
| S 4.274 | (A) | Secure basic configuration of storage systems |
| S 5.130 | (B) | Protection of SANs by segmentation |
Operation
| S 2.359 | (B) | Monitoring and administration of storage systems |
| S 2.360 | (B) | Security audits and reporting for storage systems |
| S 4.275 | (A) | Secure operation of storage systems |
Disposal
| S 2.361 | (C) | Deinstallation of storage systems |
Contingency Planning
| S 6.1 | (A) | Development of a survey of availability requirements |
| S 6.98 | (A) | Contingency planning for storage systems |

