S 4.2 Network- and Systemmanagement
Description
A management system for a mainly local computer network (LAN, VLAN) is used to centrally administer as many of the hardware and software components in the local network as possible. Such systems are designed to support the system administrators to the greatest possible extent in their daily work. There is a basic distinction between network management and system management. The differences result from the components that are managed in each case.
Network management includes all the precautions and activities for securing the effective use of a network. For example, this includes checking that the network components are functioning correctly, monitoring the network performance and centrally configuring the network components. Network management is primarily an organisational problem which can only be supported by technical means, namely a network management system.
System management is primarily concerned with the management of distributed IT systems. Tasks here include, for example, central management of users, software distribution, application management, etc. In certain areas, such as configuration management (the monitoring and consolidation of system and network component configurations), it is not possible to draw a clear distinction between network and system management.
The (software) system used to manage a network and its components is always referred to below as the "management system". The components that it manages are called the "managed system". These terms are used particularly in the area of network management.
A network and system management framework is defined in ISO/IEC standard 7498-4 or as X.700 of ITU-T, according to which the tasks of a management systems are as follows:
- Configuration management
- Performance management
- Fault management
- Invoice management
- Security management
A specific system management product need not offer support in each of these areas. The manufacturers usually offer ranges of products designed in such a way that certain functions can be obtained as a module or as compatible individual products.
Network management is the older and more developed management discipline. By contrast, system management is a relatively new discipline, but is increasingly in demand due to the rapid growth in networking in companies and public agencies and the resulting increase in heterogeneity and complexity. The obvious goal is to integrate the two disciplines. The management products available at the moment are designed such that they are primarily intended for either network management or system management. Products which combine the two functions are still under development. As a rule, products that are designed for system management also allow access to network management information.
Due to the heterogeneity of the hardware and software encountered in modern-day networks, system management is an extremely complex task. System management is made even more difficult by virtue of the fact that close co-operation is required between the management software and the software requiring management. However, the software available today is generally not designed to work with a management system. This is partly due to a lack of standards which would, for example, guarantee sufficient security and partly due to the fact that relatively large software packages are supplied with their own management system because of the restrictions on disclosing the information necessary for managing the software. For example, Microsoft Internet Explorer has a management software, the "Internet Explorer Administration Kit (IEAK)", which allows the administrator to select security settings which cannot subsequently be changed by the user or can only be changed to certain default values. The functions of this tool are proprietary and are not subject to any standards.
The architecture of management software generally has a centralist structure. There is a central management station or control panel from which the system administrators can manage the network for which they are responsible together with the hardware and software it contains. The systems for network management in particular are based on this. As a result of the lack of standards in the area of system management, the available products often have a centralist architecture, the details of which, however, are proprietary, and therefore no general statement can be made about the architecture.
A network management system is usually based on a model which distinguishes between "manager", "agent" (also "management agent") and "managed objects". Other components are the protocol used for communication between the manager and agents, as well as an information database, the so-called "MIB" (Management Information Base). The MIB must be available to both the manager and each management agent. The idea is that management agents and their MIB are seen to be part of the managed system.
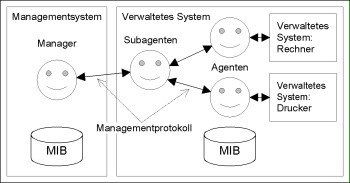
Figure: Network management system
An agent is responsible for one or more of the objects which are to be managed. It is possible to organise the agents hierarchically: In this case agents are responsible for the subagents assigned to them. There is always an object to be managed at the end of each command chain formed in this manner. An object to be managed is either an existing physical object (device), such as a computer, a printer or a router, or a software object such as a background process for
the administration of print jobs. In the case of devices that can be managed with a management system, the management agent has usually already been "permanently" integrated in the device by the manufacturer. If the agent does not understand the communication protocol used by the manager, a software management agent which can convert the protocol is required. In a similar manner, software components may already contain the management agent, or a particular management agent which is designed for the administration of this software component is required.
In order to address the individual components of the system to be managed, the manager exchanges information with the relevant agents. The type of protocol used for the communication has a considerable impact on the capabilities and, in particular, on the security of the management system.
Management systems can basically be divided into three categories according to the communication protocol used (see also S 2.144 Selection of a suitable network management protocol):
- SNMP (Simple Network Management Protocol), the widespread standard protocol of the TCP/IP-based system management..
- CMIP (Common Management Information Protocol), the less-common standard protocol of the ISO/OSI-based system management.
- Manufacturer's own protocol. It is normally possible to use so-called adapters to integrate the standard protocols, although there is usually only one SNMP connection.
The SNMP protocol is the one used most frequently. SNMP is an extremely simple protocol which recognises only five types of messages and is therefore easy to use. CMIP is mainly used to manage telecommunications networks and is irrelevant in management systems based on the Internet or Intranet, as it uses the OSI protocol stack rather than the TCP/IP stack.
Although system management systems usually have a centralist structure to allow the system to be managed from a management station, the exact architecture depends on the permissible size of the systems which can be managed and on the range of functions offered. These systems range from simple collections of management tools, which can be used next to each other in small networks without being integrated, to management platforms which can manage a world-wide company network comprising thousands of computers.
Certain management platforms use proprietary protocols for communication between the components. These systems usually have a much higher performance range and are not only used for network and system management but also offer resource management for entire organisations. Given the scant specifications for security mechanisms in the few standards which do exist, the manufacturers' own solutions also provide security-related (albeit not standardised) mechanisms, such as cryptographic techniques.
Threat scenario
The following typical threats to the IT-Grundschutz of a management system are assumed to exist:
Force Majeure
| T 1.1 | Loss of personnel |
| T 1.2 | Failure of the IT system |
Organisational Shortcomings
| T 2.27 | Lack of or insufficient documentation |
| T 2.32 | Inadequate line bandwidth |
| T 2.59 | Operation of non-registered components |
| T 2.60 | Strategy for the network system and management system is not laid down or insufficient |
| T 2.61 | Unauthorised collection of person-related data |
Human Error
| T 3.9 | Improper IT system administration |
| T 3.28 | Inadequate configuration of active network components |
| T 3.34 | Unsuitable configuration of the management system |
| T 3.35 | Disabling the server while in operation |
| T 3.36 | Misinterpretation of events |
Technical Failure
| T 4.31 | Failure or malfunction of a network component |
| T 4.38 | Failure of components of a network management system or system management system |
Deliberate Acts
| T 5.2 | Manipulation of information or software |
| T 5.8 | Manipulation of lines |
| T 5.9 | Unauthorised use of IT systems |
| T 5.18 | Systematic trying-out of passwords |
| T 5.28 | Denial of services |
| T 5.66 | Unauthorised connection of IT systems to a network |
| T 5.67 | Unauthorised execution of network management functions |
| T 5.86 | Manipulation of management parameters |
Method recommendation
To secure the information system examined, other modules will need to be implemented in addition to this module. These modules are selected based on the results of the IT-Grundschutz modelling process.
The system to be administered consists of individual computers, network switching elements and the physical network. Each of these components presents a potential security risk for the whole system. Generally speaking, these risks cannot be entirely eliminated through the introduction of management software alone. This is due to the fact that it is not usually possible to include all systems in a management system to the same extent. The basic requirements for the security of the system are defining and adopting a security policy across the whole organisation. In the case in question, this policy must be expressed in particular in the configuration of hardware and software. For this reason, particular attention should be paid to the safeguards covered in the Level 3 modules. A good starting point is module S 4.1 Heterogeneous networks.
As management systems are designed with a centralist structure, the central management station is of particular importance in terms of security considerations, and a particular effort must therefore be made to protect it. The central components of a management system should therefore be set up in rooms which meet the demands on a server room (see module S 2.4 Server Room). If there is no server room available then a suitable alternative location is a server cabinet (see module S 2.7 Protective cabinets).
The successful set-up of a network and system management system requires a series of safeguards, from design and purchase right through to operation.
The steps involved and the safeguards of relevance at the various steps are listed below:
- Creation of a management strategy based on the requirements arising from the existing IT system.
- Requirements analysis (see S 2.168 IT system analysis before the introduction of a system management system)
- Define concept (see S 2.169 Developing a system management strategy)
- Before purchasing the management system, the following steps are necessary:
- Formulate the requirements for the management product based on the management strategy (see S 2.170 Requirement to be met by a system management system)
- Select a suitable management product on the basis of these requirements (see S 2.170 Requirement to be met by a system management system).
- The security safeguards relevant to the operation of the management system are divided into the following areas:
- Installation, including the implementation of the management strategy (see S 4.91 Secure installation of a system management system) and.
- Ongoing operation of the management system (see S 4.92 Secure operation of a system management system).
- Reference should, of course, also be made to the existing safeguards for the ongoing operation of the managed system (see relevant Layer 3 modules).
The bundle of security safeguards for the module Network and system management is presented in the following.
Planning and design
| S 2.143 | (A) | Development of a network management concept |
| S 2.144 | (A) | Selection of a suitable network management protocol |
| S 2.168 | (A) | IT system analysis before the introduction of a system management system |
| S 2.169 | (A) | Developing a system management strategy |
Purchasing
| S 2.145 | (B) | Requirements for a network management tool |
| S 2.170 | (A) | Requirements to be met by a system management system |
| S 2.171 | (A) | Selection of a suitable system management product |
Implementation
| S 4.91 | (A) | Secure installation of a system management system |
Operation
| S 2.146 | (A) | Secure operation of a network management system |
| S 4.92 | (A) | Secure operation of a system management system |
Contingency Planning
| S 6.57 | (C) | Creation of an emergency plan for the failure of the management system |

