S 5.9 Novell eDirectory
Description
Novell eDirectory is a complex and versatile product that,
- on the one hand, can manage the integrated resources and their users across platforms in a government agency's or company's network, and
- on the other hand, can also be used as an Internet information base with secure and standardised access capabilities via suitable clients.
These two scenarios pose completely different threats to the use and operation of such a system. A combination of these operational scenarios poses a particularly great challenge from the perspective of information security.
Accordingly, the security of the underlying operating system is always a contributing factor for the security of the data stored in an eDirectory directory. However, the security of the underlying operating system is not covered in this module; detailed information relating to the secure operation of the operating system used can be found in the Layer 3 modules. Likewise, basic protection of the Novell eDirectory as a directory service must be implemented. For this, module S 5.15 General directory service must be applied in addition to this module.
eDirectory was developed from the Novell Directory Services (NDS) directory service, which was a component of the Netware 4 operating system. When it first appeared on the market, it constituted a major improvement on the NetWare 3 operating system. Novell is now offering these directory services as a stand-alone product called eDirectory that is completely independent of the Netware operating system. eDirectory can be installed and operated on a number of different operating systems. In the literature and resources, however, there are frequent references to the "Novell Directory Services", rendering NDS synonymous with eDirectory.
This module examines the English language version of eDirectory Version 8.6 in particular. The software supports the Netware, Windows NT/2000, Linux, and Sun Solaris platforms.
eDirectory can be used with special client software such as Novell Client for the Windows operating systems. These clients are integrated into the boot procedure of the corresponding computer and take over the task of authenticating users for the eDirectory directory service. A similar method is available for Unix operating systems (Linux, Solaris) that use the Pluggable Authentication Modules (PAM) mechanism, in which case the Novell Account Management Modules are used. The users are authenticated for the eDirectory directory service here as well when logging in.
Access via the LDAP interface is another possibility. Using this standardised interface makes it possible to use eDirectory with other applications and systems as well. The LDAP protocol is generally used as the method to access the Internet.
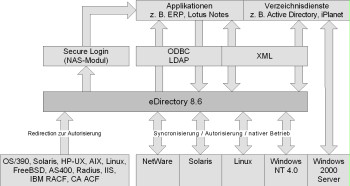
Figure: Diagram of the architecture
Furthermore, the eDirectory software offers a number of tools, including iMonitor, which provides monitoring and diagnostics capabilities in a web browser through the server of a directory service.
Threat scenario
Due to the large number of functions provided and the complexity of the software, an eDirectory directory service is subject to a series of threats. In addition, the threats posed to the operating system used, and especially to general server accesses and the file system, also need to be considered.
The following typical threats to the IT-Grundschutz of a Novell eDirectory system are assumed to exist:
Force Majeure
| T 1.2 | Failure of the IT system |
Organisational Shortcomings
| T 2.1 | Lack of, or insufficient, rules |
| T 2.2 | Insufficient knowledge of rules and procedures |
| T 2.7 | Unauthorised use of rights |
| T 2.69 | Lack of, or inadequate, planning of the use of Novell eDirectory |
| T 2.70 | Lack of, or inadequate, planning of partitioning and replication in Novell eDirectory |
| T 2.71 | Lack of, or inadequate, planning of LDAP access to Novell eDirectory |
Human Error
| T 3.9 | Improper IT system administration |
| T 3.13 | Passing on false or internal information |
| T 3.16 | Incorrect administration of site and data access rights |
| T 3.34 | Unsuitable configuration of the management system |
| T 3.35 | Disabling the server while in operation |
| T 3.36 | Misinterpretation of events |
| T 3.38 | Errors in configuration and operation |
| T 3.43 | Inappropriate handling of passwords |
| T 3.50 | Improper configuration of Novell eDirectory |
| T 3.51 | Errors in the assignment of access rights in Novell eDirectory |
| T 3.52 | Errors in the configuration of intranet client access to Novell eDirectory |
| T 3.53 | Errors in the configuration of LDAP access to Novell eDirectory |
Technical Failure
| T 4.10 | Complexity of access possibilities to networked IT systems |
| T 4.13 | Loss of stored data |
| T 4.33 | Poor-quality or missing authentication |
| T 4.34 | Failure of a cryptomodule |
| T 4.44 | Failure of Novell eDirectory |
Deliberate Acts
| T 5.16 | Threat during maintenance/administration work |
| T 5.18 | Systematic trying-out of passwords |
| T 5.19 | Abuse of user rights |
| T 5.20 | Misuse of administrator rights |
| T 5.65 | Denial of services in a database system |
| T 5.78 | DNS spoofing |
| T 5.81 | Unauthorized use of a cryptomodule |
Method recommendation
To secure the information system examined, other modules will need to be implemented in addition to this module. These modules are selected based on the results of the IT-Grundschutz modelling process.
A security concept specifically for the use of the eDirectory components should be created during the planning phase that can be integrated consistently into the existing organisation-wide security concept. The eDirectory system must be configured so that the existing security requirements can be implemented while meeting the additional eDirectory-specific requirements.
An eDirectory system is generally used in an environment together with other systems that control access to the internal network from the outside. In particular, the eDirectory may need to work with firewall systems and systems used for remote maintenance. For this reason, the corresponding safeguards from the modules relevant to the other systems affected must be taken into account as well when implementing the eDirectory-specific safeguards. In addition to the modules in Layer 3, the following modules also need to be mentioned:
- S 3.1 Security gateway (firewall), provided that the eDirectory systems are used in a firewall environment.
- S 4.4 VPN, if the eDirectory system is accessed using VPN
- S 5.7 Databases, as a general reference
A series of safeguards need to be implemented for the secure implementation of an eDirectory system, starting with the planning and installation phase and continuing through the operation phase. The individual steps to take as well as the appropriate safeguards to consider in each step are summarised below:
- After deciding to use eDirectory as a directory system, it is necessary to purchase software and any additional hardware needed. Since eDirectory can be used in a variety of application scenarios (see above), the hardware to be purchased, when this is necessary, depends on the operational scenarios planned. For this reason, the following safeguards must be implemented:
- The first step is to plan the use of the eDirectory system (see safeguards S 2.236 Planning the use of Novell eDirectory and S 2.237 Planning of partitioning and replication in Novell eDirectory).
- A security guideline which interprets the existing security guidelines in the context of eDirectory while defining supplementary guidelines relating specifically to eDirectory must be drawn up at the same time (see safeguard S 2.238 Specification of security guidelines for Novell eDirectory).
- Before the eDirectory system is used live in routine operations, the users and administrators must be trained in how to use the product. It is particularly advisable for administrators to receive intensive training in the utilisation of the product and acquire an in-depth knowledge of the security of the operating systems used (see S 3.29 Training on the administration of Novell eDirectory). Users should be briefed in detail on the available security mechanisms of the clients used (see S 3.30 Training on the use of Novell eDirectory client software).
- Once the preliminary organisational and planning tasks have been completed, the eDirectory system can be installed. The following safeguards must be implemented for this purpose:
- The installation can only be regarded as complete when the eDirectory systems have been made secure (see S 4.153 Secure installation of Novell eDirectory and S 4.154 Secure installation of Novell eDirectory client software). This will ensure that only authorised administrators will be able to access the eDirectory system in the subsequent configuration phase.
- The "raw installation" is followed by the initial configuration of the eDirectory system, see S 4.155 Secure configuration of the Novell eDirectory, S 4.156 Secure configuration of the Novell eDirectory client software, S 4.157 Setting of access authorisations to Novell eDirectory, and S 4.158 Setting of the LDAP access to Novell eDirectory.
- After configuration and a test operation phase, regular operations can be initiated. The following security-related aspects must be taken into account in this phase:
- An eDirectory system is normally subject to continuous changes. The security-relevant configuration parameters require constant modification in line with this. Moreover, in a distributed software architecture, security will depend on the security of all the subsystems. This applies especially to the eDirectory client software. The safeguards that are relevant to secure operation are summarised in S 4.159 Secure operation of Novell eDirectory and S 4.160 Monitoring of Novell eDirectory, and in the safeguards geared to the protection of communications (see S 5.97 Protection of communications with Novell eDirectory).
- As well as the safeguards for the protection of ongoing operations, the safeguards relating to contingency planning are also of central importance. Information on this subject is contained in S 6.81 Creation of data backups for Novell eDirectory.
Planning and design
| S 2.236 | (A) | Planning the use of Novell eDirectory |
| S 2.237 | (B) | Planning of partitioning and replication in Novell eDirectory |
| S 2.238 | (A) | Specification of security guidelines for Novell eDirectory |
| S 2.239 | (A) | Planning the use of Novell eDirectory on the Intranet |
| S 2.240 | (A) | Planning the use of Novell eDirectory on the Extranet |
Implementation
| S 3.29 | (A) | Training on the administration of Novell eDirectory |
| S 3.30 | (A) | Training on the use of Novell eDirectory client software |
| S 4.153 | (A) | Secure installation of Novell eDirectory |
| S 4.154 | (A) | Secure installation of the Novell eDirectory client software |
| S 4.155 | (A) | Secure configuration of Novell eDirectory |
| S 4.156 | (A) | Secure configuration of the Novell eDirectory client software |
| S 4.157 | (A) | Setting of access authorisations to Novell eDirectory |
| S 4.158 | (B) | Setting of the LDAP access to Novell eDirectory |
Operation
| S 4.159 | (A) | Secure operation of Novell eDirectory |
| S 4.160 | (B) | Monitoring of Novell eDirectory |
| S 5.97 | (B) | Protection of communications with Novell eDirectory |
Contingency Planning
| S 6.81 | (A) | Creation of data backups for Novell eDirectory |

