S 5.18 DNS-Server
Description
This module examines the basic security features of the Domain Name System (DNS) and the servers required for this. DNS is a network service to convert host names of IT systems into IP addresses. Usually, for a host name, the corresponding IP address is searched for (forward resolution). If, however, the IP address is known and the host name is searched for, this is referred to as reverse resolution. DNS can be compared to a telephone book which does not resolve names into telephone numbers, but into IP addresses. This constitutes a simplification for the users. Instead of numbers in the form of IP addresses which are difficult to remember, they must only know the host name of a computer in order to establish a connection to it. Which names belong to which IP addresses is managed in the domain name space. The domain name space has a hierarchical structure and is provided by DNS servers. DNS servers manage the domain name space in the Internet, but are often also used within the organisation's internal network. On the users' computers, there are so-called resolvers (coordinate converters), by means of which the requests are sent to the DNS servers and which return information on the domain name space as a response. In the proper meaning of the word, the term "DNS server" refers to the program used, but is, in most cases, also used as synonym for the computer on which this program is run.
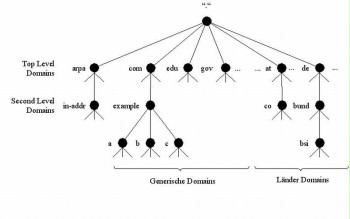
Figure: Domain name space
The Internet is a public environment, and information systems also operate IT systems which are to be accessible via the Internet, for example a web server or a mail server. In order to be able to establish an Internet connection, DNS is required. Here, the communication partner sends a corresponding DNS request to a DNS server. In this case, it must therefore be possible to access this DNS server from the public network; it is thus a publicly accessible IT system. Careful planning and proper, professional implementation are important for smooth operation, as a functioning name resolution is a basic prerequisite for a number of applications. For this reason, this module focuses on the availability and the integrity of DNS servers as well as on problems which might occur in the course of operating DNS servers.
This module describes the threats and safeguards applying specifically to a DNS server. The module must then be applied when DNS servers are operated in an information system. In order to ensure the security of DNS servers, additional modules must be implemented.
Threat scenario
The following typical threats to the IT-Grundschutz in connection with a DNS server are assumed to exist:
Force Majeure
| T 1.2 | Failure of the IT system |
Organisational Shortcomings
| T 2.1 | Lack of, or insufficient, rules |
| T 2.32 | Inadequate line bandwidth |
| T 2.100 | Errors on applying for and managing Internet domain names |
| T 2.152 | Lack of, or inadequate, planning of the use of DNS |
Human Error
| T 3.3 | Non-compliance with IT security measures |
| T 3.9 | Improper IT system administration |
| T 3.38 | Errors in configuration and operation |
| T 3.103 | Incorrect domain information |
| T 3.104 | Incorrect configuration of a DNS server |
Technical Failure
| T 4.22 | Software vulnerabilities or errors |
Deliberate Acts
| T 5.78 | DNS spoofing |
| T 5.151 | DNS flooding - denial-of-service attacks |
| T 5.152 | DNS hijacking |
| T 5.153 | DNS amplification attack |
| T 5.154 | DNS information leakage |
| T 5.155 | Exploitation of dynamic DNS updates |
Method recommendation
To secure the information system examined, other modules will generally need to be implemented in addition to this module. These modules are selected based on the results of the IT-Grundschutz modelling process.
In this respect, these other modules include module S 3.101 General server in particular and, depending on the operating system used, the modules S 3.2 Server under Unix, S 3.6 Windows 2000 Server or S 3.8 Windows Server 2003.
Due to the fact that at least a part of the DNS servers operated in an information system communicate with the Internet, module S 1.8 Handling of security incidents and module S 3.1 Security gateway (firewall) must be observed in order to ensure secure connection.
DNS servers manage all name information of an information system and thus contain information on the entire network infrastructure. For this reason, a DNS server should be installed in a server room or at least in a secure server cabinet; in this respect, see the corresponding modules S 2.4 Server room and S 2.7 Protective cabinets. In the case of outsourcing, module S 1.11 Outsourcing must be observed in addition.
This module describes the threats and safeguards applying specifically to a DNS server.
Planning and design
Before the selection of software components and the planning of the infrastructure can be started with, it should be checked if the desired domain name is still available. Since the DNS servers responsible must be specified when a domain name is registered, safeguard S 2.298 Administration of Internet domain names should be taken into account. If the use of DNSSEC is planned, it is of fundamental importance to draw up a concept for the management of cryptographic keys, as described in S 2.46 Appropriate key management. When planning the use of DNS, it must be defined which domain information has higher protection requirements. In addition, it must be decided how high the performance capacity of a DNS server needs to be. On the one hand, this applies to the IT system itself, i.e. the main memory in particular, and, on the other, the bandwidth of the network connection. In this context, it should also be planned how the DNS server will be integrated into the network infrastructure of the information system (S 2.451 Planning the use of DNS) and how the access rights (S 2.8 Assignment of access rights) will be assigned. The result of the planning activities must be documented in writing.
Purchasing
There are different software products in the area of DNS servers. In order to make the appropriate choice, the potential products must be analysed as to whether they meet the functionalities and security required according to the planning document (S 2.452 Selection of a suitable DNS server product).
Implementation
Depending on the selected DNS server, the administrators must be trained (S 3.73 Training the administrators of a DNS server). The training ensures that the administrators responsible are familiar with the individual configuration options. Based on the training and proper planning, a secure configuration ensuring the availability of DNS and the integrity of the information supplied should be developed: S 4.350 Secure basic configuration of a DNS server, S 4.198 Installation of an application in a chroot cage, S 4.351 Secure zone transfers, S 4.352 Secure dynamic DNS updates.
Operation
During live operations, it is important to inform yourself of current security gaps in order to install existing software updates, if any, or to introduce other security precautions; as stated in module S 1.14 Patch and change management. In addition, the communication of the DNS server with other DNS servers and clients should be restricted to a minimum using packet filter rules (S 4.98 Restricting communication to a minimum with packet filters). In order to guarantee smooth operation and to detect any malfunctions or anomalies, a DNS server should be monitored continuously (see S 4.354 Monitoring of a DNS server).
Manual modifications to the configuration and/or to the DNS information should only be carried out after the domain information has been backed up in order to be able to restore it in the event of an error, see S 4.78 Careful modifications of configurations.
Disposal
If DNS servers are taken out of operation, they should be properly disposed of (see S 2.453 Withdrawal from operation of DNS servers).
Contingency Planning
Within the framework of contingency planning, business continuity plans should be drawn up for the relevant threat scenarios (see S 6.139 Creation of a business continuity plan for DNS servers). Since DNS provides a basic functionality for communications via networks, consideration should be given to keeping suitable redundancy systems available.
Planning and design
| S 2.298 | (B) | Administration of Internet domain names |
| S 2.450 | (W) | Introduction to DNS basics |
| S 2.451 | (A) | Planning the use of DNS |
Purchasing
| S 2.176 | (Z) | Selection of a suitable Internet service provider |
| S 2.452 | (C) | Selection of a suitable DNS server product |
Implementation
| S 2.32 | (Z) | Establishment of a restricted user environment |
| S 2.46 | (A) | Appropriate key management |
| S 3.73 | (A) | Training the administrators of a DNS server |
| S 4.95 | (A) | Minimal operating system |
| S 4.97 | (Z) | One service per server |
| S 4.98 | (A) | Restricting communication to a minimum with packet filters |
| S 4.198 | (Z) | Installation of an application in a chroot cage |
| S 4.350 | (A) | Secure basic configuration of a DNS server |
| S 4.351 | (B) | Secure zone transfers |
| S 4.352 | (B) | Secure dynamic DNS updates |
| S 4.353 | (Z) | Use of DNSSEC |
Operation
| S 2.8 | (A) | Assignment of access rights |
| S 2.35 | (B) | Obtaining information on security weaknesses of the system |
| S 2.273 | (A) | Prompt installation of security-relevant patches and updates |
| S 4.78 | (A) | Careful modifications of configurations |
| S 4.354 | (B) | Monitoring of a DNS server |
| S 5.118 | (Z) | Integration of a DNS server into a security gateway |
Disposal
| S 2.453 | (C) | Withdrawal from operation of DNS servers |
Contingency Planning
| S 6.139 | (A) | Creation of a business continuity plan for DNS servers |

